Responsible Disclosure: CloudFlare - more interested in tracking than security
CloudFlare claim they want to secure the web - but they seem more interested in tracking their customers than giving them decent security.
Upon registering with the Internet giant, users are encouraged to confirm their email addresses. So far, so standard. This is the confirmation message CloudFlare sends out:

Looks good! Hey! I wonder where that garish orange button goes?
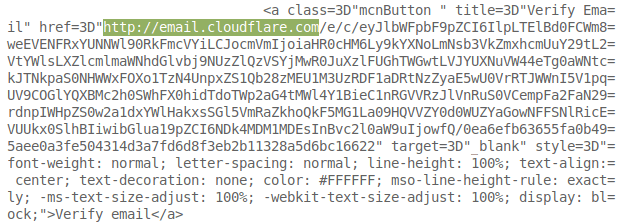
WHAT!?! An http URl? Surely some mistake. Every baby-in-a-basket knows that we should use https everywhere.
No matter, I'll click on the raw link underneath. That's got an https at the start, right? WRONG!
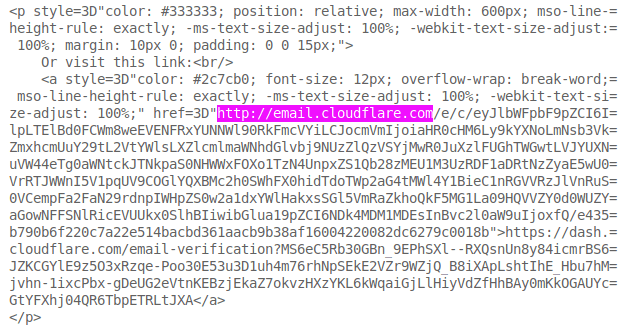
Yup, the clumsy clowns at CloudFlare have managed to turn a secure URl into an insecure one. Bless.
Why do they do this? Because they want to track every click on their emails. Their statistics are more important than your security.
Why is this bad?
Links to http sites are not secure. That means your visit to that URl can be seen by your ISP and anyone else between you and your destination.
A user clicking on that insecure URl risks having their request intercepted. While an attacker can't log in using the data they've captured, they would be able to redirect the user and phish their details.
It gets worse!
Hey, at least email.cloudflare.com belongs to Cloudflare, right?
Well... Not quite. Visit it, and you'll find that it is run by Customer.io's edge event collection service.
Visit an incorrect URl like email.cloudflare.com/example and you'll be taken to Customer.io's site.
Basically, if Customer.io gets hacked, or goes rogue, they can start phishing all of Cloudflare's customers. Nice...
How to solve it?
STOP TRACKING EVERY LINK IN YOUR EMAILS!
Or, if you really have to - make sure your tracking server supports https and is controlled by you.
Disclosure timeline
I went through HackerOne in the vague hope of getting a tiny bug bounty.
- 2018-10-19 - Disclosed
- 2018-10-26 - Response from HackerOne asking for clarification
- 2018-10-27 - "We were able to validate your report, and we have submitted it to the appropriate remediation team for review."
- 2018-11-05 - Informed them that I indented to publish on the 19th. Received no objection.
- 2018-11-19 - Response from HackerOne "It looks like the problem has been solved and future emails will provide https:// verification links."
- 2018-11-20 - Published
All this has happened before...
This is an identical bug to the one I disclosed to Udacity who were kind enough to say thanks and send me some merchandising.
 €100 Bug Bounty from Intigriti - please stop tracking your confirmation emails!
€100 Bug Bounty from Intigriti - please stop tracking your confirmation emails!
Andrew McGlashan says:
Šime Vidas says: