
I've written before about the nascent WebMonetization Standard. It is a proposal which allows websites to ask users for passive payments when they visit. A visitor to this site could, if this standard is widely adopted, opt to send me cash for my very fine blog posts. All I need to do is add something like this into my site's source code: <link rel="monetization"…
Continue reading →

Codeberg is a hip new code hosting site - similar to GitHub and GitLab. And, much like Gits Hub & Lab, users can serve static content through Codeberg pages. Somehow I screwed up my configuration, and when I visited edent.codeberg.page/abc123 I got this error: Now, whenever I see something from the request echoed into the page's source, my hacker-sense starts tingling. What happens if I…
Continue reading →
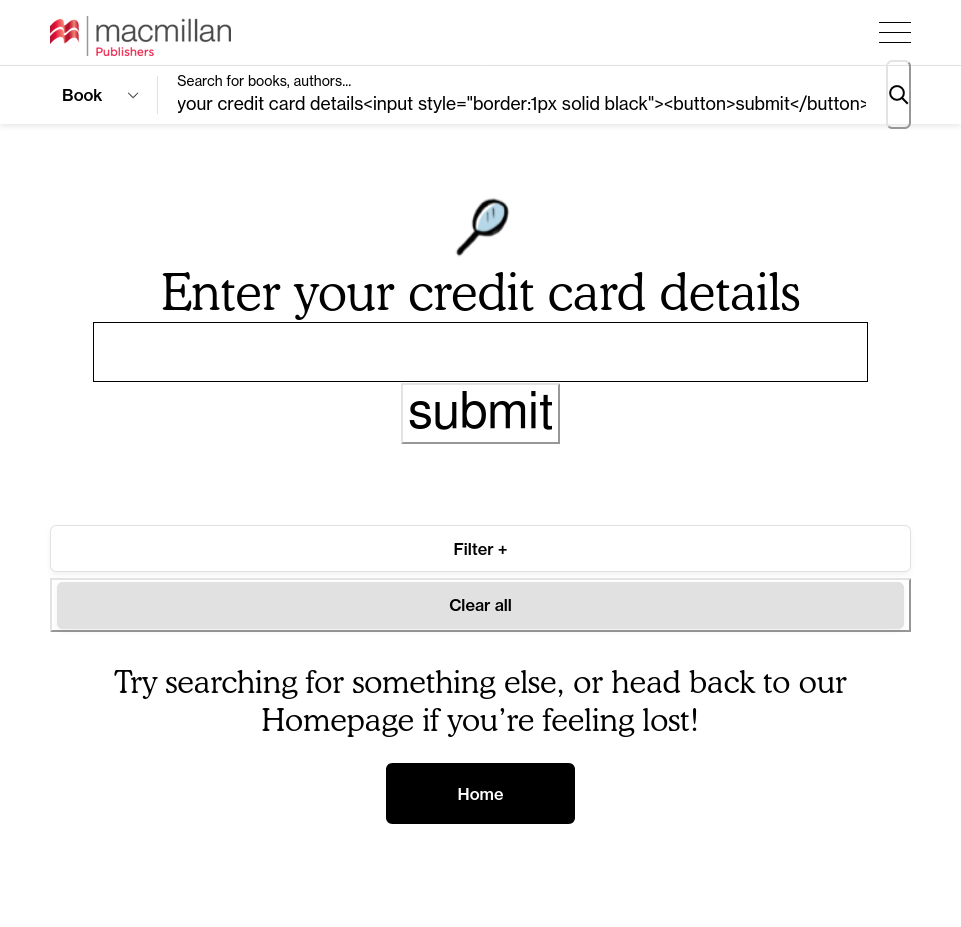
Another day, another unfiltered reflection of user-supplied content! You know how this goes by now. You type into a search box <em>test and the whole page suddenly turns italic. Luckily, the Macmillan Publishers' website filtered out any <script> elements it encountered. But that still leaves the attacker with the ability to draw SVGs over the page or, more maliciously, start harvesting…
Continue reading →
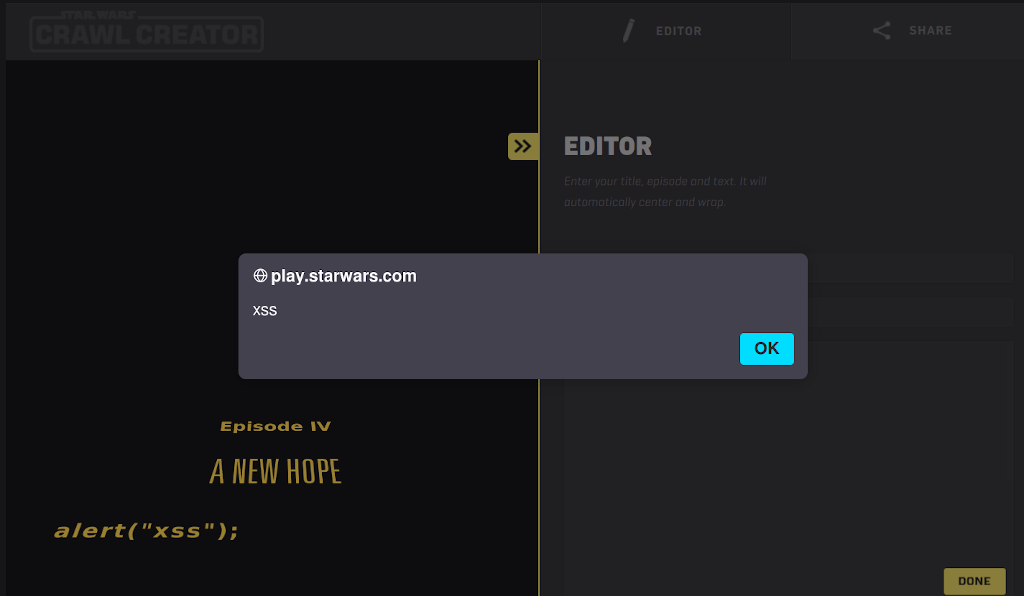
You remember that bit in Star Wars where the Rebels find the flaw in the Death Star plans and then completely fail to exploit it? Yeah, that's why they don't make movies about inept hackers like me… Anyway, the website https://play.starwars.com/html5/starwars_crawlcreator/ allows users to create their own "Star Wars" style crawl. It's a fun little site - but it has a few flaws. Whenever you l…
Continue reading →

This is a diary of what I've learned. Hopefully it will let other learners know what the course is like, and if it is worthwhile. Oh, and it might just help me remember what I'm learning! Verdicts Some of the lab tasks were impossible without looking at the cheat sheet. I got stuck on one because the question told me to go to one URl, but I had to guess the one which was vulnerable. Felt like a …
Continue reading →
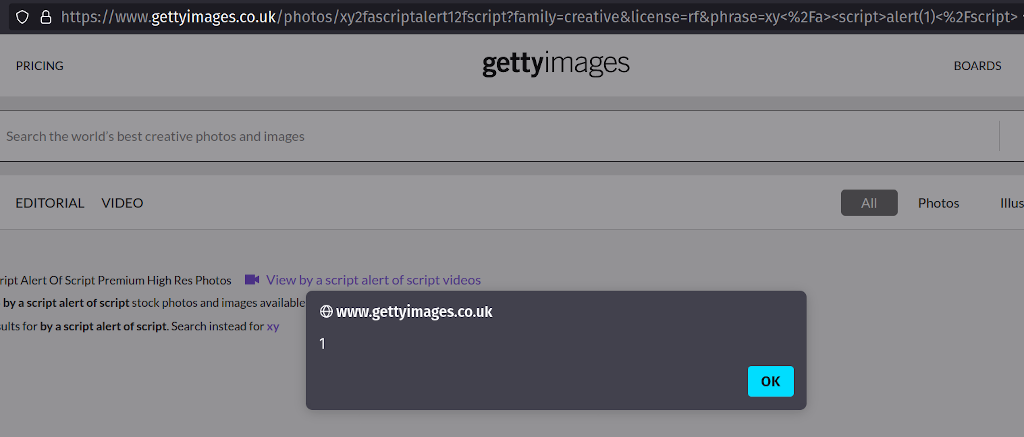
I've spent two months trying to report this issue to Getty images. They haven't responded to my emails, phone calls, Tweets, or LinkedIn messages. I've tried escalating through OpenBugBounty and HackerOne - but still no response. I've taken the decision to fully disclose this XSS because the Getty Images sites accept payments from users - and users need to be aware that the content they see on…
Continue reading →

Legacy websites are a constant source of vulnerabilities. In a fit of excitement, a team commissions a service and then never bothers updating it. Quite often the original owners leave the business and there's no-one left who remembers that the service exists. So it sits there, vulnerable, for years. The [REDACTED] website had a subdomain which was running KANA's IQ software which was last…
Continue reading →

Bit of a boring write-up, but here we go. Taxi app Gett had a content injection flaw in its search function. By searching for an HTML string, it was possible for an attacker to add links or images to a page. It was really hard to contact them - but the threat of media attention sprung them into action. For example, searching for a specially crafted string meant that an arbitrary SVG could be…
Continue reading →

Here's a quick write-up of a minor XSS (Cross Site Scripting) vulnerability on the website of Three.co.uk - one of the UK's mobile providers. A brief recap... Most websites have a search function. If you search for something which cannot be found, the site will often say "No results found for XYZ." If we can convince the search engine to spit out HTML, we can inject malicious content into…
Continue reading →

One of the problems with the BlockChain goldrush is that it attracts a lot of people who don't necessarily have the required technical skill to safely run a service. This in turn reduces trust in the ecosystem. I'd like to discuss ArtChain.info - "Certifying Art Using the Bitcoin Blockchain" - and the some of the security issues I found there. XSS This is one of those simple bugs which every…
Continue reading →

Update! I now have an XSS which is only 18 characters! Here's a fun little game for all the family! What is the minimum number of characters required to perform a successful XSS attack? Let's take an entirely theoretical example - suppose we have a site which echos back user input without sanitising it. So a search for " <em>" turns the whole page italic. ahem A hacker might think, "Hurrah! …
Continue reading →

Another day, another bug! LetsSaveMoney.com is a "money saving" site. It offers discounts on a wide range of products and services, and is financed through affiliate marketing. Links removed, because the site has disappeared. My Trade Union, Prospect, has just launched a white-labelled "Members' Rewards" based on LetsSaveMoney - that's how I came across this bug. It's a depressingly familiar…
Continue reading →











