
I maintain a a test-suite for TOTP codes. It contains a bunch of codes which adhere to the specification, some of which stretch it to breaking point, and some that are completely invalid. These codes are a good starting point for checking whether a 2FA / MFA app works correctly. Proton have release a swish new authenticator app for Android, iOS, Mac, Linux and Windows. Sadly, their open source…
Continue reading →
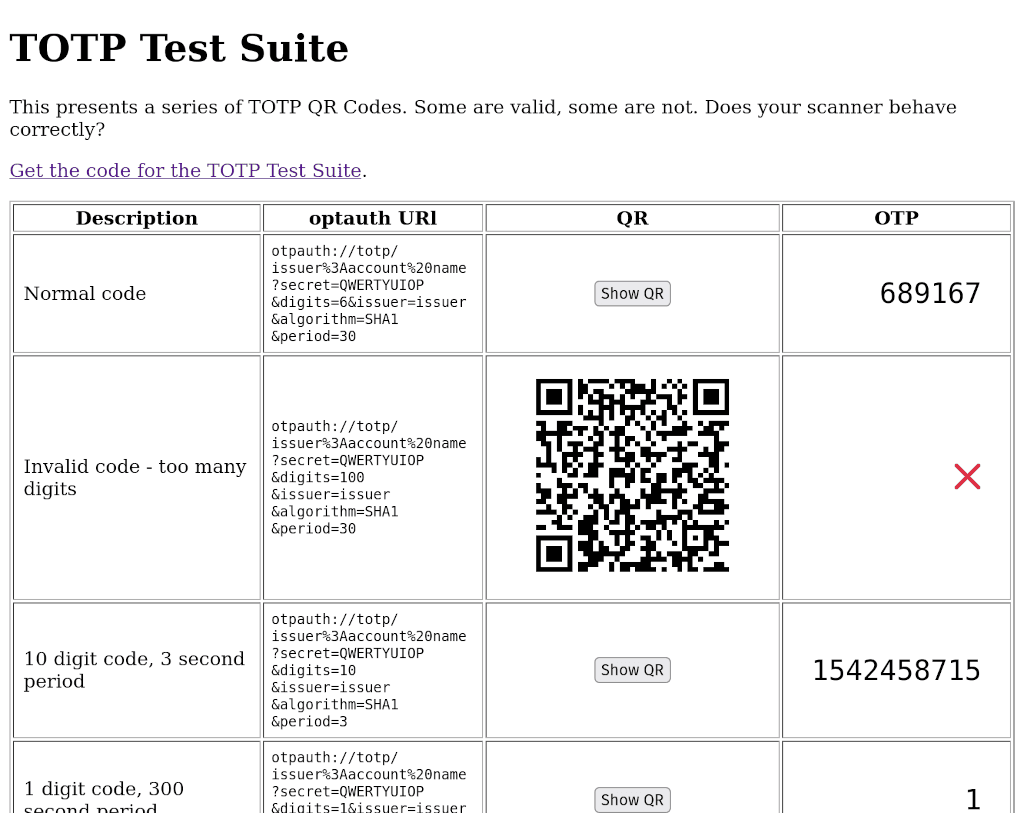
Because I'm a massive nerd, I actually try to read specification documents. As I've ranted ad nauseam before, the current TOTP spec is irresponsibly obsolete. The three major implementations of the spec - Google, Apple, and Yubico - all subtly disagree on how it should be implemented. Every other MFA app has their own idiosyncratic variants. The official RFC is infuriatingly vague. That's no…
Continue reading →

The Web Crypto API is, thankfully, nothing to do with scammy cryptocurrencies. Instead, it provides access to powerful cryptographic features which were previously only available in 3rd party tools. So, is it possible to build a TOTP code generator without using any external JS libraries? Yes! And it is (relatively) simple. Here's the code that I've written. It is slightly verbose and contains…
Continue reading →

If you use Multi-Factor Authentication, you'll be well used to scanning in QR codes which allow you to share a secret code with a website. These are known as Time-based One Time Passwords (TOTP). As I've moaned about before, TOTP has never been properly standardised. It's a mish-mash of half-finished proposals with no active development, no test suite, and no-one looking after it. Which is…
Continue reading →

Here's a "fun" thought experiment. Imagine a website which let you sign in using only your username and TOTP code. No passwords. No magic links emailed to you. No FIDO tokens. No codes via SMS. Just a TOTP generated and displayed on your device. Is that useful? Sensible? Practical? It's certainly technically possible. Store the username, store the TOTP seed, done. Your users can now log in. …
Continue reading →

Yeah. Yeah, I reckon so. Under the right circumstances. Multi-Factor Authentication (MFA, 2FA, TOTP, whatever you want to call it) is pretty nifty. You scan a QR code and your phone will continually generate a set of one-time passwords which are synchronised with a remote server. There's nothing stopping multiple people from scanning that QR code! They will each have the same password displayed …
Continue reading →

Imagine, just for a moment, you and your friends decide to travel in time. In order to make sure you can authenticate your communications with each other, you set up a shared Time-based One Time Password (TOTP). The TOTP algorithm uses a Hash-based Message Authentication Code (HMAC). The hash is calculated from a shared key and a time-based component. The key is a short string of characters.…
Continue reading →
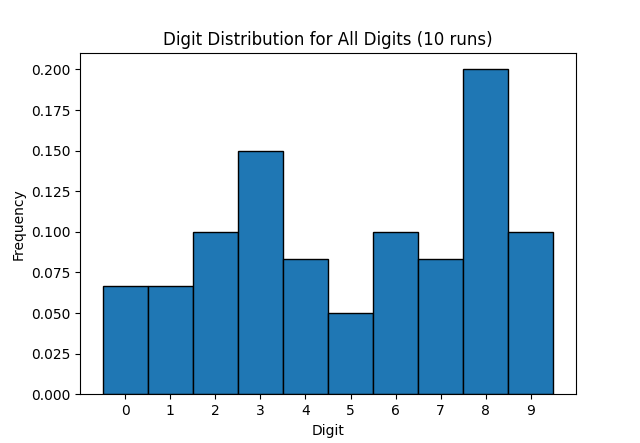
I'm pretty sure that the 2FA codes generated by my bank's TOTP app have a bias towards the number 8 - because eight is an auspicious number. But is that just my stupid meaty brain noticing patterns where none exist? The TOTP algorithm uses HMAC, which in turn uses SHA-1. My aforementioned brain is not clever enough to understand how that works. Although bigger, meatier brains have assured me it …
Continue reading →

Recently, WordPress got in contact with me to say they suspect that my password was exposed in some sort of data breach. Well, it's a day ending with a "y" - so of course some scumbag has pilfered my digital identity. WordPress mandated that I change my password. But was that really necessary? Firstly, the password was uniquely generated by my password manager. It isn't re-used anywhere else.…
Continue reading →

I needed a way to generate a TOTP secret using a fairly locked-down Mac. No Brew. No NPM. No Python. No Prolog, COBOL, or FORTRAN. No Internet connection. Just whatever software is native to MacOS. As I've mentioned before, the TOTP specification is a stagnant wasteland. But it does have this to say about the secret: The secret parameter is an arbitrary key value encoded in Base32 according to…
Continue reading →

Yes yes, Cunningham's law etc etc! I want to play around with 2FA codes. So, I started looking for the specification. Turns out, there isn't one. Not really. IANA has a provisional registration - but no spec. It links to an archived Google Wiki which, as we'll come on to, isn't sufficient. There's some documentation from Yubico which is mostly a copy of the Google wiki with some incompatible…
Continue reading →







