
I'm an absolute sucker for Claire North's books. She has an almost supernatural ability to weave an intricate yet satisfying tale, all while leaving the reader hungry for more. Ithaca presents a God's-eye-view of the story of Penelope. It's a fast, furious, and feminist story which plunges us straight into the middle of the Greek melodrama. Kenamon takes his time to consider this. Penelope does …
Continue reading →

Shakespeare, famously, shunned computers. Like some sort of retro hipster, he didn't write his plays on a laptop, refused to use spellcheck, and didn't register his copyright on the blockchain. Lord, what fools these mortals be! What would Shakespeare's plays have been like if their characters understood basic cybersecurity? Now, it is true that very few of his plays feature computers, but…
Continue reading →

HTML documents have the concept of an alternate representation of the document. For example, a page's header might say: <link rel="alternate" type="application/rss+xml" href="https://shkspr.mobi/blog/feed"> That tells you there's an alternative representation of the page, what sort of content it is, and where it is located. That's nice. But it's hard for a browser to tell the user what that…
Continue reading →

I recently went up to a conference in a city I'd never visited before. As I was sat on the train up, I wondered if any of the other passengers were also going to the conference. It's a bit socially awkward and creepy to go up to a bunch of strangers and interrogate them about their plans for the weekend. So I sat in silence. Back when everyone was on Twitter, there was a reasonable chance that…
Continue reading →

I've bumped in to Ken Banks a few times over my career - and he has always been a kind, inspiring, and dedicated chap. How did he get that way? This book is part autobiography and part an explanation about how people can find purpose in life. It is refreshingly secular on the latter, and curiously impersonal on the former. While Ken's childhood family is recounted in great detail, his wife and…
Continue reading →

That's it. That's the post. Fine! I'll expand a little more. Large Language Models are a type of Artificial Intelligence. They can read text, parse it, process it using the known rules of English, and then regurgitate parts of it on demand. This means they can read and parse a question like "In Python, how do I add two numbers together?" and then read and parse the Python documentation. It…
Continue reading →

Sometimes, you want to stop scripts running only on specific domains. The best way to do that, I think, is with uBlock Origin - a free and fast ad-blocker. On the desktop version, it's simple to block scripts. Click the plugin icon, then click the disable scripts button. But on mobile it's a little more complicated. Here's how to do it on the Android version of Firefox. Install Firefox. Then …
Continue reading →

There's a law in the USA called the DMCA - Digital Millennium Copyright Act. Amongst its myriad provisions is the ability for copyright holders to send takedown notices to service providers. If someone has ripped off your content, you can send them a legal letter saying "take that down". People often send DMCA requests to Google saying "this site has stolen my copyrighted content - please remove …
Continue reading →

If you explore this blog's archives, you'll see that I've been blogging continuously every day since the start of 2020. Before that, I was blogging every month since mid-2008. Today, I am very hungover. Although I usually write a bunch of posts a few days and weeks in advance, I find myself looking at my publishing calendar and seeing it blissfully empty. Part of the reason I blog is that I…
Continue reading →

Imagine, just for a moment, you and your friends decide to travel in time. In order to make sure you can authenticate your communications with each other, you set up a shared Time-based One Time Password (TOTP). The TOTP algorithm uses a Hash-based Message Authentication Code (HMAC). The hash is calculated from a shared key and a time-based component. The key is a short string of characters.…
Continue reading →

This is a retropost. It was written in July 2021, but published after I had left the Civil Service. An MP has written to the Chancellor of the Duchy of Lancaster asking about some work our department is doing. This is all rather usual for Government business. In the letter, the MP mentions me. By name. This is decidedly unusual! Civil Servants at my level are anonymous, interchangeable cogs…
Continue reading →
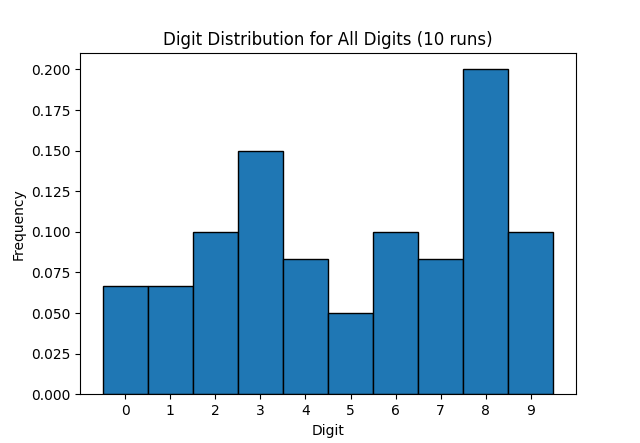
I'm pretty sure that the 2FA codes generated by my bank's TOTP app have a bias towards the number 8 - because eight is an auspicious number. But is that just my stupid meaty brain noticing patterns where none exist? The TOTP algorithm uses HMAC, which in turn uses SHA-1. My aforementioned brain is not clever enough to understand how that works. Although bigger, meatier brains have assured me it …
Continue reading →











