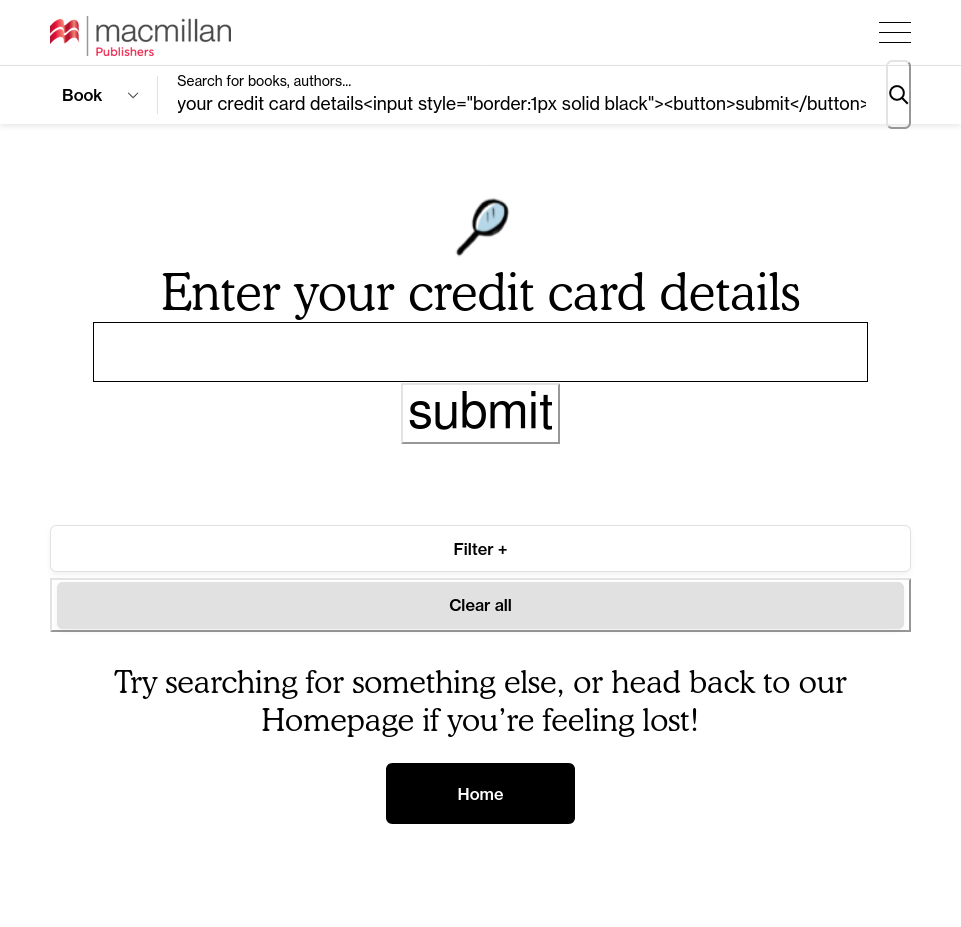
Another day, another unfiltered reflection of user-supplied content! You know how this goes by now. You type into a search box <em>test and the whole page suddenly turns italic. Luckily, the Macmillan Publishers' website filtered out any <script> elements it encountered. But that still leaves the attacker with the ability to draw SVGs over the page or, more maliciously, start harvesting…
Continue reading →
I hate academic tests. Wouldn't it be great if you could find the official answer papers? Oh, cool, the OCR Exam Board is hosting answer sheets for all my classes! What happens if I click it? Yeach! It redirects users to a scammy ebook service hosted on an external website. Which, I assume, the exam board does not endorse. Alongside exam books, textbooks, literary classics - there's a…
Continue reading →

Shamir's Secret Sharing (henceforth "SSS") is clever. Far too clever for most people to understand - but let's give it a go. Suppose you have a super-secure password for a Really Important Thing. Th15IsMyP4s5w0rd!123 You can remember this - because you're awesome. But it might be a good idea to share the password with someone else, just in case. Of course, if you share it with one person,…
Continue reading →
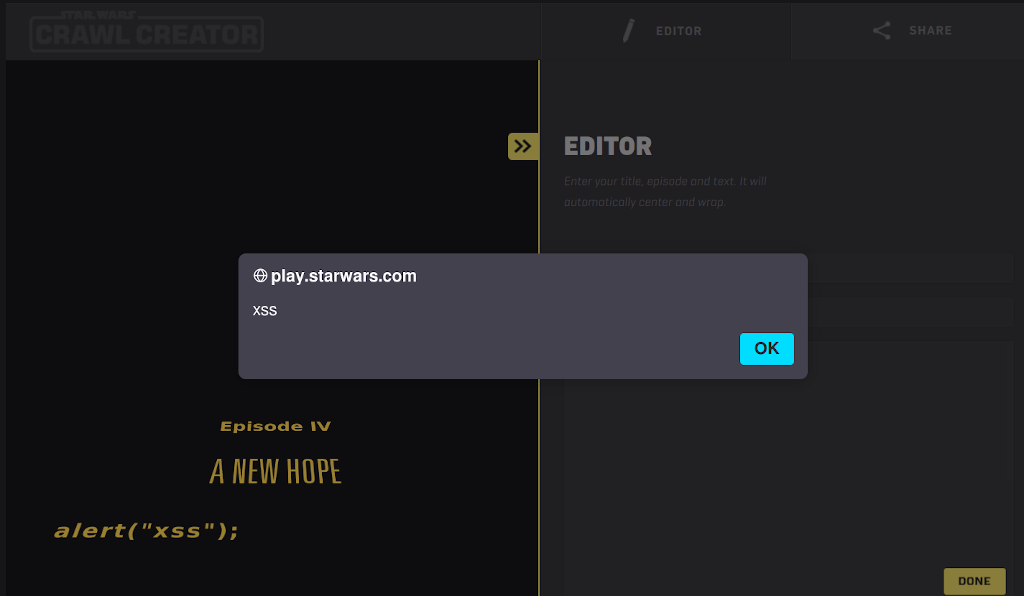
You remember that bit in Star Wars where the Rebels find the flaw in the Death Star plans and then completely fail to exploit it? Yeah, that's why they don't make movies about inept hackers like me… Anyway, the website https://play.starwars.com/html5/starwars_crawlcreator/ allows users to create their own "Star Wars" style crawl. It's a fun little site - but it has a few flaws. Whenever you l…
Continue reading →

This would be a best seller if it had been entitled "Everything I learned about national security talks, I learned from Cicero". Preferably dumbed-down to accompany a Netflix series about sexy Romans. Instead, it is a scholarly work which takes the reader through the art of rhetoric and how it is used and abused by modern speech-makers. It specifically looks at things through a National…
Continue reading →

Imagine… Last night, lightning struck our house and burned it down. I escaped wearing only my nightclothes. In an instant, everything was vaporised. Laptop? Cinders. Phone? Ashes. Home server? A smouldering wreck. Yubikey? A charred chunk of gristle. This presents something of a problem. In order to recover my digital life, I need to be able to log in to things. This means I need to know my u…
Continue reading →

Not really a security issue, but one which I thought was worth highlighting. It shows the peril of slightly vague specifications. When you scan a 2FA token into your authenticator app via QR code, you get presented with a bunch of information about your account. This lets you store things like the issuer and the account name. I recently scanned a code, and it displayed my name as Terence+Eden. …
Continue reading →

Yes yes, Cunningham's law etc etc! I want to play around with 2FA codes. So, I started looking for the specification. Turns out, there isn't one. Not really. IANA has a provisional registration - but no spec. It links to an archived Google Wiki which, as we'll come on to, isn't sufficient. There's some documentation from Yubico which is mostly a copy of the Google wiki with some incompatible…
Continue reading →
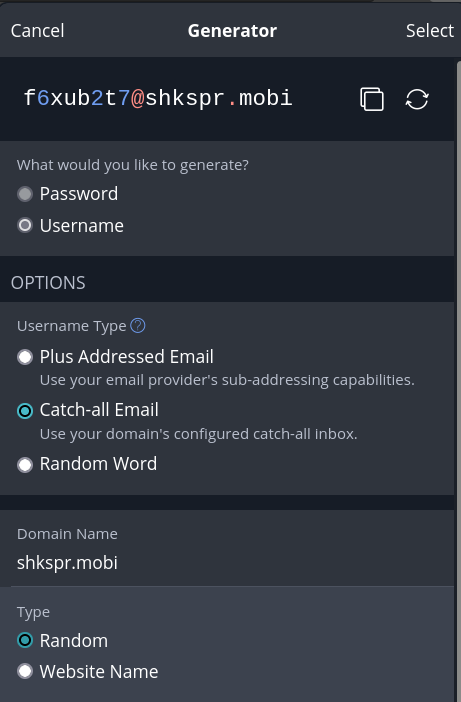
I've been using Bitwarden for years. It generates a unique password for every website I visit. There's only been one small problem - I want a unique username for each website. Let me explain. Sometimes websites sell or leak your email address to spammers. If you're using yourname@example.com for every site, you'll never know who leaked your details. Bitwarden can fix that! …
Continue reading →

I found this on a security-related Slack (shared with permission). It launched an entertaining discussion about the risks of taking a potentially fake FIDO token. We all know the risks of taking a free USB drive and shoving it in our computer, right? USB sticks can install software, act as a keylogger, transmit data over WiFi, and even physically damage the electronics! So a USB Yubikey…
Continue reading →

I found this book while following a citation trail for my MSc. Published before the 21st Century (fuck, I'm old) it's a run-down of this new-fangled thing called Information Warfare. It covers electronic attacks, espionage, computer security and more. In the last 20 years, depressingly little has changed. If you removed the mentions of ActiveX and floppy disks, it'd still be 90% relevant. It…
Continue reading →

The FIDO specification defines a form of Universal 2nd Factor (U2F) when users log in to a system. Rather than relying on one-time codes sent via SMS, or displayed on a phone screen, these are physical hardware tokens which are used to supplement passwords. When used with websites, this technology is also known as WebAuthn. I use a USB thumb-drive sized hardware token and they're nifty - but a…
Continue reading →











