This is part 4 of a series of blog posts looking at the security of the UK Government's web infrastructure.
Over the last few days, I've shown that hundreds of websites run by branches of the UK state are in a perilous state of disrepair. There are multiple sites with hugely embarrassing XSS flaws, running ancient and unsecured software, languishing unmaintained and long since abandoned.
What are the consequences of failing to invest in security and maintenance? The websites become a haven for cyber-criminals. They exploit weaknesses in the sites and use them to push dodgy pills, fake goods, and all manner of illicit schemes.
The exploits which we are about to see range from the trivial - comment spam - to the extremely serious - complete site takeovers.
All the sites mentioned in this blog were notified on 19th February about the specific flaws found. I've no idea how these sites were compromised, nor whether any citizens' data are at risk. All I know is that a disastrous attitude to "cyber security" is rotting away within the *.gov.uk namespace.
Complete Site Takeover
This looks like the perfect site to by some "Genuine* Fashionable Boots", doesn't it?
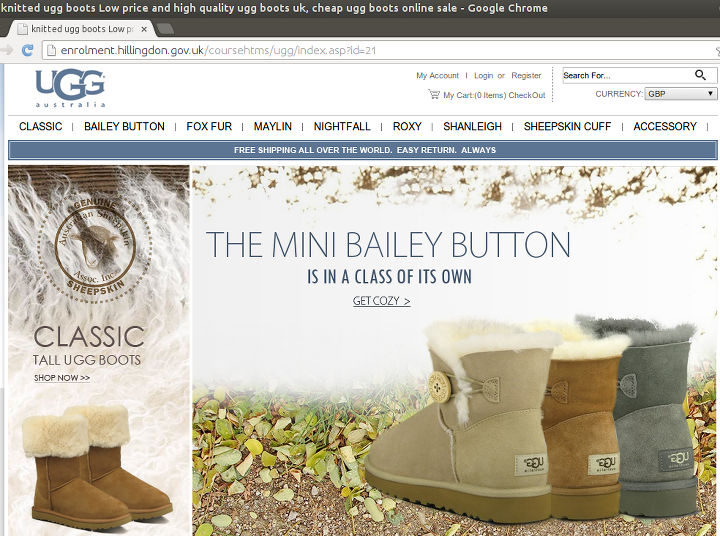 It is seemingly hosted with the endorsement of the Conservative run London Borough of Hillingdon. One of the most prosperous borough in London, and they can't even afford to hire a website security team.
It is seemingly hosted with the endorsement of the Conservative run London Borough of Hillingdon. One of the most prosperous borough in London, and they can't even afford to hire a website security team.
—❦—
The Leadership Centre is funded by the government department for Communities and Local Government. Its mission?
We believe it takes great leadership to create thriving and prosperous communities so we work with and support senior leaders from across the public sector to help them shift their thinking on leadership.
Sadly, that doesn't extend to thinking about leading technology teams. The site has been abandoned for around the last 3 years. In that time, it has become riddled with spam.

—❦—
At the other end of the spectrum, we have the tiny borough of Amble. With a population of barely 6,000, their website plays host to a number of webpages extolling the virtue of knock-off boots.

—❦—
The town of Kidwelly is nearly 900 years old. It has a rich history including medieval castles, nature reserves, and an annual festival.
As far as Google is concerned, it also maintains a cottage industry for cut-price "blue pills".

Having spoken to the council, they have told me that the local police are currently dealing with the matter.
—❦—
Can we reasonably expect small parish councils under the yoke of austerity to have top-notch web security teams? If they are able to find the resources necessary to fund the protection of their digital assets, that's great - but it's highly unlikely.
Instead, Central Government needs to heavily invest in making sure that all councils - big and small - are able to competently run web sites and services.
Comment Spam
Every blog attracts comment spam. Fraudsters leaving vaguely plausible comments in the hope that publication will see a flurry of extra hits on their site. The bigger and more prestigious the site, the more likely the site is to be targeted. And the .gov.uk name is very prestigious.
Amongst the Government sites playing host to spam is the Foreign and Commonwealth Office's blog page for the British Ambassador to Somalia.
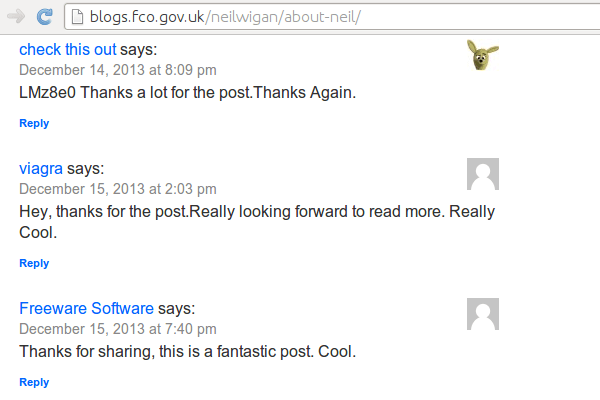
—❦—
The Northern Ireland Assembly is the devolved legislature for Northern Ireland. It has hundreds of comments, seemingly all of which promoting dodgy deals.
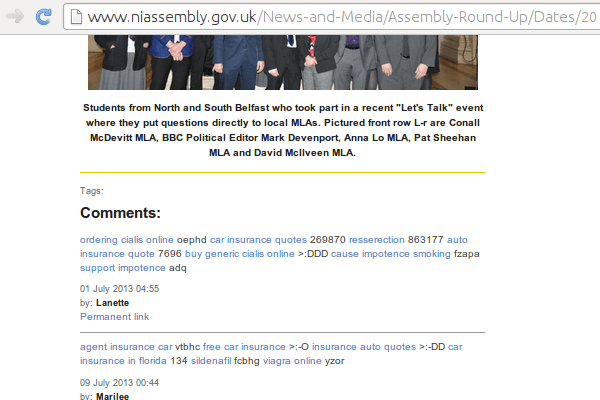
—❦—
A book of condolence in Oldham for a much loved community member now plays host to spammers.

—❦—
Lewes, and many other councils, have open forums which are overrun with spam messages.

—❦—
Even the UK National Archives have seen fit to save some comment spam for future generations to ponder.
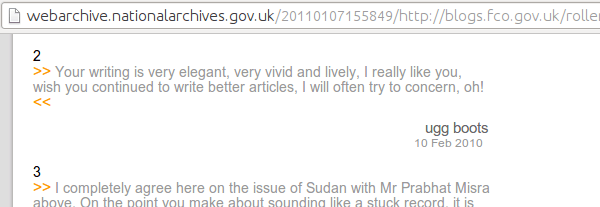
Hidden Links
Finally, we get to the murky world of hidden links. These are spamming messages not designed to be seen by humans. They are hidden within the web pages' source code in the hopes that Google and other search engines will see them and increase the spamming site's popularity.
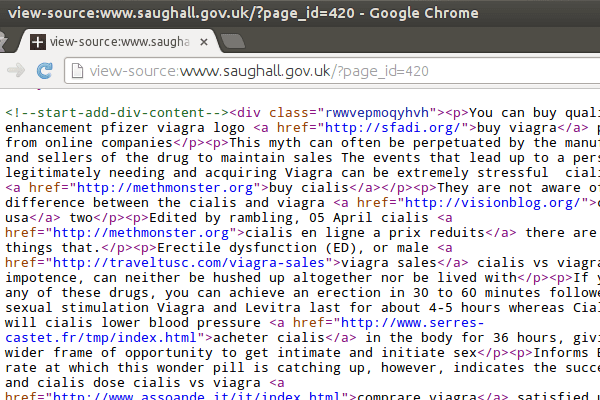
The spam covers the usual range from pharmaceuticals to knock off designer goods.
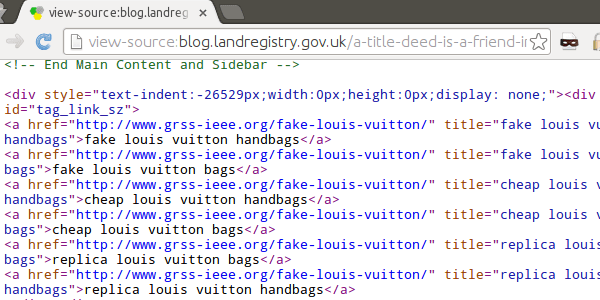
Again, there are several sites which exhibit this malicious behaviour.

What Can Be Done?
The State needs to take responsibility for the websites run in its name. If site owners are unable or unwilling, then those sites should be removed from the web. It is simply too dangerous to allow them to stay online without decent security measures in place.
It is time that the Government started to treat cyber-security as a serious subject. They love putting out press releases, and making grand sounding plans with shadowy agencies - what they need to do is spend some money on basic front-line services.
5 thoughts on “The Unsecured State Part 4 - UK Government Websites Spewing Spam”
So I am going to put on my Parish Councillor hat here and hopefully give a little insight. When the council of which I am a member were considering a new website they were offered a product from a private company who provided a bespoke proprietary system which would cost the council a little over £1400 a year to run and that did not include the initial configuration and setup fees. It would have been something like £3k in the first year and the £1.4k each year. Needless to say I knew that NO.10 were using WordPress and there was little reason not to use it in place of a private product. The reasoning was.
Now councils (especially parish) don’t all have IT departments. They either rely on the focus of well meaning volunteers or they buy in external help. The larger the council the bigger the administration the greater the likelihood of people being able to manage the websites. However a council is a pretty busy organisation and if you had to place website security in the queue of issues like Road Repair, Drain clearing, Town Management, Social Services and Community Care, Planning and development, salaries, payroll, daycare and events you will always find it near the bottom of the list.
So what this leads to is consultancies will step in and try to mitigate the risk and provide services. So when you look at the unsecured state the one aspect you have not been able to extract in the data of your presentation is ... who is actually hosting and being responsible for this .. contractually speaking. I think that would make an interesting answer as it will then lead to the question how much are we paying for these sites to begin with and what level of national organisation can be created to help monitor them.
It's not beyond the whit of our community, people like you and I Terence, to make a proposal to help manage and reduce these risks for our state.
One of the reasons I put my name on a ballot paper every election is because I believe that our Local democracy needs people like us with good core technical skills to represent ourselves on the council meetings to help reduce this management issue one site at a time.
Well when you have people selling stuff like Gov Rocket, a list of 10 or so websites with .gov somewhere in the domain name, that host comment sections, (with the intent that buyers will spam the comments section to get backlinks), it's no wonder that some .govs are filled with spam.
Heck, over 1250 people bought Gov Rocket...
I should check the sites mentioned in the "review copy" I have, and go see how much comment and trackback spam are on those sites...
Matt
Only when IT security is given the the same or better attention than say occupational health and safety will this kind of nonsense stop. What council would open a public park that was full of scammers trying to flog knock off tat?
I remember finding this sort of stuff 10 years ago, and still nothing has changed, crazy. Here's another one; "site:.nhs.uk ugg" in Google reveals >100k results:
https://www.google.co.uk/search?q=site:nhs.uk+ugg
Trackbacks and Pingbacks
[…] Every council needs to provide similar levels of accountability, service and accessibility, but not every council can provide that equally. Not every council can afford the standards that web users have grown to expect. Neither can they afford to build services that are as robust and secure as we deserve. […]
What links here from around this blog?