Responsible Disclosure: SVG injection in Three.co.uk
Here's a quick write-up of a minor XSS (Cross Site Scripting) vulnerability on the website of Three.co.uk - one of the UK's mobile providers.
A brief recap... Most websites have a search function. If you search for something which cannot be found, the site will often say "No results found for XYZ."

If we can convince the search engine to spit out HTML, we can inject malicious content into the page.
This is usually done by searching for something like <script>alert("h4X0r");</script>
Three's website detects script elements as hostile and refuses to serve them back.

But, curiously, it does allow some HTML elements through. The <u> underline element, for example.

It wouldn't allow <img> or <video> or most other troublesome content. But I was surprised to see it let through SVG (Scalable Vector Graphics). This means some minor naughtiness can be had!
Doing a search for
<svg xmlns="http://www.w3.org/2000/svg" viewBox="0 0 128 128" width="128px"><circle cx="64" cy="64" fill="#006add" r="64"/>Results in a big blue circle being drawn on the page.  ...and that's when I stopped and tried to find someone to report it to!
...and that's when I stopped and tried to find someone to report it to!
Why is this a problem?
Drawing a circle is not malicious. But SVGs are complex. They can store intricate graphics.
Because the search parameter is sent in the URL - http://www.three.co.uk/Search/?q=<svg... - it would be easy for a spammer to send a message saying "Click here for great deals on Three!!!" and then use the SVG to draw a graphic encouraging the hapless user to visit a malicious site.
Or they could create a form to phish users' details. Or... Well, use your imagination.
Reporting it to Three
*sigh* Three don't publish any security contact details. Nor do they participate in any bug bounties that I could find.
I reached out to my friends in the mobile industry - because I didn't have much faith in reporting it via Twitter...




Eventually a friend of a friend sent me a security email address which Three do not publicise. I fired off a quick disclosure and was pleasantly surprised at how seriously they took the issue.
Timeline
- 2019-08-22 - Discovered and disclosed. Got a reply in under an hour that it was being looked at and that a 90 day disclosure was fine.
- 2019-09-20 - Three informed me the issue was fixed, which I verified. They offered to send me a token of their appreciation in lieu of a formal bug bounty.
- 2019-09-22 - Bug Bounty delivered!
 Big ol' box of chocolates!
Big ol' box of chocolates!
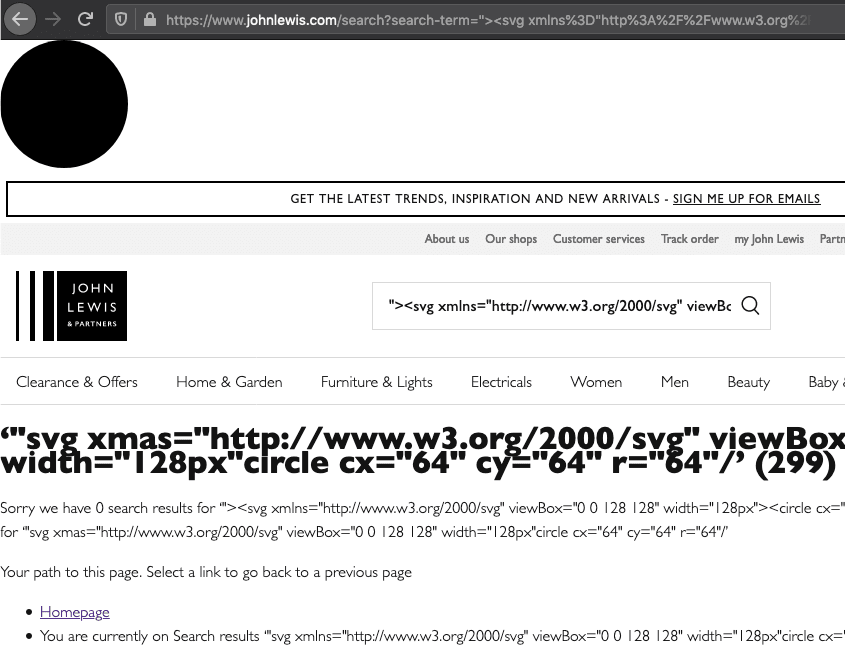 Responsible Disclosure - John Lewis
Responsible Disclosure - John Lewis What's the most malicious thing you can do with an injected HTML heading element?
What's the most malicious thing you can do with an injected HTML heading element?
Neil says:
Great! But what are they doing about the non-publicised security contact address?
I'm pleased you got your chocolates, but it made me realise that I've never had a similar bounty when I've reported issues that are /not/ IT-security related.
I've told various organisations that their websites have broken links or outdated content; that their street cabinets are open; their unoccupied premises insecure; that their shopping trolleys are abandoned in neighbouring streets; and many similar things.
I've been thanked, surely, but chocolates, vouchers, swag or cash? No.
A good deed is its own reward... 😀
But chocolate helps.
It’s kinda ironic that your code snipped exposed missing sanitation and escaping in my RSS aggregator and reader. Reported upstream xD