

More Phishers On Twitter
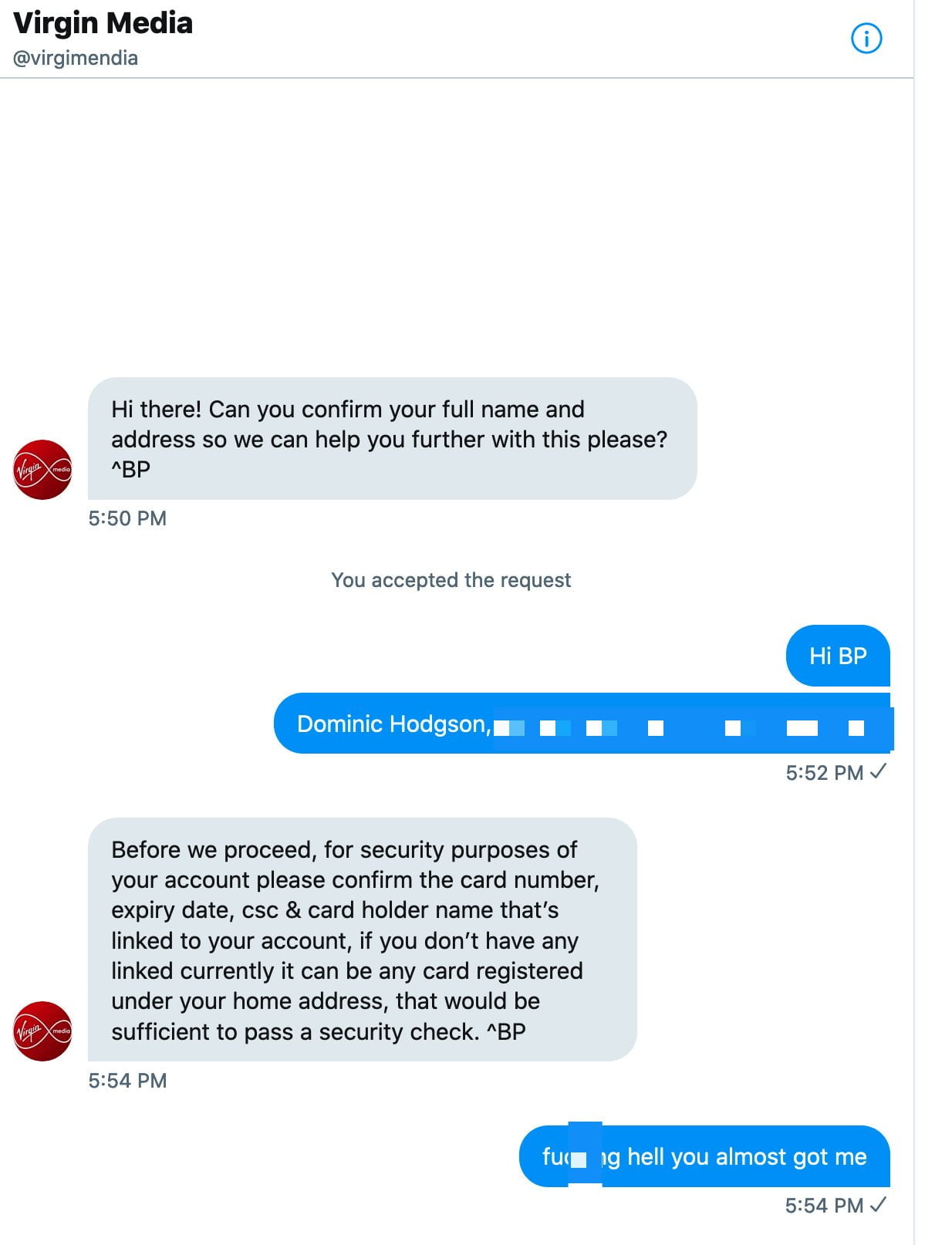
My mate Dom was moaning to his ISP on Twitter. They sent him a private message so they could look into his account.
Blimey! Thankfully, that was a pretty brazen and inept attempt at phishing. Anyone asking for all your card details like that should set the alarm bells ringing. Of course, phishers often target credulous people who don't understand that they're being scammed.
By sending an email that repels all but the most gullible the scammer gets the most promising marks to self-select, and tilts the true to false positive ratio in his favor. Cormac Herley - Microsoft Research
Investigating the account might not have given much of a clue about its dodgy nature.

Superficially, it looks identical to the official account. It even has a verified badge on its Tweets. How? Because all it does is retweet the official account it is spoofing!
Looking closer you should be able to spot that it is a fairly new account with zero followers. Oh, and the name is "Virgimendia"! The kerning of fonts on a small screen is likely to confuse lots of users.
They were quite clever in targetting people who had mentioned the official account. This is similar to a Twitter phishing attack I blogged about 5 years ago.
I tried my luck at baiting the scammer - to no avail!

Their use of language suggests they're a British English speaker. At least, I assume they're not thinking of me in cryptographic terms!
A bunch of us reported the account, and by the next morning it was gone.
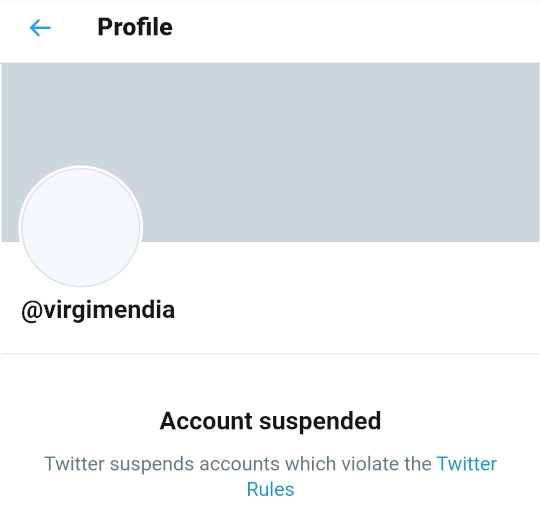
The disturbing thing about this, is that the scammers had been operating for at least a week. Virgin Media had been alerted, but seemingly didn't take any action.
(Content Warning: The following Tweets contain racist language and encouraging suicide.)




https://twitter.com/julsbvby/status/1294702901835726854






Could automated tooling have stopped this? To a human it looks pretty obvious that this is a scam. But what heuristics would you use to train a model designed to stop this? And how many false positives would it detect?
Stay safe out there.
Marcus Downing says:
I like to think I’m decent at spotting phishes (it’s literally my job) but a Virgin Media impersonator got me once. Their @ wasn’t even close but I saw everything else and it seemed to match!