
I remember the first time I saw a Swastika in India. It was gaudy red, painted on the back of a dusty yellow moped. The driver wore a helmet, but the woman riding pillion had only her sari to protect her head. India is different. The rules of the road are different. The languages are different. The colours, spices, and clichés are different. Over there, the स्वस्तिक is a symbol of auspiciou…
Continue reading →

I had dinner with the outgoing editor of The Guardian the other night. Clever chap, sure he'll go far in life. The Guardian is very hot on security. Many of their writers have PGP keys which they publicly advertise. In theory, that's great (complaints about PGP notwithstanding) - but the reality shows just how tricky it is to act in a security conscious manner. Have a look at Alan's Twitter…
Continue reading →

Recently I've been plagued with Tweets saying that I'm "trending in London." As flattering as that is, it's not true. There appears to be a network of Twitter bots which are randomly repeating other people's tweets, ripping off avatars and bios, and generally causing a nuisance. Looking at the users' Twitter name, I don't think it's unreasonable to think that "ekip_uhokoqeq" and…
Continue reading →

There are two very clear signs that I'm getting old. The first is that I bought a domestic robot to help me with the chores. The second is that, rather than spending my evenings and weekends reading decades old forum postings, reverse engineering serial interfaces, and soldering components together - I plunked €99 on a bit of kit which "just works". Enter the Thinking Cleaner - it's a r…
Continue reading →

(An adaptation of my earlier blog post on the same topic.) This is a case study focusing on the usability of encryption systems as used by political dissidents in Apartheid era South Africa. Background - South Africa Between 1948 and 1994, the nation of South Africa was ruled by an ethnically white minority. They set in place a system of government – known as Apartheid - which suppressed, b…
Continue reading →

Last week I was on In The Abstract - a science podcast - along with the very funny Francesca Day , the mediumly funny Tara Clarke, and the just-funny-enough Steve Pritchard. During the talk, I completely forget the name of the Rosetta Disc and made several legally doubtful slurs against Elon Musk and Mark Zuckerberg. Stick it in your ears - 🔊 February 2015🎤 In The Abstract 💾 Download th…
Continue reading →

Last week I was on the In The Abstract podcast. I came up with a curious idea. If I were Tom Scott, I'd turn this into a performance piece - instead, here's a short and entirely fictional story. Facebook knew you were in love a long time before you did. It noticed you scrolling back through her timeline. Every millisecond lingering over the photos of her at the beach was faithfully logged. …
Continue reading →

The two big memes of our entrepreneurial age are Go big, or go home! And Ever tried? Ever failed? No matter. Try Again. Fail again. Fail better. Samuel Beckett Well, I've failed and now I'm heading home. Last year I applied for a place on a Master's programme at the Oxford Internet Institute. I was desperate to spend a year studying the Social Science of the Internet. It felt like it was…
Continue reading →
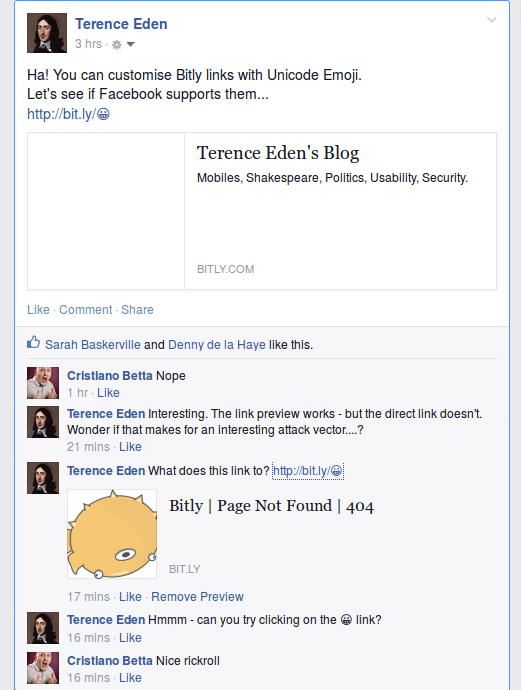
2025 Update - Bitly removed the ability to create emoji links, so some of these links are now dead. Facebook rewrite URLs with Unicode in the path - this is not best practice and could be dangerous. It is possible to create a URL like http://bit.ly/😀 - the Unicode characters are valid in the path. The URL Encoded representation is : bit.ly/%F0%9F%98%80 Facebook mangles these URLs in such a wa…
Continue reading →

I have a (very minor and polite) disagreement with Matt Gemmel's argument against dates in URLs. Before I start, let me be very clear; your blog = your rules. If you want to write your URLs as a series of Emoji or in Klingon - go right ahead. There really is no such thing as "best practice" - only personal preference and observed behaviour. That said... Here's my case for keeping dates in…
Continue reading →
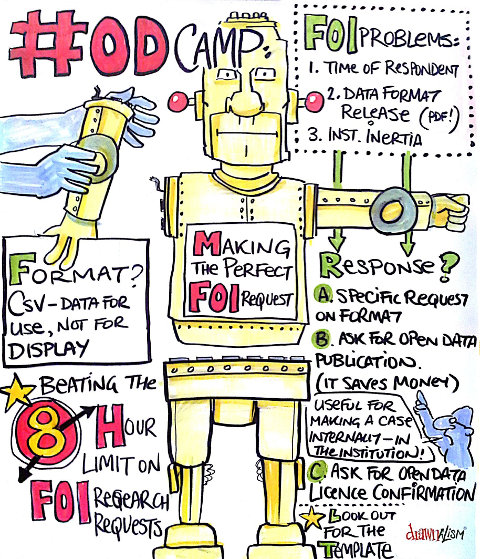
One of the sessions I lead at Open Data Camp was "Open Data Horror Stories" - we talked about some of the disasters we've had when requesting or using Open Data. This lead on to a session ran by Gaia Marcus on how to create the "perfect" FOI request. This is not an exhaustive guide to making FOI requests. I strongly suggest that you read WhatDoTheyKnow's recommendations and FOI Man's Top Ten …
Continue reading →
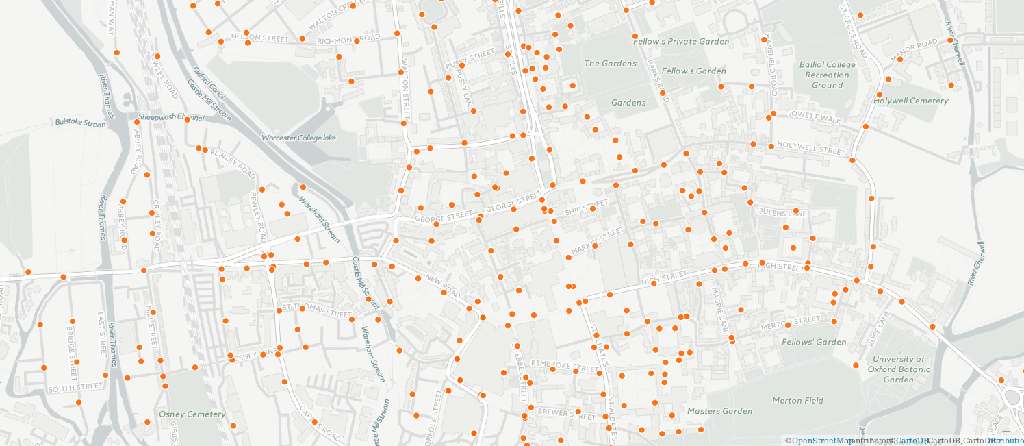
(Inspired by a session at Open Data Camp called "Open Data Horror Stories") I was having an argument spirited discussion with my friend John the other day. He was sympathising with Tony Blair's regrets over the introduction of the Freedom of Information Act. Apparently, FOI requests put too great a strain on departments and government bodies. Not only is there a huge cost of compliance, but…
Continue reading →











