
Back in 2022, I wrote this rather grumpy post on Mastodon, the federated social media platform. @Edent@mastodon.socialTerence EdenMastodon enforces a "noreferrer" on all external links.I have mixed feelings about that.As a blogger, I want to see *where* visitors are coming from. I also like to see (and sometimes join in) with the conversations they're having.But, I get that people want privacy…
Continue reading →

It's never great to find out you're wrong, but that's how learning and personal growth happens. HTTP Message Signatures are hard. There are lots of complex parts and getting any aspect wrong means certain death. In a previous post, I wrote A simple(ish) guide to verifying HTTP Message Signatures in PHP. It turns out that it was too simple. And far too trusting. An HTTP Message Signature is a…
Continue reading →
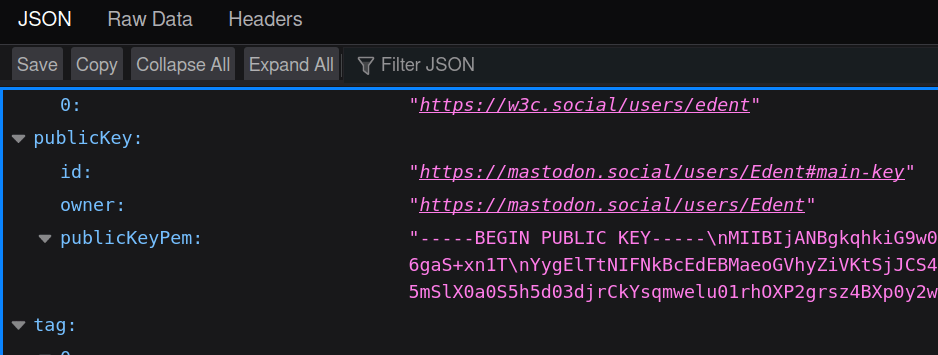
Mastodon makes heavy use of HTTP Message Signatures. They're a newish almost-standard which allows a server to verify that a request made to it came from the person who sent it. This is a quick example to show how to verify these signatures using PHP. I don't claim that it covers every use-case, and it is no-doubt missing some weird edge cases. But it successfully verifies messages sent by…
Continue reading →

I'm trying to get my head round HTTP Signatures as they're used extensively in the Fediverse. Conceptually, they're relatively straightforward. You send me a normal HTTP request. For example, you want to POST something to https://example.com/data You send me these headers: POST /data Host: example.com Date: Sat, 24 Feb 2024 14:43:48 GMT Accept-Encoding: gzip Digest:…
Continue reading →
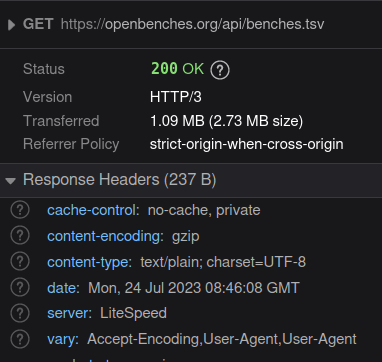
Perhaps this was obvious to you, but it wasn't to me. So I'm sharing in the hope that you don't spend an evening trying to trick your webserver into doing something stupid. For years, HTTP content has been served with gzip compression (gz). It's basically the same sort of compression algorithm you get in a .zip file. It's pretty good! But there's a new(er) compression algorithm called Brotli…
Continue reading →

Hyper-Text Transfer Protocol is, by some measure, the most popular way for computers to talk to each other on the Internet. Generally speaking, clients (like browsers) talk to servers using a set number of HTTP "verbs". This tells the server what sort of thing the client is trying to do. The two most popular verbs are probably POST - which lets you send data to a server - and GET - which lets…
Continue reading →
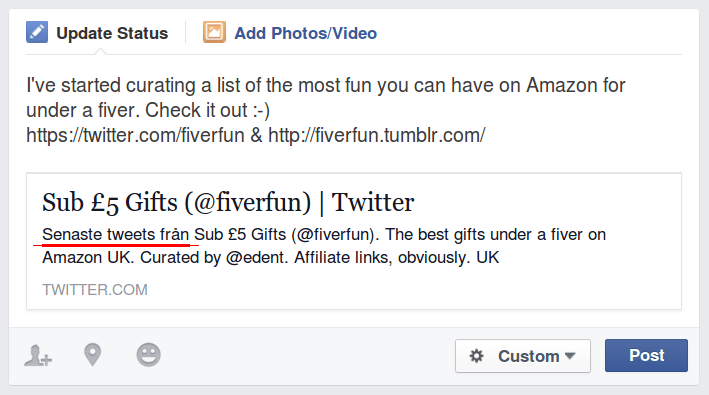
I've nothing against the Swedes. Lovely people. Sweden is the third-largest country in the European Union by area. But I'm not from there. Neither, as far as I am aware, is Facebook. But Twitter seems to think so. When I share a link to Twitter on Facebook, this (sometimes) happens. And sometimes, I get this delightfully mangled Unicode atrocity! So, what's going on? When Facebook wants…
Continue reading →

It is a truth universally acknowledged, that an ISP in possession of a good Internet connection must be in want of a customer. One would think that, in these capitalist times, ISPs would compete over who could provide the fastest speed, the best service, and the lowest price. Sadly, in the UK, our ISPs seem to compete on who can be slightly less awful than each other. Last night, I did what…
Continue reading →

I'm trying out the new Android app for Path - the new social networking service. I've discovered something rather troubling... Most of the app's communication with the Path servers is over SSL. This means that no-one can see the data you're sending and receiving. If there are snoops on your network, they will only be able to see the encrypted data flowing back and forth. In general, this is…
Continue reading →








