I've spent two months trying to report this issue to Getty images. They haven't responded to my emails, phone calls, Tweets, or LinkedIn messages. I've tried escalating through OpenBugBounty and HackerOne - but still no response. I've taken the decision to fully disclose this XSS because the Getty Images sites accept payments from users - and users need to be aware that the content they see on Getty Images sites may have been tampered with.
This XSS was slightly unusual. When a user submits HTML to a site search, it should be escaped before echoing it back on the screen. And that's exactly what Getty Images does:

Except!
It only does that if there were no results found.
If a malicious user can craft a search term that returns results, then HTML is passed unescaped:
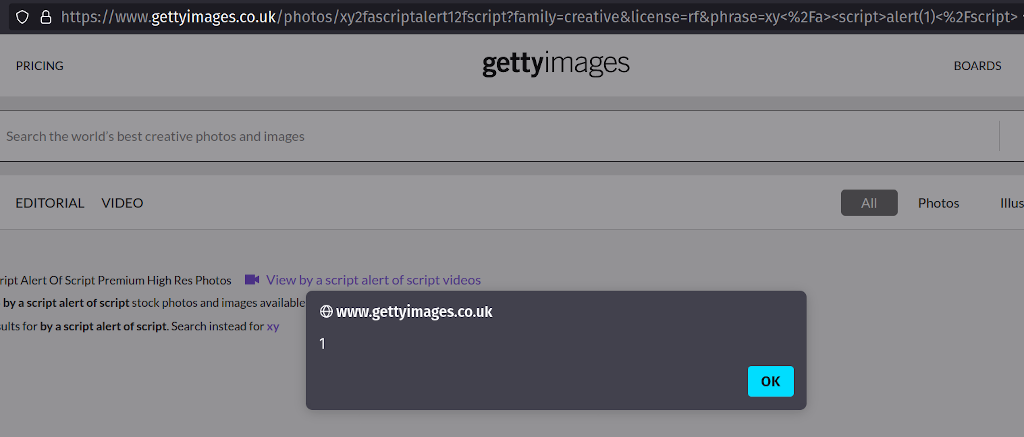
So - take care if you're using the Getty Images websites. Be cautious if it asks you for your financial or personal data. It is possible that the information you're seeing has been manipulated by an adversary.
Timeline
- 2021-06-17 Discovered on the Getty Images Norway site, replicated on the UK site. Contacted via Twitter as they have no publicly listed security contact. Responsibly disclosed via OpenBugBounty
- 2021-06-23 Used HackerOne's Disclosure Assistance programme to see if that would prompt a response.
- 2021-07-12 Tried contacting via LinkedIn and the general contact form on their website. Made several attempts over the month.
- 2021-07-29 Direct email to security employees at Getty Images.
- 2021-08-17 Blog post automatically published.
3 thoughts on “Full Disclosure: XSS in Getty Images”
It's really frustrating when big websites don't respond to ethical vulnerability disclosure.
| Reply to original comment on twitter.com
Is it really that difficult for an organisation with a website to have a clear vulnerability reporting process, and then to actually do something about reports?
I know it's not standardised yet, but we've gone for .well-known/security.txt (decoded.legal/.well-known/se…).
| Reply to original comment on twitter.com
Apologies you’ve had such a hard time connecting with the security team at Getty Images, I’ve responded to your email with additional details.