
Did you know that you can to link to a specific Tweet on Twitter? The URL looks like this: https://twitter.com/#!/edent/status/197967209459499008 Pretty obviously, that's the user's name and the ID of their tweet. Simple, right? Not really, click on that link and you'll see this: That's my name in the URL bar - but the Number 10 Press Office's tweet on the page. What's Going On? Have I retweeted that status? Nope! Am I a 1337 h4x0r who has hacked Number 10? No sir! Is the screenshot a…
Continue reading →
We live in a world of our own creation. This means we can find it inconceivable that outsiders don't know the acronyms we use daily. How can anyone possibly live without understanding what we do? Customers don't understand your company's acronyms, processes, or business model. It's worse than that, though - most users don't even recognise your company's name! Here's a great example. In Zinio's world, everyone knows who Zinio are. They live in Zinio town, drink Zinio coffee from the Zinio…
Continue reading →

Bitcoin me! 1LJmePYmet9VjpeAqqLbd0RVGoYcLqAZhk If that "sentence" makes any sense to you - you're not a muggle. Muggles (for want of a better epithet) don't want to invest a lot of time into things which don't fit with their mental model of how the world works. Without getting into a philosophical discussion on what money is and how value is generated - let's look at how Bitcoin works in practice. Failing to Design is Designing to Fail Bitcoin is doomed to fail. Pick a reason why. …
Continue reading →

One of the most influential books I have ever read is Donald Norman's "The Design of Everyday Things". In the book, Norman rails against the usability flaws which seek to undermine our comfort and sanity. Everything from lightswitches which never seem to have a consistent state, to to alarm clocks with impossible to figure out controls. It really is a must read for anyone who cares about usability - on computers or in the real world. I travel a lot for business - and occasionally for…
Continue reading →
Google has rightly received praise for its reworked "Contacts" functionality. But there is still a rather glaring error. One of the things I love to do is add images to my contacts. It gives me a visual cue when I'm scrolling through looking for a person, it prompts my memory when I see the face of a friend calling me, and it helps me remember what people look like. As you can see, I'm pretty good at keeping everyone's photo on my phone up to date. Which Conditions Are Appropriate? …
Continue reading →

This morning, when I logged on to Twitter, I saw a user who I didn't recognise tweeting away in my timeline. I wracked my brains thinking about how they could have gotten in there before I realised it was a long-dormant friend who had changed their name and avatar. But, in thinking about how a spammer could infiltrate one's timeline, I think I came up with a fairly bullet-proof method to spam Twitter users. I present this as an exercise in devious thinking - and also to show how our…
Continue reading →

What is "Implicit Knowledge"? Essentially it's stuff that everyone knows, but no one has written down. Usually it's something that people have worked out through their own experiences. This sort of knowledge is common in life - but is fatal in computing and design. Take the following tweet I received. Mark Hawkins @Mawkins Replying to @edent …
Continue reading →

There are many "rules" when it comes to User Interface / User Experience design. One that I try to stick to is "Don't let users do things they can't do." It's one of my gripes with Linux. If you're editing a configuration file, you are relying on yourself to sanity check your input - often without knowing what the limits are. Take these two different examples. In a text file, we might have: #Maximum Widgets to fidget maxW_to-F = 0 Whereas a GUI would show How many Widgets do you want t…
Continue reading →

I'm a big fan of OAuth - despite some claims to the contrary. It's an excellent way of teaching people not to stick their username and password into any old site which asks for it. Which is why I'm so incredibly disappointed in Twitter's implementation of mobile OAuth. For a service which started out operating by SMS, Twitter takes a surprisingly unenlightened view of mobile. It's main mobile service - http://m.twitter.com/ - is almost completely devoid of useful features. That's one of…
Continue reading →
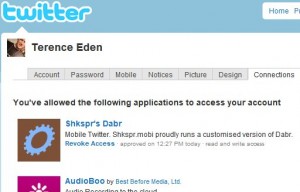
Twitter has a gaping security hole. Changing your password won't stop malicious users logging in as you! I received a rather worrying email from Twitter. Apparently they thought my password had been compromised and needed to be reset. Reset Your Twitter Password After checking to see if it was valid, I went and changed my password. Any site which relied on a cookie to post to Twitter would have been blocked out. Ha! Gotcha, suckers! The OAuth Problem OAuth tokens are not revoked when th…
Continue reading →

One of the things I love about Private Eye is the columns I don't read. Corners of the magazine dedicated to the gossip of the classical music world, the perils of modern architecture, positively incomprehensible reports about big business buying into football. I care for none of these subjects, but I'm immensely relieved that they are reported on somewhere. The Guardian's Saturday edition strikes me as a long form version of Private Eye, but written by those who would never use a sentence w…
Continue reading →

I know a thing or two about mobile websites. The last 4 years of my life have been spent obsessing over them. I wouldn't claim that the sites I run are the best in the world - but I've picked up a thing or two about how a successful mobile retail channel should work. Nokia's Ovi gets everything wrong. I'm going to show you 25 easily avoidable mistakes in the new Ovi Store. Here's how to make a successful downloads platform: Make it easy for your customers to buy things. ...er.... …
Continue reading →











