The UK is facing an epidemic of SMS fraud. Scammers know that we're all at home eagerly waiting for deliveries. So they send out phishing messages saying "Sorry we missed you" or "You need to pay a delivery fee". If you click on the link they send, you'll go to a very convincing website which looks identical to the courier's page.
Whereupon the fraudsters will ask for your bank details, credit card number, mother's maiden name, and inside leg measurement.
There are many complex reasons why this fraud proliferates. But one thing underpins these scams - a domain name and hosting. Over the last few months, the vast majority of the fraud I've seen has come from domains registered by NameCheap.
OK, but that's anecdotal evidence. Is there anything more robust?
My friends in the UK's National Cyber Security Centre have released a report looking at phishing - amongst other things. Here's what they have to say about NameCheap:
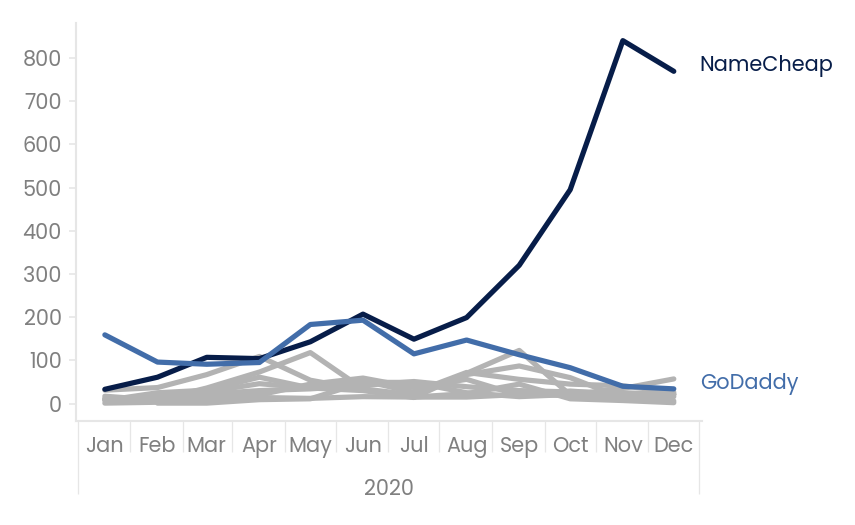
Figure 1 shows that NameCheap became the most popular host of UK government-themed phishing during 2020.By December 2020 we found that it hosted in excess of 60% of phishing in this category.
NameCheap appear to be the preferred supplier of domains and hosting to the criminal community.
OK, they can't easily control who registers domains. But I'm sure that they take reports of abuse seriously. Right?
Looking specifically at the number of campaigns hosted by NameCheap against its monthly median attack availability, we see that by mid-year the median takedown times were consistently in excess of 60 hours. This undoubtedly made NameCheap an attractive proposition to host phishing and may explain the rise in monthly hosted campaigns that followed for UK government-themed phishing.
Oh...
The problem is, these domains are designed to be "hit-and-run". The spammer sends as many phishing messages as possible, in as short a time as possible. They're expecting the domain to be taken down. Every minute counts.
The CEO of NameCheap is, unsurprisingly, defensive of his company's handling of the situation.






What can be done?
There are some proposals to restrict access to new domains - but I don't think that's effective. A spammer can register a domain, wait a month, then blast it out.
NameCheap could make it harder for people to register domains with them. They accept anonymous registration using crypto-currency. I want to live in a world where people can anonymously register web services - but I also don't want to be bombarded with spam.
Given that NameCheap want anonymous customers, and given the prices for hosting are cheap, perhaps they should be taking "good behaviour" deposits from anonymous customers? Take, say, a hundred pounds and refund it only if the account isn't suspended.
Perhaps Nominet could insist that its members take swifter action against spammers - and then remove the ability to resell domains for those that don't?
Maybe NameCheap should increase its prices so that it can afford to pay for the abuse staff that it so desperately needs?
There are no easy answers here. But NameCheap are obviously doing something to attract - and profit from - scammers. What can be done to make them take more responsibility?
16 thoughts on “Why do scammers love NameCheap?”
A well put summary of the issues around the current flurry of SMS spam, how easy it is to host domains and sites, and some thoughts on how to impede criminals while enabling anonymous use of services.
Meanwhile I wonder if NameCheap counts as "bulletproof hosting" at this point?
| Reply to original comment on twitter.com
Ian
It’s a bit of a whack-a-mole solution, but the mobile networks could start reverse look-up of domains in SMS messages, and if it’s supplied by [unreliable domain name seller] block the message on quality control grounds until the domain name seller cleans up its act.
A bit like IP reputation scores for spam filters, but for the domain name reseller instead.
This worries me. I don’t want my phone company “protecting” me. Perhaps I should think of the children…?
Eric Andersen
I have found in the recent past that SPAM text messages have contained links to domains registered with NameCheap. When I complained to NameCheap, I was told to take it up with the telecom company.
It seems there are always people seeking to exploit gaps in the system and when attempts are made to close those gaps, cries of “excessive regulation!” can be heard from those same groups.
There is a synergy here between the spammers and NameCheap. Both are profiting from the exploit and you and I are paying the price.
I have no answer, I don’t know the inner workings well enough to propose one. I can only hope that someone more clever that I can find one.
Ubaldo
I've had their so-called attorney tell me that I need to file an FCC complaint, in the U.S. I replied back "then what exactly do you get paid for if you're the attorney of record for domain abuse complaints? Spamming IS abuse, its being done with your domain name. Shut the domain name down and the spamming ceases. That is helping the situation not kicking the can down the road like your pathetic response suggests."
That was 4 years ago, c.2018. Today, mid-2022 I still receive upwards of 20 spam calls and 5 SMS spam texts PER DAY on my cell phone. 99.3% of the SMS spam that I receive is STILL from namecheap domain names usually registered within the prior 14-30 days, many times its within a day!
The domain names used in the SMS spams are gibberish too, they're not even worth reg-fee. Just a bunch of letters and numbers. Isnt it clear to these highly paid attorneys what is going on? Doubt it as 6 decades on this planet have proven that degrees AND/OR high pay has zero correlation to brains.
Apparently the spammers flock to namecheap more so than any other registrar so what that tells me is they are lax on wanting to stop this whereas these spammers likely have hit brick walls at other registrars. The complete shutdown from their abuse attorney makes me wonder if namecheap is in on it or somehow receiving benefit from it.
The answer is simple, if there isnt already a TOS clause that states the domain will be deleted, immediately, upon verifyable proof of spam activities then it needs to be added to namecheap's TOS. AND THEN namecheap needs to execute on it when shown proof.
Until then I have not and will not purchase another domain name at namecheap no matter how low the cost it. I will not subsidize this abuse and the willful ignoring of it. I have moved all my 400+ domain names out of that registrar years ago. I have also posted publicly on forums this very same statement, advised people to stay away from namecheap lest they wish to support spamming and willful ignorance of spamming.
The cost of a lost customer is quite a large number.
I am not a spammer. But I do love namecheap because I am able to lease domain names from them without ever giving them my name by paying in bitcoin. It’s unfortunate this, and other aspects, are abused but it is worth it in the end.
James
I wonder if a login-namecheap.com domain purchased from Namecheap with a mocking website hosted by them might get a different response...
Phil
It would, but not for the reason you might want. This is because it would be an abuse of their name, so they would be responding to this rather than the general impersonation of a company. Namecheap would likely expect each company to respond by taking action to protect their respective names and trademarks. This is the individualist/libertarian approach that is responsible for giving the scammers the benefit of the doubt to begin with.
Chris March
You’re right to call out NameCheap’s shoddy practices, but at the same time it feels like the problem of SMS fraud could be well-mitigated by the mobile networks?
There is already the 7726 spam reporting service – yet information on what the mobile networks do with reports made to this service is scarce. (Is it just there to make people feel better?)
A common pattern I see is for scam messages to start with the company name and contain a URL; e.g. “DELIVERY COMPANY: Your parcel has an unpaid £1.45 shipping fee. Please pay this now via: not Delivery Company’s website. Your package is at risk if this fee is not paid.”
There are a small number of companies whose brands get targeted in this way – banks and delivery companies seem to be the targets at the moment. Could the mobile networks take a more active role and liaise with these companies to establish what domain name(s) they are going to use in their SMS notifications – and when they are asked to deliver messages that match known fraudulent patterns containing a brand name and a URL that don’t correspond with each other, they instead route the message to /dev/null?
whack-a-mole gets a few victims bbc.co.uk/news/uk-englan…
| Reply to original comment on twitter.com
It seems that namescheap do not care about spammers using them as long as the registration cash keeps flowing. If they really cared they would ensure they had full contact details for their customers and inform the FBI if those customers illegally spammed or phished. I am in the UK and have been finding their customers emails constantly for months being blocked by my servers anti spam software. I also am not on any USA marketing lists so these spammers are using pirate email databases to spam the world. Time ICANN took action!
Boomish
All the phasing emails I get are registered from Namecheap, the problem I find is it's so hard to report them, they ask for headers via twitter then they ask for the Raw Source which is too large to DM. Then they say fill out an "abuse" ticket but thats long and complex with sections that are not need for simple phishing emails. Why can't they have a simple email forwarding service.
Dirk Daggler
Namecheap has closed all tickets and rejects responsibility as the criminal websites' data is with another hosting provider and they recommend clicking the 'unsubscribe' link on spam emails, which of course only leads to email addresses being verified to be bombarded with more spam. Hundreds of spam emails lead to dozens of websites, all belonging to the same non-existent 'company' in Iceland, all registered via Namecheap. I am at my wits' end and have noticed over the past 5 months that Namecheap thus seems to be deliberately supporting this spam terror and simply generating revenue through the dozens of domains registered there.
Kevin
Namecheap is operating exactly they way they want to. Their abuse department will claim they can't find the domain you complained about (it's line 1), or say they're working on it, or say there's no evidence of abuse. Their Twitter account is far more responsive but it's still retroactive. Namecheap does nothing to stop crime gangs from registering an infinite number of new domains.
Besides the Namecheap component, there are one or two high volume SMS spam crime gangs a well-established and stable infrastructure on Salesforce, Amazon, Cloudflare, and High Speed Web. Yes, they're all fully aware that they're hosting a credit card phishing gangs.
I've been getting phishing spam for six months now in which the drop box for harvesting addresses is hosted on a domain that lives on Namecheap servers. I send complaints, and get back the automated "we take abuse reports very seriously" email. Then a day or two later I get more phishing spam, almost always sent from a Bluehost IP address, almost always with the drop box hosted by Namecheap.
SpamBuster
I started to get hundreds of spam messages a day. After doing a WHOIS on each spam message, I realized every single one of the spammers were using NameCheap domains. I started to report every single domain that came in. During the first week, NameCheap was actively deleting every domain I sent in. The spams kept coming with new domains being setup daily. I kept reporting them, until one day I realized they were no longer deleting the domains or responding to my emails. After I complained, they wrote me back saying they now needed even more information about each domain. Basically making my job harder and more time consuming. There was no issues during the first 2 weeks with the format I was using, and was even told to keep sending them in using that same format. I decided I wasn't going to use the format they wanted me to use, instead, opting to contact the BBB to push for a permanent resolution to this issue. Believe it or not, I have not received one single spam email since BBB contacted them. Hmmmm, how easy was that?