
Julien Savoie has written a brilliant post explaining how you can enable https on your intranet. This is useful for several reasons. It means your employees aren't constantly fighting browser warnings when trying to submit stuff internally. All your http traffic is encrypted. You don't need to install a self-generated root certificate on devices. Lovely! But there's a downside. Every TLS certificate created by Let's Encrypt is recorded in a Certificate Transparency log. These CT logs are…
Continue reading →
Chrome for Android had a flaw which let one tab draw over another - even if the tabs were on completely different domains. A determined attacker might have been able to abuse this to convince a user to download and installed a spoofed app. See Chrome Bug #1242315 for details. Demo Here's a video of me on one site (Twistory.ml) opening a link to Twitter in a new tab. Twitter's mobile site contains a Web Manifest which should prompt the user to install an app. Rather than displaying this…
Continue reading →
As part of my MSc, I have to take an online exam. Obviously, this means I am highly likely to cheat by looking up things on Wikipedia or by having a bit of paper with notes on it. EVIL! So, the exam body requires me to install ProctorU. It's a service which lets someone watch you through your laptop camera while you do the exam. Creepy, but I get it. They also want to see your screen to make sure you're not alt-tabbing. A bit grim, but I get it. They also want complete control over your…
Continue reading →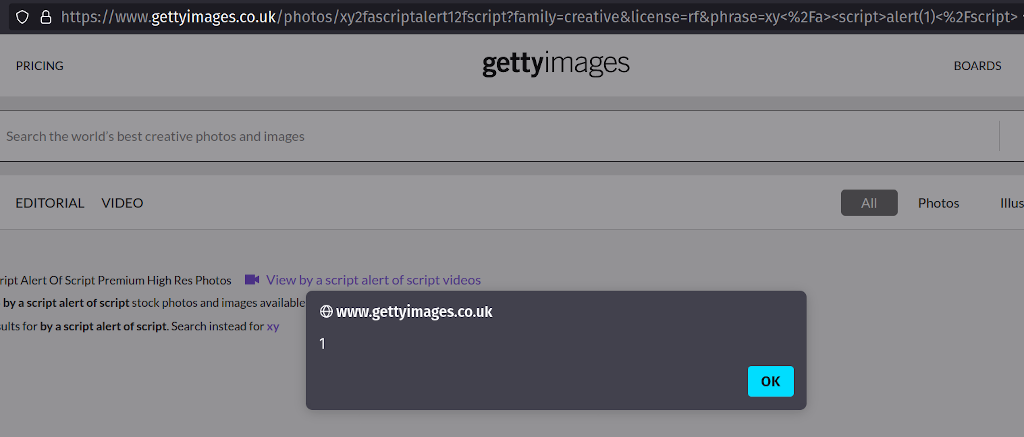
I've spent two months trying to report this issue to Getty images. They haven't responded to my emails, phone calls, Tweets, or LinkedIn messages. I've tried escalating through OpenBugBounty and HackerOne - but still no response. I've taken the decision to fully disclose this XSS because the Getty Images sites accept payments from users - and users need to be aware that the content they see on Getty Images sites may have been tampered with. This XSS was slightly unusual. When a user submits …
Continue reading →
In HTML, the autocomplete attribute is pretty handy. The HTML autocomplete attribute is available on <input> elements that take a text or numeric value as input, <textarea> elements, <select> elements, and <form> elements. autocomplete lets web developers specify what if any permission the user agent has to provide automated assistance in filling out form field values, as well as guidance to the browser as to the type of information expected in the field. …
Continue reading →
Legacy websites are a constant source of vulnerabilities. In a fit of excitement, a team commissions a service and then never bothers updating it. Quite often the original owners leave the business and there's no-one left who remembers that the service exists. So it sits there, vulnerable, for years. The [REDACTED] website had a subdomain which was running KANA's IQ software which was last updated in 2010. At least, that's judging by the fact it ran jQuery 1.4.4. Most routes into the site…
Continue reading →
Bit of a boring write-up, but here we go. Taxi app Gett had a content injection flaw in its search function. By searching for an HTML string, it was possible for an attacker to add links or images to a page. It was really hard to contact them - but the threat of media attention sprung them into action. For example, searching for a specially crafted string meant that an arbitrary SVG could be drawn onto the page like this: Or just a regular <img> element: Links could also be added - like …
Continue reading →
The UK faces an epidemic of telephone scams. Fraudsters are constantly calling people up pretending to be their bank. But how can you be sure the number displayed on your screen in genuine? You can't. The telecom system is hopelessly insecure and shouldn't be trusted for anything more complicated than dialling the speaking clock. Barclays bank knows that customers are worried about this. So they've produced a handy website where you can see if a telephone number belongs to Barclays. Because…
Continue reading →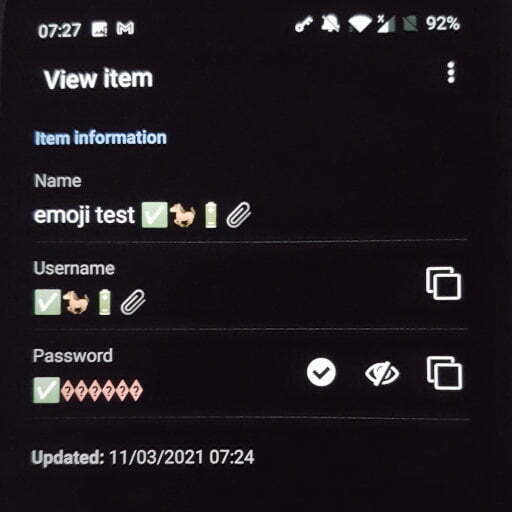
Let me start by saying that Emoji Passwords are probably a really daft idea. I want to use emoji in my passwords. They're easy to type on a mobile keyboard, easy to remember, and a lot more fun than boring ASCII characters. Let's go with ✅🐎🔋📎 (As close as possible to Correct Horse Battery Staple) I use BitWarden as my password manager. It saves emoji passwords into its database, but has trouble displaying them: Android Browser Plugin Linux App Bug Report I've raised this (minor) …
Continue reading →
Once in a while, big companies suggest that the answer to abuse is to ban anonymity and institute a Real Names policy. This time, it is Google's turn. They think that critical software should only be authored by people with "real names". I don't want to go into whether this is a good idea or not. Nor philosophical discussions of what a "real name" is. I want to discuss how this would work practically. Let's assume that a central website - like GitHub - decided to gather real names for…
Continue reading →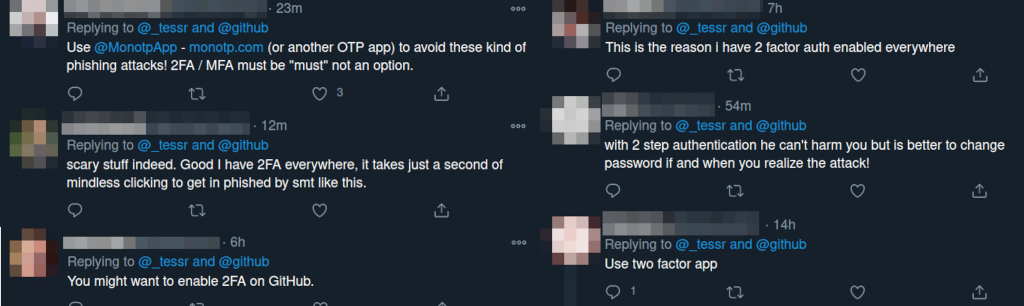
Another day, another high-profile website cloned to phish credentials. Tess Rinearson@_tessrIs this a phishing attempt? Goes to "githubverification.com" and asks for username and pw (if so, it nearly got me!) /cc @github pic.x.com/jgt4oNvjF2❤️ 2,243💬 111🔁 016:12 - Sat 16 January 2021 In the replies, you’ll see lots of techbros saying “this is why you should switch on 2FA people!!!” Except, and I hate to bring accuracy to a technical discussion, that’s not how 2FA works! A second factor all…
Continue reading →
(For the new reader, there is a famous essay called Falsehoods Programmers Believe About Names. It has since spawned a long list of Falsehoods Programmers Believe About....) Everyone has fingerprints! The BBC has a grim tale of a family with a genetic mutation which means they have no fingerprints. It details the issues they have getting official ID. In 2010, fingerprints became mandatory for passports and driver's licences. After several attempts, Amal was able to obtain a passport by…
Continue reading →











