Twenty One. I have 21 accounts which use Two-Factor Authentication. I use the Authy app to manage them all, but it is still a pain to scroll through and find the exact 2FA token I need.
Encouraged by my friend Tom Morris's blog post, I picked up a YubiKey NEO for £50. It implements the FIDO U2F standard.
Sadly, the YubiKey is substandard and frustrating to use. Here's what I found.

First impressions count for a lot - and it is pretty disappointing. What you see in my fingers is literally all Amazon sent me. A fob and a bit of card. No instructions, no welcome pack, no getting started guide. What does the circle do? How do I use it with Android?
The plastic is cheap and doesn't look like it would survive in a pocket full of keys. In short, it looks like a freebie USB stick - not an expensive piece of security hardware.
OK, let's get started!
Linux Set Up
Do I need to do anything special to get it working on Ubuntu? Who knows - the Yubico pages literally just point to StackOverflow.
A quick lsusb shows ID 1050:0116 Yubico.com Yubikey NEO(-N) OTP+U2F+CCID - so it seems to be detected correctly. So that should be fine, right?
When I push the button on the YubiKey, it spits out a 44 character password - all lower case characters. It's the same every time. Shouldn't this be unique, like a normal one-time code?
Firefox Woes
Fine, let's follow the steps needed to set up Facebook with a security key.

Ah... Turns out that U2F support will be coming to Firefox in Version 57 which is scheduled for release in mid-November.
Chrome Test
OK, let's switch my browser to Chrome temporarily. That Firefox page alerted me to Yubico's demo server at https://demo.yubico.com/ (which isn't linked from anywhere on their main site). With that I was able to confirm that the key worked. I guess. I touched the button on the key, it autotyped the password and I was logged in. Yay?
I don't really understand what I did or why it worked.
GitHub
The GitHub help pages give a range of scary warnings about setting up 2FA.
There are 12 steps to setting up a U2F. Step one is setting up 2FA via an app - which is a 10 step process.
The short version is:
- Go to https://github.com/settings/two_factor_authentication/configure
- Give the key a name.
- Press the button on the key.
That's it! Pretty simple.
After logging in with a username and password, you get this screen:

I pressed the button and IT WORKED!
Android
OK, so this key has NFC and therefore should work with Android. But how? There's nothing on the Yubico website.
I held the Neo against my phone, and it popped open the default web browser.
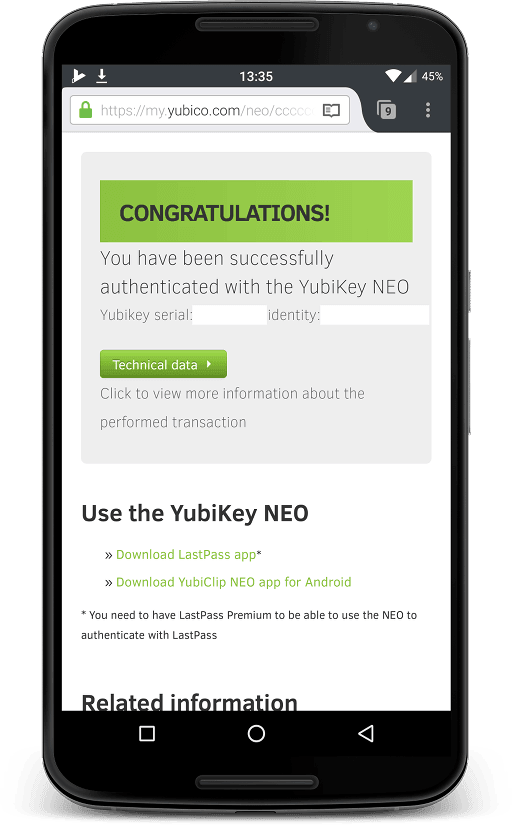
I don't understand what this screen is telling me. Apparently I have been "successfully authenticated" - but with what? I haven't typed in a password or given a user name.
That serial and identity - should I keep them safe? Private? Are they dangerous if they get leaked? Do I need them backed up?
Oh, great, yet another app I have to install, configure, and update.
The app
The app is also substandard. The Android version only supports American and German keyboards.

The company encourages you to contribute new layouts to their open source project. But it, like the app, hasn't been updated since 2015!
Back to GitHub
So I tried GitHub via the Chrome browser on Android.
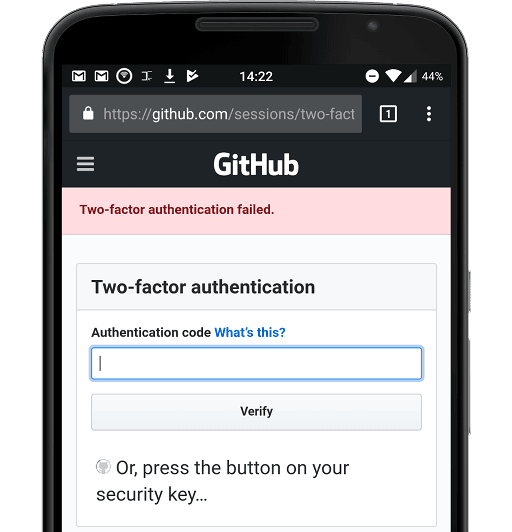
Nope. Just wouldn't work. I held the key to the phone, the app copied the 44 character password, I manually pasted it in. And I got this error, repeatedly. My 2FA codes from Authy worked fine.
I don't know how to fix that.
The other app
There is another app! It isn't linked to from the default page you get when you hold the Neo against the phone. That would be too easy, apparently. After clicking around on the Google Play store, I found Yubico Authenticator
Yubico Authenticator allows you to use a YubiKey NEO to store OATH credentials (TOTP and HOTP supported, as used by Google, Microsoft, Dropbox, Amazon and many more) used for 2-factor authentication.
Aha! I think this is what I need. And it has been updated recently. Well, May 2017.
Again, it is as ugly as the last app. Compare it to Authy which uses icons to help you find the code you need, strong colours to remind you which service you're using, and large numbers to help when copy-typing.

Which of those apps would you rather use every day?
There's no way to copy credentials from another service - so I had to manually set up all 21 accounts again. That was a fun way to spend an afternoon.
- Scan the QR code of the service.
- Give it a memorable name.
- Tap the YubiKey to your phone to store the token.
- Repeat.
To get tokens out:
- Tap the YubiKey to the phone.
- The Authenticator opens up.
- Scroll to find your code (hard without icons or colours as a guide).
- Tap a tiny square to copy the code.
- Swap back to your app and paste it in.
Honestly, I thought I'd be at the login screen of the app, then just have to tap the YubiKey to the phone and have it do it automatically.
Why did I think that? Because that's what the website promises!
LastPass
I use LastPass to manage all my passwords. If I want to use U2F with it, I need to pay them $2 a month for their premium product. LastPass is the only company I'm aware of who charge extra to enable security features.
But I can still use the YubiKey code generator app. Just not the key itself...?
I AM SO CONFUSED!
PGP
I'm one of those daft people with a PGP key in active use. I set it up four years ago as a 4096 bit RSA key. This fifty-quid hunk-of-junk can only handle 2048 bit keys, like it is from the stone age. Why? Who knows.
If you can be bothered, you can generate yet another PGP key and store it on the device. There are no official apps to do this on Android, so you'll need to find yet another third party app to trust. I used OpenKeyChain.
Of course, if you lose the physical hardware you lose the key. There's no obvious way to extract the private key from the YubiKey. I mean, there may be a way - but good luck finding clear documentation.
What's the point?
I get security. I understand the benefits of 2FA. But I struggle with the YubiKey. It's a pain to set up and a pain to use. The apps are outdated, ugly, and underwhelming.
I had thought that this would be a "single use" solution - but it isn't. On a laptop I have to plug it in and touch the button, on Android I have to use NFC to open the app, find the right account, tap to copy, then paste the code manually.
There's no step-by-step guide for new users. It's all trial and error.
For fifty quid, I could buy a cheap Android phone and use Authy for free.
The kicker? When it is plugged into a laptop, a green LED flashes constantly. Urgh.
If you want normal people to adopt security best practices, the experiences need to be easy to use and beautiful. The YubiKey is hard and ugly. Which is a great shame.
12 thoughts on “A grumpy look at using a Yubico Neo NFC on Ubuntu & Android”
Marcus Downing
I'm currently trying to set up 2FA full disk encryption using Yubikeys and LUKS. Having bought a blue Yubikey, and done a lot of reading and experimentation, I finally discover that the blue version only supports U2F, not OTP as required by
yubikey-luks. It would have been good to know that before spending money. In theory the information was available in advance, but it really wasn't very easy to find.Here's a bit more thorough version of the comments I made on Twitter.
There are a few misunderstandings in this post, which perhaps stem from poor documentation on Yubico’s behalf.
The NEO has a few default modes (OTP, U2F) and then programmable modes through a JavaCard interface (e.g. PGP).
One of these modes (Yubico OTP), which is what you encountered with the 44 character code, does actually generate unique codes. It's a bit deceiving because the first 12 chars aren’t as they ID your key. The remaining 32 characters are cryptographically signed counters that protect against replay attacks. Yubico have information on how this mode works at https://developers.yubico.com/OTP/OTPs_Explained.html It’s a completely proprietary 2FA method that relies on asking Yubico’s server (or an external server that has a copy of the Yubikey's crypto keys) if a key is valid.
You can also use TOTP with a Yubikey but it's a bit tricky because it doesn’t have a clock/battery. TOTP relies on using the current timestamp to generate a code, so you need a helper app to supply current time to the Yubikey.
U2F solves these two pain points (plus phishing) by having all the comms built into the browser, but support is very new and scarce. Hopefully it will grow in popularity and eliminate some of this complexity.
It’s definitely way more durable than you’d think (I carry my Yubikey on my keys) and it's highly configurable (so the persistent LED + modes you don’t use can be disabled). https://www.yubico.com/products/services-software/personalization-tools/use/
I guess this is why they point to the no-frills U2F only key? Everything is self-configured with U2F so you don't have to worry about any of these different modes/settings/helper apps.
@edent
Good to know it is more durable. Your comment is the first time I've heard about the Linux configuration tool - that would have been a helpful thing to have in an onboarding process.
Morgan Percy
It looks like you would benefit greatly from reading the Yubikey manual, which explains the OTP authentication process.
The Yubikey works very well at what it does. I have been using mine for OTPs, OATH, U2F, and PGP for about 3 years. It seems that the issue here is that you purchased something you don't understand. I hardly see how that is Yubico's fault...
@edent
Hi Morgan. As I said in the 4th paragraph, the Yubikey doesn't come with a manual. At the time I wrote this blog post, the website was a mess of contradictory information. I purchased it thinking I could authenticate by tapping it against my phone - as their advert promised. I hardly see how that is my fault...
Darren
Hi,
I also had trouble with the Yubikey Neo but I got one-touch 2FA working by doing this:
1) Register key for 2FA in GitHub (I don't have Facebook but I assume it's the same) 2) Install Google Authenticator on your phone - it wouldn't work without this 3) Open GitHub in Chrome (mobile), enter username and password 4) When prompted, wave the Neo over the back of the phone 20 or 30 times
I had trouble getting the phone to detect the Neo, probably due to my massive phone case - but it does work with just a tap. The first time I got sent to the same yubico page as you did, but I closed this without installing any apps and NFC is working fine.
Perttu
You are right that the documentation options are quite confusing. This is simply because the focus of these companies is enterprise customers that buy hundreds or thousands of tokens, not consumers.
For mobile use on Android, for some mystical reason, Google decided to include the U2F support through Google Authenticator and not Chrome directly. This threw me off for a bit, but since everything works well with mobile.
The fact that you cannot extract the private key is by design, this is exactly why I have used Yubikey (Neo) and Feitian (ePass) tokens for SSH authentication. The private key should be generated on the device and never extracted, only that way you can be sure that the authentication done with that private key requires the physical token.
Feitian tokens are by the way much cheaper, you can get one for 15€, and they are now also used by Google (Titan Security Key).
Here are few articles which helped me get started with the SSH: https://lauri.xn--vsandi-pxa.com/2017/03/yubikey-for-ssh-auth.html https://www.esev.com/blog/post/2015-01-pgp-ssh-key-on-yubikey-neo/ https://www.rcdevs.com/docs/howtos/epass/epass/
Ben in Seattle
This is exactly the kind of review I want to read for any device I'm thinking about buying! Grumpy, yes, but with reason. It explains clearly what the expectations were and how the Yubikey (and Yubico app) failed. If Yubico wants to do better, this review gives them the roadmap.
I hope we will see another device review now that the NFC FIDO2 authenticator from SoloKeys.com is a reality. Like many kickstarters, it delivered late. But, if the blog is to be believed, in this case it was because SoloKeys were taking the time to get things right.
I'm curious if they did get it right. Can a small project that is aimed at individual users -- not huge, institution-wide deployments -- make @edent less grumpy?
AndyOxon
I recently purchased a Yubico 5 series key. And, it does what it says on-the-tin!
When it comes to configuration, usually the steps are provided by the service with whom you have the account, and are as simple as plug & touch. Otherwise, Yubico does have the information and tool(s) you might need… it’s just a case of finding them, and not getting it confused with old/irrelevant information.
What should have been a straightforward process to setup smart card logon with my Windows domain turned into a mission, ending in the requirement of Yubico’s PIV tool instead of Yubico’s mini-driver. A clean-up of their webpages would greatly help those searching for solutions. I understand Windows Hello makes the consumer experience much more streamlined.
I haven’t tried associating my key with any of my linux VM boxes, yet.
On Android, the Yubico authenticator feels obsolete, and the YubiClip app didn’t appear to work for me. But since the mobile device has its own key (for any authenticator app etc) then I would only find my Yubico NFC key useful for device boot/logon, any web account authentication (FIDO2) and, domain VPN authentication. None of these options (so far as I’m aware) are currently open on Android. Yubico cannot be accountable for slacking developers now, can they? Lol
Despite the fact that these keys are NOT 100% secure, I intend to buy my entire family one for Christmas because they (can) dramatically increase your overall security. Just don’t loose your key, or be sure to have a backup!
To confuse matters further, many FIDO keys can function in both U2F and FIDO2 mode with each method producing a different type of seed on the server.
That said the registration process itself is still fairly straightforward, and there is currently an uptake in interest in FIDO keys (google, microsoft, etc).
Personally I believe the longer term issue is not with the technology itself, or even the documentation, but using a USB based authentication device (and with the security concerns that USB devices bring with them).
Even in 2021 security is something for experts with console commands and UIs that look like back in 2010 – security doesn’t need a fancy looking UI.
Nevertheless integration could be a bit better be it login in to *nix systems that requires a bit of fiddling depending on init-system and authentication. On Windows a Yubikey logs in without any password if the group policy doesn’t disable this which requires admin powers. And most consumer devices simply start as desktop.
Sure you need to first pick your Yubikey with a bit of expertise then set up the slots according to your needs e.g. slot #1 left as Fido/U2F and second as Authenticator/HMAC-secret. Finally recent Yubikeys come with flexible Smartcard key slots, too supporting elliptic curves.
I do not log in to my desktop with my Yubikey but use it as Smartcard to encrypt and sign mails – configuration through GPG command line. And it serves as U2F with slot #1 and with its HMAC as 2nd factor for keystores and Authenticator-replacement Yubico Authenticator: https://www.yubico.com/products/services-software/download/yubico-authenticator/.
And maybe think about your lost or stolen smartphone giving access to anything through its apps.
Trackbacks and Pingbacks
[…] all the time. I need to buy one and try it, but it could be the easiest way to secure things. Terence had exactly the same problem with authy but found the actual implementation of Yubikey to be pretty […]
What links here from around this blog?