
Should my bank be able to block me from using their Android app, just because my phone is rooted? I'm reluctantly coming to the conclusion that... yeah, it's fair that they get to decide their own risk tolerance. Sage of the Internet, and general Sooth Sayer, Cory Doctorow once gave an impassioned speech on "The Coming War on General Computation". I'll let you read the whole thing but, I think, the salient point is that some people want to restrict the maths we're allowed to do on our…
Continue reading →
I used to work in a call centre for a Very Big Company. Every week, without exception, we'd get a bunch of new starters to train. And every week, without exception, a newbie would be fired after looking up a famous person's data. This was in the days before GDPR. There was a lot less general awareness of data protection issues. It didn't matter how often will drilled it into trainees' heads - someone would breach privacy within 5 minutes of getting on the system. It seemed to be an almost…
Continue reading →
Suppose you are sent a link to a website - e.g. https://example.com/page/1234 But, before you can access it, you need to log in. So the website redirects you to: https://example.com/login?on_success=/page/1234 If you get the password right, you go to the original page you requested. Nice! But what happens if someone manipulates that query string? Suppose an adversary sends you a link like this: https://example.com/login?on_success=https://evil.com A sensible redirection system should say…
Continue reading →
I needed a way to generate a TOTP secret using a fairly locked-down Mac. No Brew. No NPM. No Python. No Prolog, COBOL, or FORTRAN. No Internet connection. Just whatever software is native to MacOS. As I've mentioned before, the TOTP specification is a stagnant wasteland. But it does have this to say about the secret: The secret parameter is an arbitrary key value encoded in Base32 according to RFC 3548. The Base32 alphabet is pretty simple. The upper-case letters A - Z, and the numbers 3 - …
Continue reading →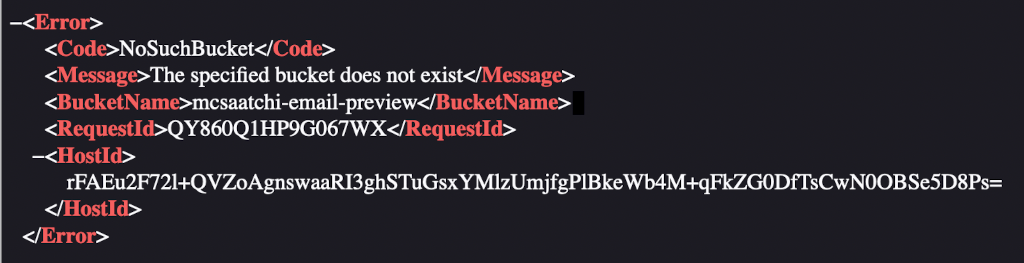
A few weeks ago, I received a billing email from my phone provider O2. While glancing at it, I noticed all the images were broken. Viewing the source of the email showed that they were all coming from http:// mcsaatchi-email-preview.s3.amazonaws.com/o2/... What happens if we visit that domain? Ah, the dreaded "The specified bucket does not exist" error. At some point the images were served from that domain but someone deleted the bucket. This is a problem. Amazon doesn't reserve…
Continue reading →
This is a curious book. It starts out as a look at the security of everyday objects, but quickly becomes a series of after-dinner anecdotes about various security related issues. That's not a bad thing, as such, but a little different from what I was expecting. There's no doubt that Mikko walks the walk as well as talking the talk. Almost every page contains a bon mot. For example: Working in information security is sometimes a bit like playing Tetris: your successes disappear but your…
Continue reading →



