Responsible Disclosure: Content Injection flaw in Gett's Website
Bit of a boring write-up, but here we go.
Taxi app Gett had a content injection flaw in its search function. By searching for an HTML string, it was possible for an attacker to add links or images to a page. It was really hard to contact them - but the threat of media attention sprung them into action.
For example, searching for a specially crafted string meant that an arbitrary SVG could be drawn onto the page like this: 
Or just a regular <img> element: 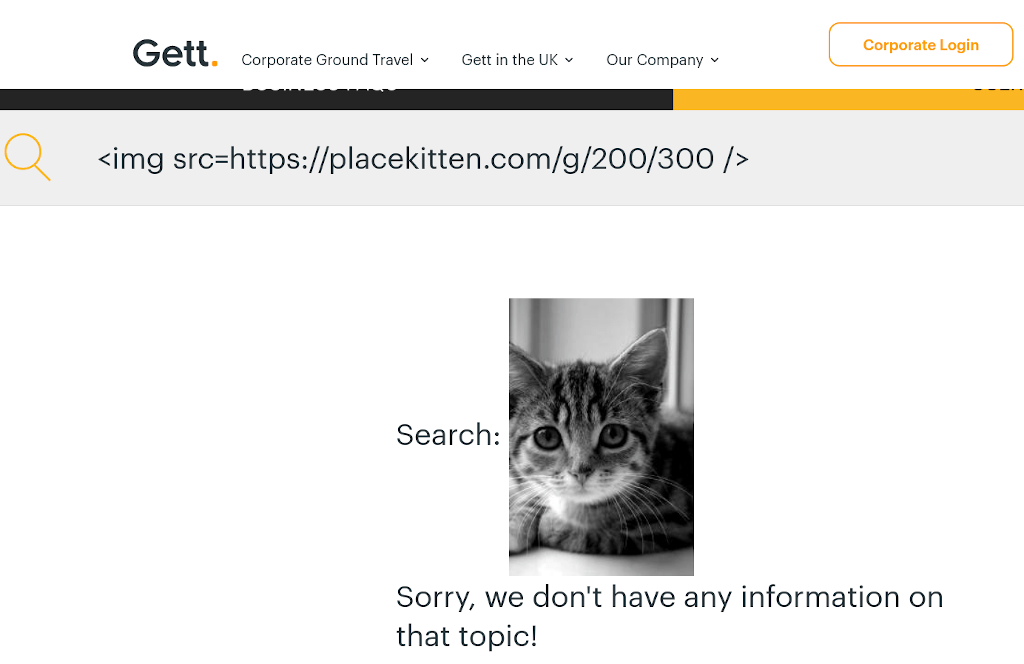
Links could also be added - like this: 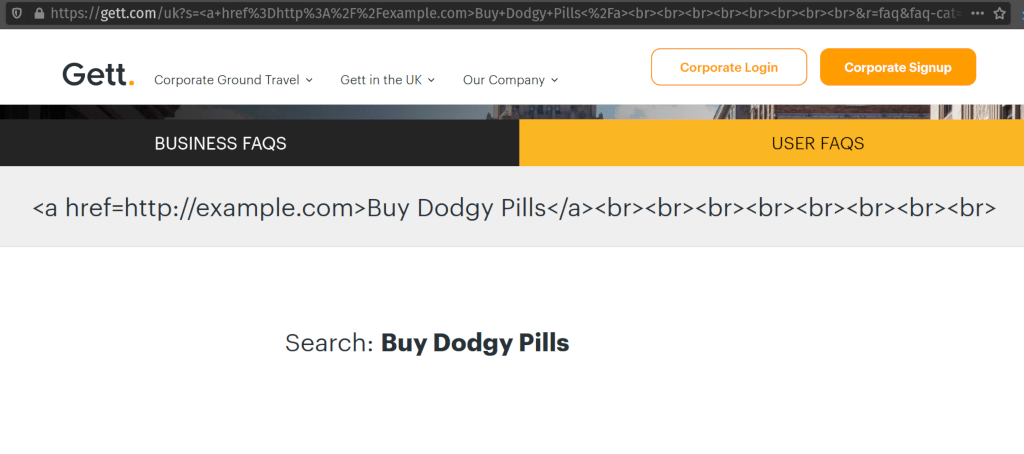 That would have allowed an attacker to bypass email spam filters, by sending links which apparently went to a trusted site. It's also useful for search engine poisoning.
That would have allowed an attacker to bypass email spam filters, by sending links which apparently went to a trusted site. It's also useful for search engine poisoning.
Similarly, the entire page could have been rewritten if the attacker crafted the right sort of HTML and CSS.
Luckily, the form rejected and <script> and <iframe> tags, so an attacker couldn't have run malicious code.
But it would have been possible to craft a page like this to harvest people's payment details:  That form can POST data to any external website.
That form can POST data to any external website.
This was an unusual find, because Gett are running a updated WordPress site. I can only assume their custom theme caused this flaw.
Timeline
Gett don't have a security.txt file, or an obvious bug bounty. So I resorted to my tried-and-true tactic of finding an employee on LinkedIn and trying to connect with them.
- 2021-04-16 Discovered, validated, and immediately contacted Gett via LinkedIn, email, and Twitter. No response.
- 2021-04-17 Contacted a few random employees on Twitter to see if they knew of a security contact. No response.
- 2021-04-20 A friend-of-a-friend got me in touch with the CEO. I explained the issue as best I could. No response.
- 2021-04-21 Tried contacting customer service again. No response.
- 2021-04-26 Contacted a security journalist who then contacted Gett's PR team. A couple of hours later I had a response from the Gett Security team. Funny that! I disclosed all my findings and asked for a 30 day publication window.
- 2021-04-27 Validated as fixed. I was offered a $100 gift card in return for not publishing this post. I respectfully declined.
Sign Up Bonus!
As there was no formal bug bounty, I'm making my own one! Visit b.gett.com/icuk?coupon=GTPAQYZ on your mobile and we both get a discount on our next few taxi rides with Gett.