
Humans are lazy. That's why we have computers; to do the boring work for us. I recently downloaded a file. The website said the file should have a SHA-256 hash of: ca978112ca1bbdcafac231b39a23dc4da786eff8147c4e72b9807785afee48bb So I ran sha256 filename on my machine. And then lazily compared the hashes. By which I mean "Yeah the first few characters match, as do the last few. It's probably…
Continue reading →
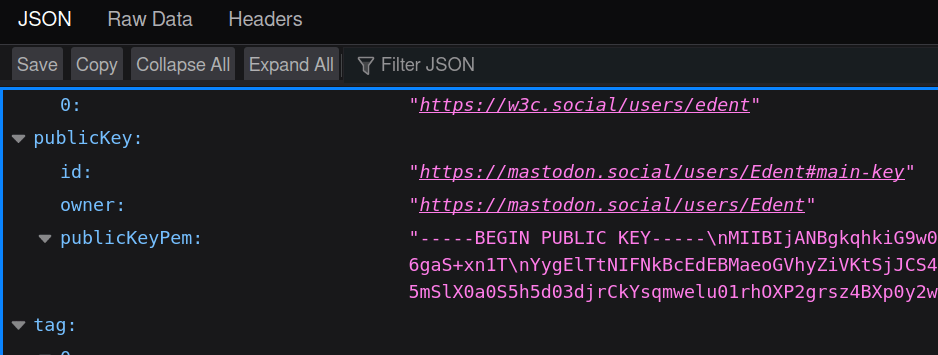
Mastodon makes heavy use of HTTP Message Signatures. They're a newish almost-standard which allows a server to verify that a request made to it came from the person who sent it. This is a quick example to show how to verify these signatures using PHP. I don't claim that it covers every use-case, and it is no-doubt missing some weird edge cases. But it successfully verifies messages sent by…
Continue reading →

Wouldn't it be good if digital currencies worked offline? I'm going to talk through a proposed user experience, and then discuss how it would work in practice. Let us imagine a future digital currency ₢. It might be fiat, it might be crypto, doesn't really matter. Alice loads up a smartcard with ₢100 and locks it. Alice gives Bob the smartcard. Bob uses offline verification to see that the sma…
Continue reading →

To understand this blog post, you need to know two things. There exists a class of numbers which are illegal in some jurisdictions. For example, a number may be copyrighted content, a decryption key, or other text considered illegal. There exists a class of algorithms which will take any arbitrary data and produce a fixed length text from it. This process is known as "hashing". These algorithms …
Continue reading →

Shamir's Secret Sharing (henceforth "SSS") is clever. Far too clever for most people to understand - but let's give it a go. Suppose you have a super-secure password for a Really Important Thing. Th15IsMyP4s5w0rd!123 You can remember this - because you're awesome. But it might be a good idea to share the password with someone else, just in case. Of course, if you share it with one person,…
Continue reading →

Twitter has a nifty new feature which allows you to schedule the publication of a Tweet. But, crucially, it doesn't let the reader know when the message was originally written. How can you, as a publisher, prove that you wrote a scheduled Tweet at a specific time? Here's one method. Write a Tweet which contains a timestamp - "This is my message 2020-08-17" Generate a hash of the message -…
Continue reading →

I'm going to start this discussion with the why and then move on to the how. Let's begin with a couple of user stories. As the recipient of some data, I want to verify that it hasn't been tampered with. and As the recipient of some data, I want to verify who originally published it. Here's why I think this is important. We are in an era of fake news. A screenshot can be easily altered. A…
Continue reading →

Every time someone mentions BlockChain, I have to down my drink. Those are the rules. You see, most uses of Distributed Ledger are really just a way to get people interested in cryptographic signing. There's lots of money and attention flowing to projects which have no need to publish to an energy-inefficient global database. They would be better suited to public-key cryptography. Let me give…
Continue reading →





