
I maintain a a test-suite for TOTP codes. It contains a bunch of codes which adhere to the specification, some of which stretch it to breaking point, and some that are completely invalid. These codes are a good starting point for checking whether a 2FA / MFA app works correctly. Proton have release a swish new authenticator app for Android, iOS, Mac, Linux and Windows. Sadly, their open source…
Continue reading →

There's a disturbing article in The Guardian about a person who was on the receiving end of a successful cybersecurity attack. EE texted to say they had processed my sim activation request, and the new sim would be active in 24 hours. I was told to contact them if I hadn’t requested this. I hadn’t, so I did so immediately. Twenty-four hours later, my mobile stopped working and money was wit…
Continue reading →

Some ideas are timeless. Back in 2004, an anonymous genius set up "FobCam". Tired of having to carry around an RSA SecurID token everywhere, our hero simply left the fob at home with an early webcam pointing at it. And then left the page open for all to see. Security expert Bruce Schneier approved of this trade-off between security and usability - saying what we're all thinking: Here’s a guy w…
Continue reading →
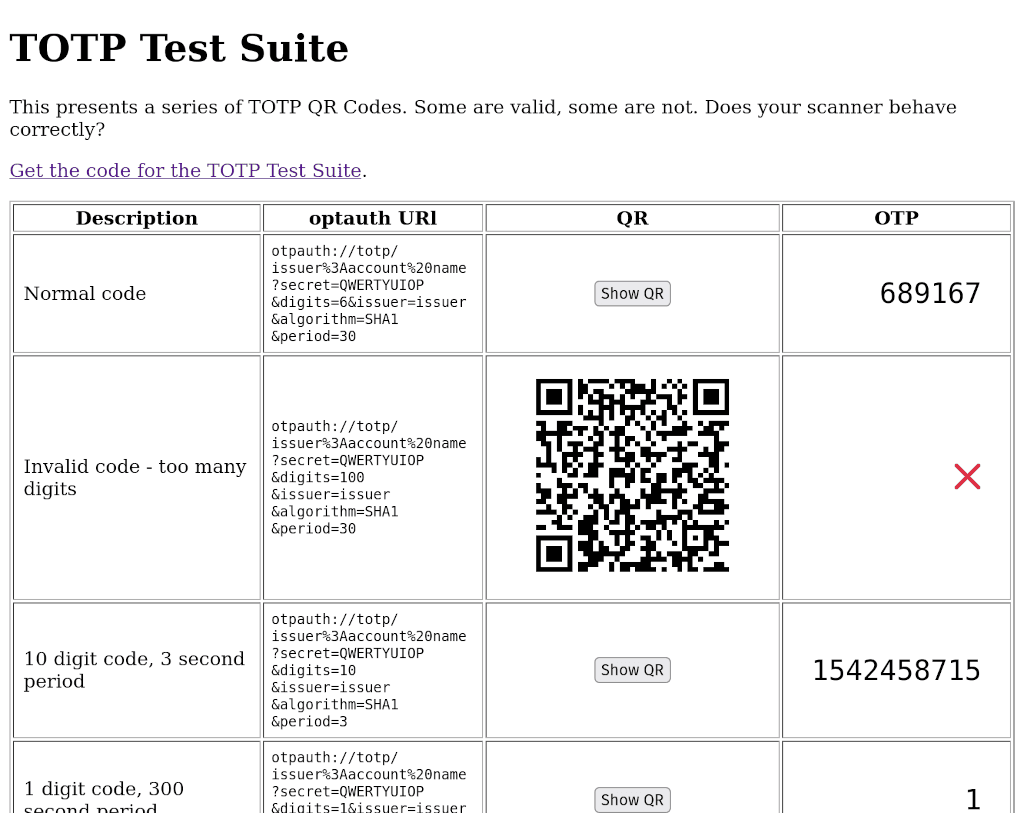
Because I'm a massive nerd, I actually try to read specification documents. As I've ranted ad nauseam before, the current TOTP spec is irresponsibly obsolete. The three major implementations of the spec - Google, Apple, and Yubico - all subtly disagree on how it should be implemented. Every other MFA app has their own idiosyncratic variants. The official RFC is infuriatingly vague. That's no…
Continue reading →

Here's a "fun" thought experiment. Imagine a website which let you sign in using only your username and TOTP code. No passwords. No magic links emailed to you. No FIDO tokens. No codes via SMS. Just a TOTP generated and displayed on your device. Is that useful? Sensible? Practical? It's certainly technically possible. Store the username, store the TOTP seed, done. Your users can now log in. …
Continue reading →

Yeah. Yeah, I reckon so. Under the right circumstances. Multi-Factor Authentication (MFA, 2FA, TOTP, whatever you want to call it) is pretty nifty. You scan a QR code and your phone will continually generate a set of one-time passwords which are synchronised with a remote server. There's nothing stopping multiple people from scanning that QR code! They will each have the same password displayed …
Continue reading →

Recently, WordPress got in contact with me to say they suspect that my password was exposed in some sort of data breach. Well, it's a day ending with a "y" - so of course some scumbag has pilfered my digital identity. WordPress mandated that I change my password. But was that really necessary? Firstly, the password was uniquely generated by my password manager. It isn't re-used anywhere else.…
Continue reading →

I have mixed feelings about Multi-Factor Authentication. I get why it is necessary to rely on something which isn't a password but - let's be honest here - it is a pain juggling between SMS, TOTP apps, proprietary apps, and magic links. I'm also not a fan of PassKeys. It feels weird to me that my computer is the password. I get the theoretical way it works - but it rubs me up the wrong way. So, …
Continue reading →

I'm big enough to admit when I make a mistake. A few days ago I had a bit of a rant on Mastodon about how PayPal was encouraging browsers to remember 2FA codes. I'd tried to log in to PayPal, went to enter my 2FA code and was presented with this: But, this isn't PayPal's fault! Let's take a look at the code behind each input: <input name="otpCode-0" id="ci-otpCode-0" …
Continue reading →

Behold! Thanks to the power of the Watchy development platform, I now have all my 2FA codes available at the flick of my wrist! HOWTO This uses Luca Dentella's TOTP-Arduino library. You will need a pre-shared secret which is then converted into a Hex array. Use the OTP Tool for Arduino TOTP Library to get the Hex array, Base32 Encoded Key, and a QR Code to scan into your normal TOTP…
Continue reading →

The other day, a company sent me a 2FA code which was only four digits long. I'll admit, this weirded me out. Surely 4 is just far too short. Right? I think almost every 2FA code I've seen has been 6 digits long. Even back in the days of carrying one of those physical RSA fobs, 6 has been the magic number. But why? A 2FA code is meant to prevent a specific class of problem. If an attacker…
Continue reading →

Imagine… Last night, lightning struck our house and burned it down. I escaped wearing only my nightclothes. In an instant, everything was vaporised. Laptop? Cinders. Phone? Ashes. Home server? A smouldering wreck. Yubikey? A charred chunk of gristle. This presents something of a problem. In order to recover my digital life, I need to be able to log in to things. This means I need to know my u…
Continue reading →








