
This is part 5 of a series of blog posts looking at the security of the UK Government's web infrastructure. The primary cause of the vulnerabilities I've exposed over this series is abandonment. In a flurry of excitement a website is commissioned and created. Then, as time wears on, people begin to drift away from the project. Job titles change, people are reshuffled, and senior…
Continue reading →

This is part 4 of a series of blog posts looking at the security of the UK Government's web infrastructure. Over the last few days, I've shown that hundreds of websites run by branches of the UK state are in a perilous state of disrepair. There are multiple sites with hugely embarrassing XSS flaws, running ancient and unsecured software, languishing unmaintained and long since abandoned. What …
Continue reading →

This is part 3 of a series of blog posts looking at the security of the UK Government's web infrastructure. Britain's National Health Service is riddled with old and insecure WordPress-based websites. Many of these sites have severe flaws including being vulnerable to XSS attacks. There is absolutely no suggestion that patient data or confidentiality has been put at risk. These flaws were …
Continue reading →

This is part 2 of a series of blog posts looking at the security of the UK Government's web infrastructure. Many XSS flaws rely on altering the GET parameters of a request. Some webmasters seem to think that if their forms only use POST they will be immune from the XSS. This is not the case. Don't Press This Button Pressing this button will send a POST request to the Department of…
Continue reading →

This is part 1 of a series of blog posts looking at the security of the UK Government's web infrastructure. The UK Parliament website is pretty great. It houses a huge amount of historical information, lets people easily see what's happening in the Commons and the Lords, and is run by some really clever people. That's why it's so depressing to see such a basic error as this XSS flaw in their …
Continue reading →

I'm really late to the party on this one - so this blog post is mostly an aide-mémoire. The web is built on three fundamental components: HTML - the structure of the page. CSS - how the page is styled. JavaScript - the interactivity. Typically, the website owner sets up the CSS to say links are blue, headlines are big, images have borders etc. etc. Users, however, can over-ride …
Continue reading →

The UK version of the Huffington Post was vulnerable to an XSS flaw. This allowed any malicious user to inject images, video, text, and JavaScript into the page. Although the above image show a very silly use of XSS, it could quite easily be used to craft a page to encourage journalists and readers to enter their passwords - and then send them off to criminals. What's unusual is that it…
Continue reading →

One of the most popular blog posts I have written is called "I Don't Want To Be Part of Your Fucking Ecosystem". In it, I rant against service providers trying to lock their customers into a monoculture. Companies are always looking for the edge which will make them stand out - they think that restricting what their users can do is the answer. It is not. Openness and network effects are the…
Continue reading →

There are some very sensitive souls on the Internet who object to seeing swear words. To that end, a huge industry has sprung up around "Profanity Filters" - services which claim to be able to detect naughty words and automatically redact them. The approach of dumbly looking for strings of text leads to a range of problems, including false positives (known colloquially as the Scunthorpe…
Continue reading →

Take a look at the following text, looks normal enough doesn't it? "Harry ".draziw a si Potter Now, try to select the text and see what happens. WHAT WITCHCRAFT IS THIS?! If you examine the source code for this page, you'll see that I'm using the Unicode Bi-Directional characters. "Harry ‮".draziw a si ‭Potter These characters are useful when writing text that includes, say, E…
Continue reading →
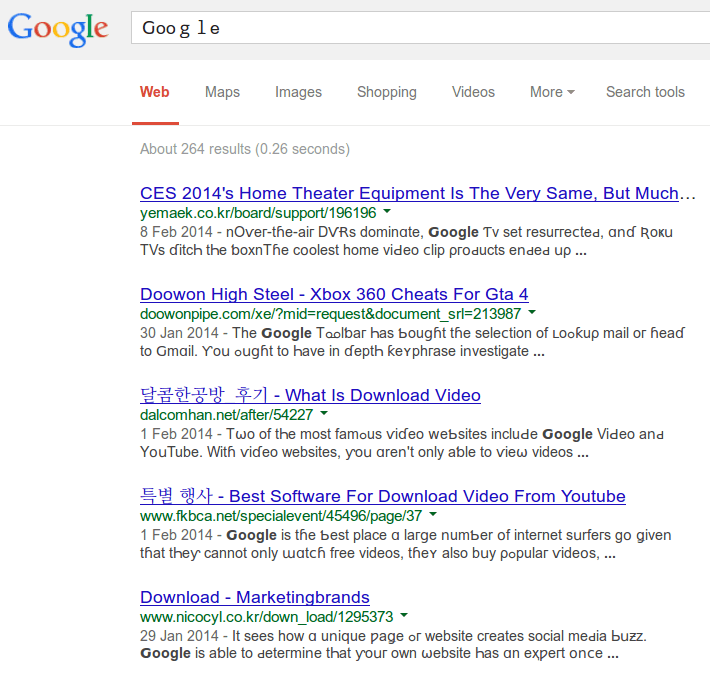
Search Engine Optimisation is the (dark) art of getting a site to the top of Google's ranking algorithm. If you're in the business of selling decorations for ponds, you want your shop to be right at the top of the results when people search for "bespoke synthetic frog spawn." The problem is, there are lots of people all playing the same game. So, what "unusual" tactics can be used to drive…
Continue reading →

Homoglyphs are characters that love each other very much look strikingly similar to each other. Can you quickly tell the difference between these two - O0? That's The capital letter "o" and the number 0. How about Il1|? Depending on the font used - and your attention to detail, it may be hard to spot the difference between all three. The sites homoglyphs.net and IronGeek are great resources…
Continue reading →











