
The UK's official web infrastructure is in a shockingly poor state. I've been doing some light digging into the security of UK Schools' websites. As I've written about ad nauseum, the Government takes almost no interest in the way some of its official websites are managed. The Department for Education is particularly inept when it comes to technology which - given that our country's future…
Continue reading →

I don't particularly like picking on the security of Government websites. I do it a lot - but I always feel guilty about besmirching the good name of the many talented people who work in the Civil Service. Today's flaw, however, is a particularly basic mistake which simply shouldn't be allowed to happen by any competent site owner. What Is An Open Redirect? A redirector is a small web service …
Continue reading →

Her Majesty’s Inspectorate of Constabulary (HMIC) are the police who police the police. As the Police policers you'd expect their website to be copper-bottomed. That they would detect anything amiss when inspecting their thin blue links. Mind you, some web developers are a law unto themselves. Yeah, yeah, these puns are unbearable. Fine. Whatever. Amusing photo by kind permission of the i…
Continue reading →

Imagine, just for a moment, you suspect that a friend of yours is a criminal. Perhaps they are running an illegal proxy, or hosting a search engine, or maybe criticising a dangerous cult, or even taking suspicious photographs. These are all - apparently - within the remit of The City Of London Police. Better report such heinous crimes to them. As a high-tech policing unit, they encourage you…
Continue reading →

A few months ago, I was attending the National Hack The Government event. I was showing off some of the work I had been doing on "The Unsecured State" - looking at *.gov.uk website security. I was chatting to an envoy from the Food Standards Agency who was eager to hear more about what I'd discovered. "Oh," I said, "It's pretty easy. Let's take a look at your website. If I were to type some…
Continue reading →

It has been an intense few months digging through the security failings of the UK Government’s websites and trying to responsibly disclose them. It culminated with a week of blog posts exposing the vulnerabilities - and an award winning hackathon project. So what has been the reaction? The Good Privately, I've been contacted by people within the Civil Service who are working hard to make t…
Continue reading →
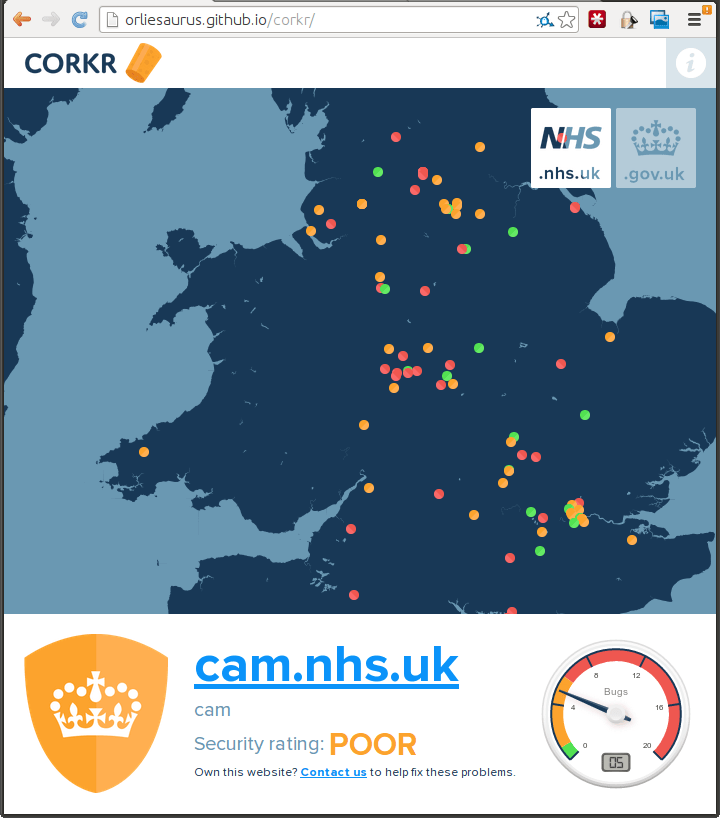
What a crazy weekend! I made the last minute decision to attend Rewired State's "National Hack The Government 2014" hackathon. Rather than hack on any of the provided datasets, I wanted to work on an interesting way to present all the security flaws I had found in Government websites. I teamed up with Mark, Marcello, and Orlando - together we created "Corkr - Plugging the Government's Digital …
Continue reading →

This is part 5 of a series of blog posts looking at the security of the UK Government's web infrastructure. The primary cause of the vulnerabilities I've exposed over this series is abandonment. In a flurry of excitement a website is commissioned and created. Then, as time wears on, people begin to drift away from the project. Job titles change, people are reshuffled, and senior…
Continue reading →

This is part 4 of a series of blog posts looking at the security of the UK Government's web infrastructure. Over the last few days, I've shown that hundreds of websites run by branches of the UK state are in a perilous state of disrepair. There are multiple sites with hugely embarrassing XSS flaws, running ancient and unsecured software, languishing unmaintained and long since abandoned. What …
Continue reading →

This is part 3 of a series of blog posts looking at the security of the UK Government's web infrastructure. Britain's National Health Service is riddled with old and insecure WordPress-based websites. Many of these sites have severe flaws including being vulnerable to XSS attacks. There is absolutely no suggestion that patient data or confidentiality has been put at risk. These flaws were …
Continue reading →

This is part 2 of a series of blog posts looking at the security of the UK Government's web infrastructure. Many XSS flaws rely on altering the GET parameters of a request. Some webmasters seem to think that if their forms only use POST they will be immune from the XSS. This is not the case. Don't Press This Button Pressing this button will send a POST request to the Department of…
Continue reading →

This is part 1 of a series of blog posts looking at the security of the UK Government's web infrastructure. The UK Parliament website is pretty great. It houses a huge amount of historical information, lets people easily see what's happening in the Commons and the Lords, and is run by some really clever people. That's why it's so depressing to see such a basic error as this XSS flaw in their …
Continue reading →











