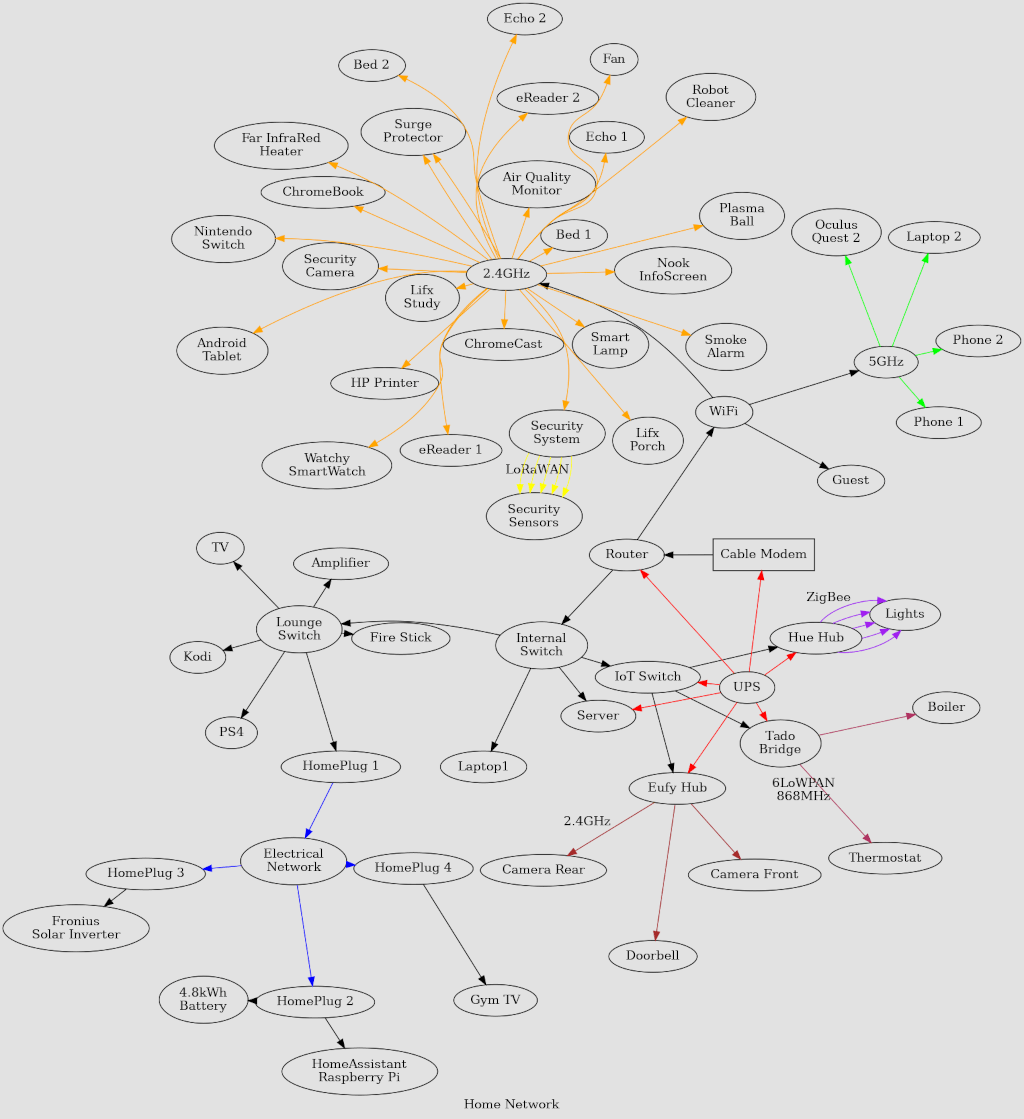
There's an absolutely delightfully bonkers post doing the rounds called "My Overkill Home Network" - which is a look into what happens when a computer geek goes feral and stuffs as many Internet connected thingamajigs in a living space. We're talking professional grade, rack mounted, doubly redundant, over-specced, equipment. Overkill is underselling it. I wondered how my home network looked in…
Continue reading →

The good folk at Nooie have sent me their 360 WiFi camera to review. Cost is usually £50 - but check the bottom of this post for a discount code. The design is gorgeous - and award winning. It's a sleek unit and, surprisingly, feels nice in the hand. It can store videos on an SD card (not included) or via the cloud. The app - which is pretty nice - also lets you view the camera when you're away …
Continue reading →

I was recently given 3 rather locked-down network cameras. Each camera was pre-programmed to communicate with a specific website, and only attach to a predefined wireless access point. Naturally, there was no supplied username or password. I thought about how I might get access. Using a man-in-the-middle attack to sniff the password, or trying to dump the firmware and examine that. Sadly,…
Continue reading →



