
Everyone loves Dark Mode. It is kinder on the eyes, less energy intensive, and looks hecking cool. *5 seconds later* We regret to inform you that Dark Mode causes security bugs. (With apologies to Ben Ward) OK, OK. This isn't a particularly severe security bug, but I found it interesting. The Matrix messaging app "Element" […]
Continue reading →

You receive a call on your phone. The polite call centre worker on the line asks for you by name, and gives the name of your bank. They say they're calling from your bank's fraud department. "Yeah, right!" You think. Obvious scam, isn't it? You tell the caller to do unmentionable things to a goat. […]
Continue reading →

It is tempting to think that users are to blame for their own misfortune. If only they'd had a stronger password! If only they didn't re-use credentials! If only they had perfect OpSec! If only...! Yes, users should probably take better care of their digital credentials and bury them in a digital vault. But there […]
Continue reading →

It's never great to find out you're wrong, but that's how learning and personal growth happens. HTTP Message Signatures are hard1. There are lots of complex parts and getting any aspect wrong means certain death2. In a previous post, I wrote A simple(ish) guide to verifying HTTP Message Signatures in PHP. It turns out that […]
Continue reading →
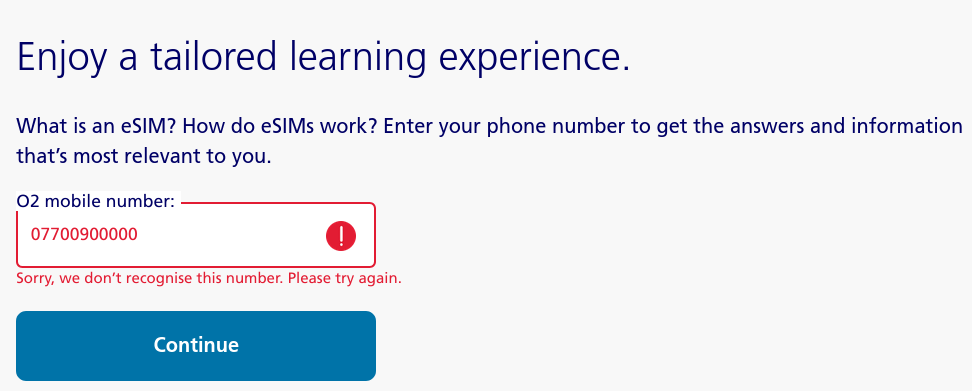
It's always fun keeping your network inspector tab open. While looking around the O2 UK website, I found this page all about eSIMs. For some reason, it wants to know the user's phone number. I put in a random number, and it refused to let me in. Putting in a genuine O2 number let me […]
Continue reading →

I'm trying to get my head round HTTP Signatures as they're used extensively in the Fediverse. Conceptually, they're relatively straightforward. You send me a normal HTTP request. For example, you want to POST something to https://example.com/data You send me these headers: POST /data Host: example.com Date: Sat, 24 Feb 2024 14:43:48 GMT Accept-Encoding: gzip Digest: […]
Continue reading →

You type in to your browser's address bar example.com and it automatically redirects you to the https:// version. How does your browser know that it needed to request the more secure version of a website? The answer is... A big list. The HTTP Strict Transport Security (HSTS) list is a list of domain names which […]
Continue reading →

I've responsibly disclosed a small security issue with Mastodon (GHSA-8982-p7pm-7mqw). It allows a sufficiently determined attacker to use any Mastodon instance to redirect unwary users to a malicious site. What do you think happens if you visit: https://mastodon.social/@PasswordReset/111285045683598517/admin? If you aren't logged in to that instance, it will redirect you to a 3rd party site. […]
Continue reading →

Quite often websites will encourage you to copy and paste commands into your terminal. There are a variety of reasons why this is bad - not least because someone could hide malicious code. That's usually done with a bit of CSS to make the evil command invisible, or using Javascript to inject something unwanted into […]
Continue reading →

The other day, my HP M140w printer stopped working. The day before, it printed fine. This time, nothing. I rebooted, reset, updated, and performed all the modern rituals associated with uncooperative hardware. I logged into to the printer's webserver and clicked around the admin panel. On one page, I found an error message. So, like […]
Continue reading →









