
Edward Snowden, the man who risked everything to expose the US government’s system of mass surveillance, reveals for the first time the story of his life, including how he helped to build that system and what motivated him to try to bring it down. I'm a civil servant in the UK. Luckily, I suppose, I don't often have access to TOP SECRET information. I suppose I could leak the canteen's lunch m…
Continue reading →

The Netherlands is a world leader in responsible disclosure. The Dutch like to resolve conflicts through a process of general consultation: the famous ‘polder model’. In this book, we hear from the hackers, system owners, IT specialists, managers, journalists, politicians and lawyers who have been key players in a number of prominent disclosures. Their stories offer a glimpse into the mys…
Continue reading →

I use a password manager. I have 2FA set up on everything. When an organisation asks me to set a recovery question, I generate a 32 character passphrase. I don't use my mother's maiden name or my first pet's birthday on anything sensitive. I monitor my email addresses for breaches, and I regularly check my credit file. I'm doing everything a geek can to protect their online life. Is it enough? …
Continue reading →

Tado is a brilliant smart thermostat. But their API is very poorly documented. This is an updated guide for 2019. I am indebted to Stephen C Phillips' original documentation. Getting started You will need: A Tado (duh!) Your Username (usually your email address) Your Password A Client Secret Getting the client secret I'm using this client secret:…
Continue reading →

Imagine the scenario. You're trying out some cool new Twitter app. It asks you to sign in via OAuth as per usual. You look through the permissions - phew - it doesn't want to access your Direct Messages. You authorise it - whereupon it promptly leaks to the world all your sexts, inappropriate jokes, and dank memes. Tragic! What's going on? Many years ago the official Twitter API keys were…
Continue reading →

A few years ago, I added WiFi to my Roomba using a 3rd party add-on. Sadly, it looks like Thinking Cleaner, the company which created the WiFi unit is no longer manufacturing them. But in their latest firmware release, they added a fun new option - the ability to make your Roomba sing! Terence Eden is on Mastodon@edentI've hacked @edent_roomba to obey its true master.(You'll want the volume up …
Continue reading →
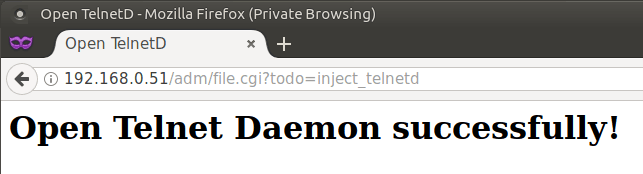
tldr; URL http://[IP]/adm/file.cgi?todo=inject_telnetd Telnet username root Telnet password Aq0+0009 History Four years ago to the day, I wrote an exposé of the hideous security failings of Sercomm IP Cameras. The blog has since attracted 200 comments - as people try to unlock their cameras, and find out what flaws they have. Despite my best efforts at contacting Sercomm - the OEM who …
Continue reading →

Last year I reverse engineered Renault's Electric Car API. One of the curious omissions was mileage - it just doesn't appear there. However! All is not lost. If you log in to your Renault Account - https://www.renault.co.uk/my-account/my-car.html - you'll get details back about your car including its make, model, date of next service, and mileage! Why isn't this in the regular API? Who knows. …
Continue reading →

I've found an interesting, but low severity, way for a malicious user to selectively deny access to specific GitHub issues and Pull Requests. This doesn't affect the whole site - just targeted pages. It doesn't require elevated permissions, nor any special skills. This is just GitHub punching itself in the face. Here's how it works. An attacker creates thousands of comments in their own…
Continue reading →

It's nearly Christmas! That means Secret Santa time at work, and the need for little stocking-filler gifts. But where can you find such cheap treats? Aha! I have created a service just for you! https://fiverfun.tumblr.com/ is my new(ish) project. It scours Amazon for the best and/or weirdest things for under a fiver! At the moment the site posts updates 3 times per day - and you can also…
Continue reading →
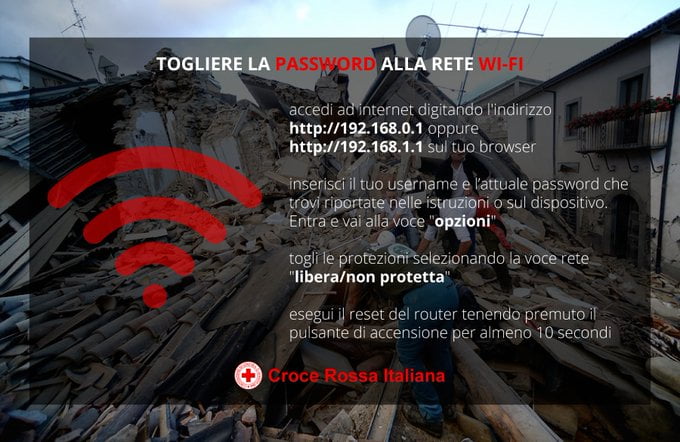
There has been a terrible natural disaster in Italy. A huge quake has broken a city. Rescue teams race to the scene to try to save lives and stabilise the situation. During the rescue efforts, the Italian Red Cross sends this tweet: Croce Rossa Italiana@crocerossa#Terremoto, per favorire comunicazioni e operazioni di soccorso vi invitiamo a togliere la password della rete wi-fi…
Continue reading →

This is a curated list of APIs which do not require usernames, passwords, access tokens, signing, accept-headers, or anything more complicated than sticking a URL in a browser. (This is an update to my post from two years ago.) When I introduce people to the concept of using RESTful APIs, they immediately get how powerful it is to retrieve information from the Internet and then manipulate it in…
Continue reading →











