
Chimoney is a new "multi-currency wallet" provider. Based out of Canada, it allows users to send money to and from a variety of currencies. It also supports the new Interledger protocol for WebMonetization. It is, as far as I can tell, unregulated by any financial institution. Nevertheless, it performs a "Know Your Customer" (KYC) check on all new account in order to prevent fraud. To do this,…
Continue reading →

There are two sorts of people in the world; those who know they are stupid and those who think they are clever. Stupid people use a password manager. They know they can't remember a hundred different passwords and so outsource the thinking to something reasonably secure. I'm a stupid person and am very happy to have BitWarden generate and save fiendishly complex unique passwords which are then…
Continue reading →

Terminology is hard. Computer terminology is even harder. Humans are animals who just love to classify things. We have a fundamental need in our delicious meaty brains to put things into conceptual buckets. This, I think, leads to some unfortunate consequences when our categories don't match up with other people's categories. For example, take this news story and this journalist's response to…
Continue reading →

There's a disturbing article in The Guardian about a person who was on the receiving end of a successful cybersecurity attack. EE texted to say they had processed my sim activation request, and the new sim would be active in 24 hours. I was told to contact them if I hadn’t requested this. I hadn’t, so I did so immediately. Twenty-four hours later, my mobile stopped working and money was wit…
Continue reading →

Some ideas are timeless. Back in 2004, an anonymous genius set up "FobCam". Tired of having to carry around an RSA SecurID token everywhere, our hero simply left the fob at home with an early webcam pointing at it. And then left the page open for all to see. Security expert Bruce Schneier approved of this trade-off between security and usability - saying what we're all thinking: Here’s a guy w…
Continue reading →

If you use Multi-Factor Authentication, you'll be well used to scanning in QR codes which allow you to share a secret code with a website. These are known as Time-based One Time Passwords (TOTP). As I've moaned about before, TOTP has never been properly standardised. It's a mish-mash of half-finished proposals with no active development, no test suite, and no-one looking after it. Which is…
Continue reading →

Lots of people using banking apps on their Android phones. They're a convenient way to check your balance, transfer money to people, and get alerts about fraudulent transactions. But, like anything related to money, they can be abused. Nowadays, thieves are not only snatching phones, but forcing their owners to transfer money to the thieves. This is not an isolated incident. How can you…
Continue reading →

A decade ago, I appeared on the 361 Podcast to give my advice about mobile security. This was the era of the iPhone 5 and Android KitKat. BlackBerry was trying to have (yet another) resurgence and Nokia was desperately trying to keep Windows Phone alive. What advice did I give then, and is it still relevant? Stay Sceptical In at number five is just stay sceptical. I mean, quite often, lots…
Continue reading →

You receive a call on your phone. The polite call centre worker on the line asks for you by name, and gives the name of your bank. They say they're calling from your bank's fraud department. "Yeah, right!" You think. Obvious scam, isn't it? You tell the caller to do unmentionable things to a goat. They sigh. "I can assure you I'm calling from Chase bank. I understand you're sceptical. I'll…
Continue reading →
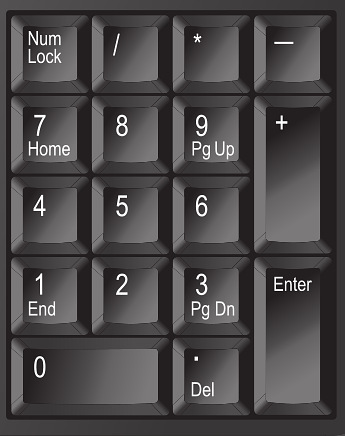
This has to be the most infuriating bug report I've ever submitted. I went to type in my 2FA code on a website - but no numbers appeared on screen. Obviously, I was an idiot and had forgotten to press the NumLock button. D'oh! I toggled it on and typed again. No numbers appeared. I switched to another tab, my numbers appeared when I typed them. So I was reasonably confident that my keyboard was…
Continue reading →

One of my most memorable experiences in the Civil Service was discussing link shortening services with a very friendly person from the Foreign and Commonwealth Office. I was trying to explain why link shortners like bit.ly and ow.ly weren't sensible for Government use. They didn't seem to particularly care about the privacy implications or the risk of phishing. I needed to take a different…
Continue reading →

It's never great to find out you're wrong, but that's how learning and personal growth happens. HTTP Message Signatures are hard. There are lots of complex parts and getting any aspect wrong means certain death. In a previous post, I wrote A simple(ish) guide to verifying HTTP Message Signatures in PHP. It turns out that it was too simple. And far too trusting. An HTTP Message Signature is a…
Continue reading →










