MSc Assignment 6 - Professional Practise 2 - Blockchain
I'm doing an apprenticeship MSc in Digital Technology. In the spirit of openness, I'm blogging my research and my assignments.
This is my final assignment! It's from the PP2 module - where I take some CPD related to my profession. I picked Blockchain. Because I hate myself.
I've blogged about the course itself. The middle two parts of this paper are about that - why I chose it and how I put it into practice. The first and fourth parts are, as far as I can tell, unrelated. We have to write about reflection in the workplace. I am not very introspective, and I don't really enjoy it. So I found as many papers as I could to dispute the premise. The final part was about a modern issue of interest to professionals - which at least had the advantage of being interesting.
I was overjoyed with a mark of 81% (in the English system 50% is a pass, 60% is a commendation, 70% is distinction). That takes my on-course average to a shade over 71%. I wonder if I can keep that up for the final project?
I used my algorithm to write an assignment to complete this.
A few disclaimers:
- I don't claim it to be brilliant. I am not very good at academic-style writing.
- It is fairly inaccurate. Many of the concepts on reflection were not relevant to my workplace, so there is a lot of fudging.
- This isn't how I'd write a normal document for work - and the facts have not been independently verified.
- This isn't the policy of my employer, nor does it represent their opinions. It has only been assessed from an academic point of view.
- It has not been peer reviewed, nor are the data guaranteed to be an accurate reflection of reality. Cite at your own peril.
- I've quickly converted this from Google Docs + Zotero into MarkDown. Who knows what weird formatting that'll introduce!
- All references are clickable - going straight to the source. Reference list is at the end, most links converted using DOI2HT.ML.
And, once more, this is not official policy. It was not commissioned by anyone. It is an academic exercise. Adjust your expectations accordingly.
1. A critical review of three reflective models and selection of one of these to use to support your reflection in the assignment
1.1 Review of 3 models
The author has reviewed the assigned literature and beyond in order to compare multiple models of reflection. Three models are evaluated by the author in Table 1.
Ideally, reflection would allow professionals to pair with more experienced practitioners and compare the effectiveness of their learning (Oluwatoyin, 2015). In the author's experience, it is not the model which is important - but rather working in a team to understand how to learn and how others learn.
| Table 1 | ERA Cycle ( Jasper, 2013) | Double Loop Learning ( Argyris, 1977) | DIEP ( Rogers, 2001) |
|
Model |
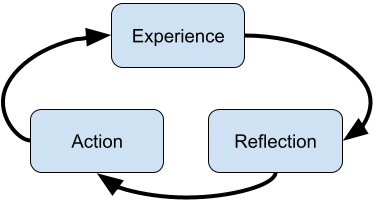
|
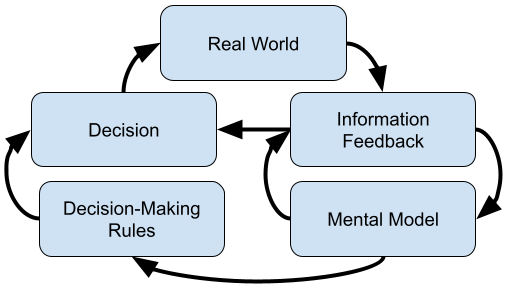
|
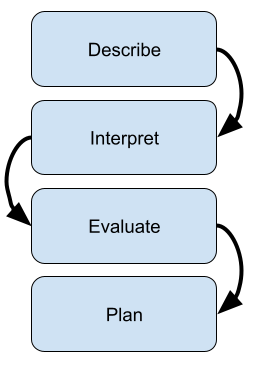
|
|
Strengths |
Simple model. | Part of many Agile processes (
Richardson, 2014).
Suitable for business processes. |
Structured model.
Suitable for teams and individuals. |
|
Weaknesses |
Content free.
Offers no structure to the reflection. |
Not a "silver bullet" (
Crossan, 2003).
Risk of undermining corporate objectives (Soeters, 2022). |
Not universally applicable.
No feedback loop. |
1.2 Evaluation of the effectiveness of the chosen module based on PP1
The author chose the DIEP reflective model for PP1 but did not find it as effective as hoped. Having extensively reviewed the literature, the author found strong evidence of the widespread use of reflective practice in healthcare (Norrie et al., 2012) but little convincing evidence that reflection is effective in digital organisations (Dors et al., 2020).
Additionally, evidence shows reflective practice rarely leads to altered behaviours (Granan, 2016). In two decades of work experience, the author has found specific models of reflection tend not to be the cause of improvements. Instead, modern digital employees are better served by concentrating on the act of reflecting as a team (Jha and Vazirani, 2021).
Others have concluded that reflection is "a contemporary label for an aspect of human thinking processes whose popularity has exceeded its conceptual and theoretical grasp" (Kompf and Bond, 1995) - although this is disputed by those who think these obstacles can be overcome (Denton, 2011). Many researchers think forcing reflection on learners is "futile" due to their desire to be seen as competent (McGarr and Ó Gallchóir, 2020) and the institutional disincentives to be honest (Hobbs, 2007). Others recognise that although isolated reflection is an "ambiguous moral exercise" (Hargreaves, 2004) it may be useful in a "safe and supportive environment" (Fernsten and Fernsten, 2005).
1.3 Comparisons with other models
In the author's opinion, there is little to distinguish between any of the popular reflective models. They only differ in the amount of administrative steps each theorist is willing to dedicate to "navel-gazing" (Andresen and Emerson, 1991).
As noted by Smith & Martin, most professionals in the author's field introduced to reflective practice do not continue with it when given a free choice (Smith and Martin, 2014). This failure to adopt reflection is present in many workplaces (Eaton, 2016). Furthermore, there is evidence showing forced reflective practice may be detrimental to the practitioner's development in the modern workplace (Hargreaves, 2004). Again, this is found across various types of profession (Wong, Whitcombe and Boniface, 2016).
While reflective practice is well accepted in fields like medicine (Ooi, Fisher and Coker, 2021), the author agrees with the critics who argue that there is a "marked dearth of evidence that reflective practice techniques yield more reflective practitioners" (Lilienfeld and Basterfield, 2020).
1.4 The relevance of the chosen model to the context of PP2
Due to the ever-changing nature of work, the modern employee must be prepared for lifelong learning. Reflecting on the learning process and achievements is thought to be critical to future employability (Helyer, 2015). However, the use of reflection has uncertain effectiveness (Mann, Gordon and MacLeod, 2009) and many novice practitioners find the application of reflection to be daunting (Walker et al., 2013).
There is a "theory practice gap" identified by Schön (Schön, 1987) - whereby practitioners aren't able to effectively utilise reflection despite repeated exposure to theoretical concepts. Therefore, the author has chosen to use DIEP as it is a familiar model which can be quickly iterated to uncover new ways of reflecting. The author's current working environment expects all processes to be rapidly iterative.
2. A discussion of the selection of CPD in relation to the wider technical area, the context within your organisation, and my specific role
2.1 Description
I chose a course which was designed to upskill me in an interesting new technology - Blockchain. It covered the basics of the technology and its applications.
Early Blockchain proponents said that "the digital revolution challenges us to develop new institutions in a much shorter period of time" (Szabo, 1997). As a new member of a team inside a newly formed institution, I wanted to see if Blockchain could help deliver rapid change. This fits with my organisation's recently published business objectives (Cabinet Office, 2021).
2.2 Relevance
There are various embryonic Blockchain projects within my organisation. For example the Royal Mint is planning a series of Non-Fungible Tokens (Sparkes, 2022) and legislators are interested in the possibilities of Blockchain voting (Holmes, 2022).
As this is a relatively new field, the Civil Service finds itself with a lack of expertise in this technology. With intense scrutiny from media, industry, and academia, I felt it was important to increase my knowledge in this area. Given the interest from senior stakeholders, I need to be able to swiftly and accurately evaluate future projects. As part of my organisation's 2025 roadmap, they have committed to exploring this technology (Wheeler, 2022), so it is of high relevance to my job.
2.3 Context
Our team deals with the security of critical national infrastructure - specifically, the integrity of the .gov.uk domain name ecosystem.
There are multiple parties with interest in this system, all with varying levels of trust in each other, which makes distributed technology particularly pertinent. There are also novel social, ethical, and legal implications which I wanted to explore, e.g. whether the immutability of Blockchain is compatible with our data protection obligations under GDPR. I also had to consider the ethical implications of endorsing a technology with a disastrous effect on climate change (Onat et al., 2021).
Finally, there are mixed views of Blockchain technologies, and many associate it primarily with scams (Phan, Li and Mentzer, 2019). I wanted to see if these issues would be a barrier to adoption.
2.4 Author's Role
I am a noted sceptic of Blockchain technology (Ross, Cretu and Lemieux, 2021) and wanted to provide more rigour to my analyses.
As part of my Personal Development Plan, I am looking for new technologies which will enhance my skills, reputation, and employability. With a predicted surge in Blockchain roles (Ge et al., 2021), I thought this CPD would help increase my employability and allow me to bring new skills to my employers.
2.5 Possible Alternatives
In conjunction with my team, I investigated other courses which may have been suitable. As indicated in my PDP, I have an identified learning need to acquire more practical knowledge of the fundamentals of DNS infrastructure. On-the-job training was thought to be a better route to learning these skills because they rely heavily on practical application rather than theoretical understanding. Some of the "soft skills" which I need to develop were not available as directed CPD. Finally, I investigated whether a series of video lectures on Blockchain would be acceptable (Gensler, 2018) - but they were unaccredited.
2.6 Evaluation
On reflection, I found this to be an extremely disappointing course. Although it taught me the key algorithms and history of the technology, the set text book was poorly written, with multiple factual and grammatical mistakes. Large parts of the book were plagiarised from other books and websites (Bavisi, 2021).
After discussing the course content with my peers, it became clear to me how much of the information was presented uncritically and without evidence. The course was provided by an organisation with a self-professed history of chauvinism and misogyny (Dallaway, 2021). While there were some interesting technical elements in the text, there was a lack of academic rigour which led to questionable conclusions.
3. An overview of how the CPD has been applied within my professional practice
3.1 An overview of the CPD
The course was a self-directed course designed to give an overview of various Blockchain technologies. It provided several case studies describing where this technology has been found useful, and mistakes which have been made with it.
It also discussed the basics of the Solidity programming language and how it can be used to implement "smart contracts". There was some investigation of environmental impacts, and which industries are ripe for disruption.
There was very little critical reflection on the flaws of the technology, and only a brief mention of the fraud it has facilitated (Trozze et al., 2022).
I learned the theories behind Blockchain, the programming languages used to construct Smart Contracts, and several practical use-cases.
3.2 Identification of specific projects for which this CPD has had an impact
My starting point was the flowchart created by the National Institute of Standards and Technology (NIST) - see Figure 01.
Using this tool, I identified a project requiring shared data, which were immutable and didn't contain sensitive data, contributed by multiple parties, and where no single entity could be in control, resulting in a tamper-proof log of data. An engagement exercise was carried out with stakeholders to see if there was sufficient interest to create a proof-of-concept.
Figure 01 - Flowchart from NISTIR 8202
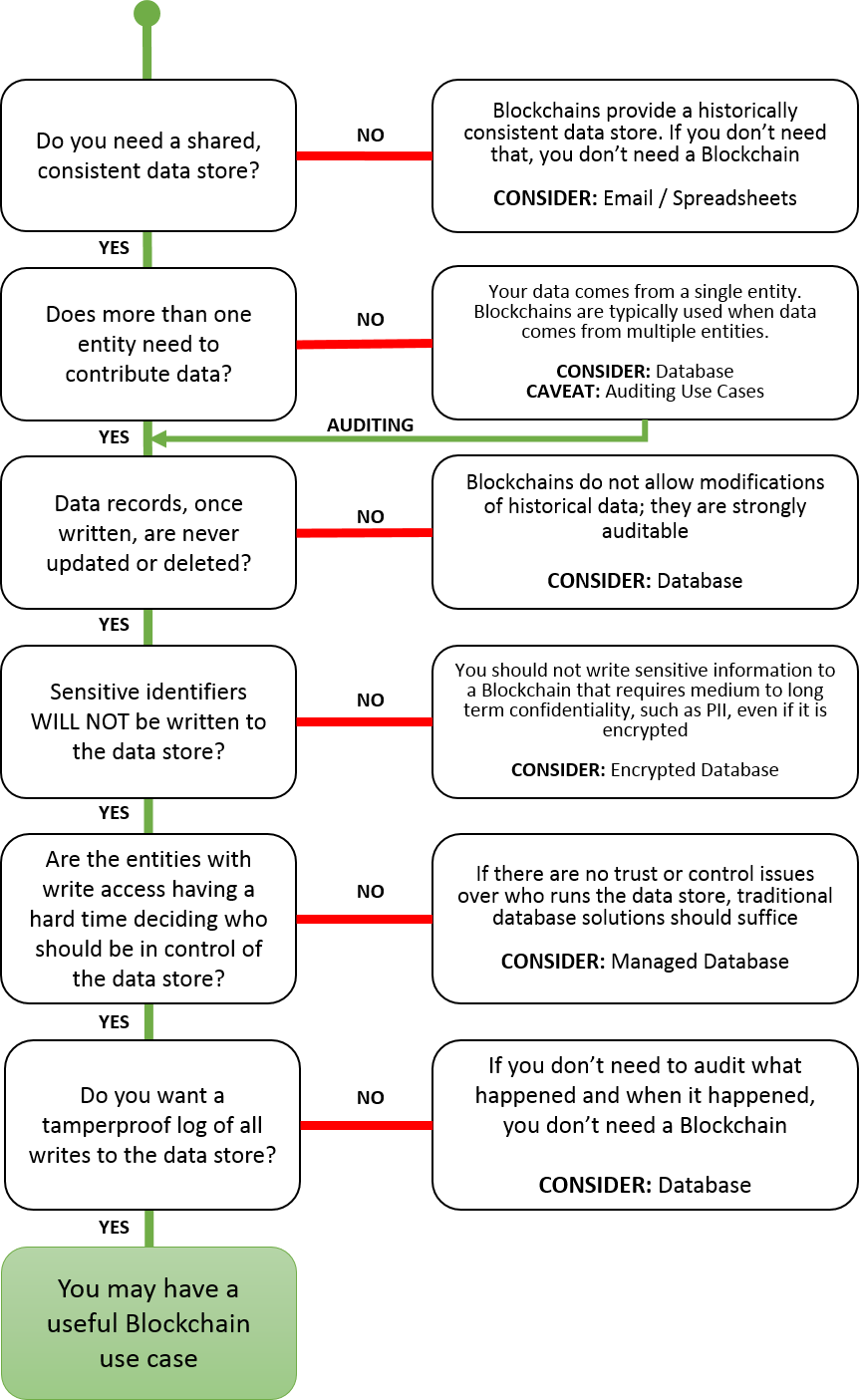 The flowchart presented in NISTIR 8202 demonstrates reasons to adopt Blockchain (Yaga et al., 2018)
The flowchart presented in NISTIR 8202 demonstrates reasons to adopt Blockchain (Yaga et al., 2018)
The background to the issue faced derives from the complicated constitution of the United Kingdom. The UK is often described as a country of four nations (Adenuga and Ogunduyile, 2020), so our service encompasses the top-level domains of .uk, .wales / .cymru, and .scot (note, there is no TLD for N. Ireland (Webster, 2019)).
There are also TLDs for Crown Dependencies and Overseas Territories, which are outside our purview. Of academic interest is the .gb TLD which represents Great Britain, but is all but abandoned (Martins dos Santos and Anastácio, 2022).
The multi-stakeholder group is complex; including separate legal and regulatory frameworks in each jurisdiction, various devolved competencies, and independence of operation which is both de facto and de jure. This is the perfect environment to see whether a "trustless" technology like Blockchain can thrive when applied to the seemingly anodyne task of collating DNS records.
Therefore, the CPD was applied to a project investigating the feasibility of using a permissioned blockchain to record DNS changes to critical domains.
3.3 Discussion and evidence of technical knowledge acquired in relation to the targeted apprenticeship standard.
A proof-of-concept model was created based around the concept of a Private blockchain.
A Private chain allows trusted participants to maintain a shared ledger i.e. it is not open to the public. This means it is quicker to iterate architectural design choices once all participants have agreed to them. It also requires less security against malicious nodes in the network. I learned that there are some disadvantages - because of the small number of participants it is hard to defend against multiple malicious nodes.
There are multiple ways to generate consensus in Blockchains. The course taught me that "Proof of Work" is the predominant method in public chains, but there are several more suitable consensus algorithms for Private Chains (Pahlajani, Kshirsagar and Pachghare, 2019).
Given the specific and limited number of participants, I decided to investigate voting consensus. This allows a pre-agreed quorum of voters to sign transactions to mark them as valid.
Any database - whether traditional or decentralised - needs to be designed for future requirements. While the proponents of Blockchain highlight the disparate nature of nodes as being essential for performance, I learned from a closer reading of the literature that there are several complex scaling issues related to how a Blockchain grows (Croman et al., 2016).
My investigation found that a Distributed Ledger would face two main scaling challenges. Firstly, the time taken to add records would slow down with every insertion operation due to the need to revalidate the entire chain. Secondly, consensus seeking algorithms introduce latency depending on the responsiveness of other nodes. Both of these are problematic for services which need rapid updates.
An interesting and innovative feature of some Blockchains are so-called "smart contracts" (Schuster, 2021). These can be thought of as stored procedures - code which exists on the chain and is executed by nodes under specified circumstances. For example, a smart contract could execute a transaction (writing data to the chain) when the chain reaches a specific state. In this paradigm, nodes will automatically run the code contained in the contract when all participants meet certain conditions.
Despite their name, there is little about smart contracts which would make a valid agreement under existing UK contract law (Rühl, 2021). As has been recently demonstrated, contracts created by programmers may have significant logical flaws which may lead to devastating financial consequences. These bugs cannot necessarily be detected with analysis tools (Ghaleb and Pattabiraman, 2020).
One repeated concern expressed by stakeholders was the inability for Blockchains to redact or remove incorrect data. Colleagues in HM Land Registry published a "lessons learned" retrospective which investigated the inherent problems they found with immutable data structures (Tombs, 2019). GDPR requires our organisation to correct any mistakes about our data subjects. Because of the immutability of the blockchain structure, it is impossible to remove or alter data while preserving the chain's integrity. This represents a fundamental contradiction - and sets up a dilemma which may not be resolvable (Tatar, Gokce and Nussbaum, 2020).
The skills I learned on this CPD enabled me to understand what Blockchain technology purports to deliver and - more importantly - comprehend its limitations and defects. I was able to create a research plan to meet the user needs of our stakeholders.
On presentation of the proposals, there was considerable - and justified - scepticism from all parties involved in this exercise. Some had little interest in the technology, and several were already convinced that this was a "solution in search of a problem". Another had recently lost a considerable amount of money on cryptocurrencies and was convinced all Blockchain-based projects were a scam.
In conclusion, there was little interest in progressing the solution once we had reflected on the limitations of Blockchain technology. Despite the high interest by Governments in Blockchain technology (OECD, 2018) my research has concluded they are technologically deficient. A more practical solution may be a Merkle Tree variant as implemented in Google's Certificate Transparency Logs (Laurie, 2014).
3.4 Reflections and commentary on the next stages of my professional development
I will reflect on the application of the CPD using the DIEP model (Rogers, 2001) as discussed in §1.4.
Describe
I investigated whether Blockchain could be effectively integrated into a multi-party DNS agreement. I undertook a complex investigation consisting of analysis, literature review, stakeholder discussion, and understanding of key algorithms. This formed a testable hypothesis to see if it could meet business needs. It could not.
Interpret
I am grateful that my workplace embraces a culture of "Fail Fast" (Ehrenberg and King, 2020). Being able to experiment in an environment with high psychological safety and no fear of ridicule was an empowering experience. Even though the experiment failed, it taught me about the storage solutions and information governance issues present in Blockchain.
Evaluate effectiveness
Although Blockchain presents some potentially interesting data structures and solutions to esoteric cryptography problems, there is little practical application yet. Through this experience, I learned how to identify scams and become aware of how zealots attempt to convert the unwary into their "digital ponzi schemes" (Scharfman, 2022). I also gained an appreciation for the way novel technologies get assessed within my organisation.
Plan for the future
While it is important to explore the frontiers of innovation and explore idea space for emergent concepts, there is a risk that over-hyped technology will quickly fall out of fashion once its deficiencies are well understood. Therefore, to protect my own credibility, the next stage of my professional development will need to be in a more practical direction.
4. A discussion of a contemporary challenge
4.1 A Contemporary Challenge
Digital exclusion from government services is a pressing issue for society. Lack of reliable and digital identity often means vulnerable users in the UK are unable to access vital online services (Crosby, 2008). Internationally, the World Bank estimates 1.1 billion people have no proof of identity (Rajendran, 2017).
The UK's approach to verification of users has been costly, difficult for departments to implement, and hard for people to use (National Audit Office, 2017). Can the UK take advantage of Blockchain technology to create a more inclusive digital environment?
The author performed "competitive intelligence analysis" by investigating whether other states are modernising their identity infrastructure with Blockchain. They discovered how India has started to experiment with building new services on Blockchain (Chowdhury and Saha, 2021). They also found theoretical explorations of how a state could craft a biometric identity system utilising Blockchain (Páez et al., 2020) - but with little exploration of user-needs.
4.2 Potential Solutions
The World Wide Web Consortium's proposal for "Decentralised Identifiers" (W3C, 2021) defines several methods of Public Key Infrastructure (PKI).
This would allow a diverse set of participants to make identity claims about themselves and others - see Figure 02. By recording these claims on a Blockchain, data subjects can prove when a claim was issued and who issued it. The issuer would also be able to unilaterally revoke their claims - although they could not expunge the record of the original claim from the Blockchain.
The system also relies on all parties being able to keep their private keys safe - a well known failing of PKI systems (Ruoti et al., 2015).
Figure 02 - DID Diagram
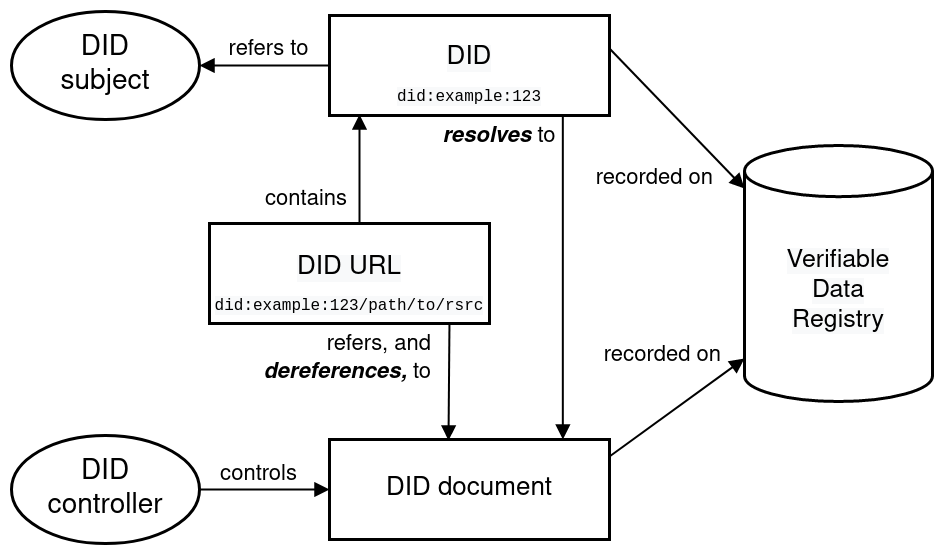 © 2021 W3C Decentralized Identifiers (DIDs) v1.0
© 2021 W3C Decentralized Identifiers (DIDs) v1.0
Could a state-backed blockchain be useful in providing a digital identifier to all of its citizens?
There are some superficial reasons to think so. Immutability of data may be attractive given how the hard drives of the UK's former National Identity Register were physically destroyed by a newly elected government (Boersma et al., 2014). An "always-on" connection to an online database is now possible given the surge in mobile internet access across all sectors of society (Ofcom, 2022).
But these need to be set against the complexity and uncertainties of the problem space. These sorts of intrinsic issues with multi-stakeholder systems are commonly referred to as "wicked problems" (Mertens, 2015).
4.3 The ethical role of the modern professional
Data Analytics professionals must identify the risks to both the user and the organisation from new technology. This can be via literature review or user research.
For the above example, a literature review reveals there are long-standing issues with the usability of PKI (Whitten and Tygar, 1999). Additionally, any system which relies on biometrics as a critical factor in authentication must contend with the fact that not all users will have those biometric markers. For example, some people have genetic mutations which prevent the development of fingerprints (Nousbeck et al., 2011).
The author believes the ultimate role of the Data Analytics professional is to stop the spread of unethical practices. As a member of the Chartered Institute for IT, it behoves the author to act under the auspices of their ethical framework.
This also means understanding the environmental impact of technology (Crooks et al., 2009). Given the continuing climate crisis (IPCC, 2022) and the exorbitant energy cost of Blockchain's "Proof of Work" algorithm (Schinckus, 2021), it is the author's professional opinion that all Blockchain technologies - whether in the identification space or otherwise - should be actively resisted.
References
Adenuga, Kayode & Ogunduyile, Gbenga Teaching Currency: Leveraging On Prospects And Challenges Of The 4th Industrial Revolution (Industry 4.0) In The Colleges Of Technology In United Kingdom
() IATED. doi:10.21125/edulearn.2020.0135
Andresen, L. and Emerson, S. (1991) ‘Educational Developers: What Do They Know?’, Higher Education Research and Development Society of Australasia, 13(1), p. 16.
Argyris, C. (1977) ‘Double Loop Learning in Organizations’, Harvard Business Review, 1 September. Available at: https://hbr.org/1977/09/double-loop-learning-in-organizations (Accessed: 27 April 2022).
Bavisi, J. (2021) ‘Plagiarism Investigation’, EC-Council. Available at: https://www.eccouncil.org/plagiarism-investigation/ (Accessed: 24 April 2022).
Boersma, K. et al. (2014) Histories of state surveillance in Europe and beyond. First edition. Oxon New York: Routledge, Taylor & Francis Group (Routledge studies in crime and society).
Cabinet Office (2021) National Cyber Strategy 2022, GOV.UK. Available at: https://www.gov.uk/government/publications/national-cyber-strategy-2022 (Accessed: 11 June 2022).
Chowdhury, Swarup Roy & Saha, Suman Building Better India
() IGI Global. doi:10.4018/978-1-7998-3444-1.ch007
Croman, Kyle & Decker, Christian & Eyal, Ittay & Gencer, Adem Efe & Juels, Ari & Kosba, Ahmed & Miller, Andrew & Saxena, Prateek & Shi, Elaine & Gün Sirer, Emin & Song, Dawn & Wattenhofer, Roger On Scaling Decentralized Blockchains
() Springer Berlin Heidelberg. doi:10.1007/978-3-662-53357-4_8
Crooks, B. et al. (2009) ‘Raising Awareness of Green IT - The BCS Way’, p. 15.
Crosby, J. (2008) Challenges and opportunities in identity assurance. London: HM Treasury.
Crossan, Mary Chris Argyris and Donald Schön's Organizational Learning: There is no silver bullet
() Academy of Management. doi:10.5465/ame.2003.10025187
Dallaway, E. (2021) The Story of the EC-Council Gender Survey Scandal: Survey Creator Says “It Was Written by Women so it Can’t be Sexist”, Infosecurity Magazine. Available at: https://www.infosecurity-magazine.com/blogs/the-story-of-the-eccouncil-gender/ (Accessed: 24 April 2022).
Denton, David Reflection and Learning: Characteristics, obstacles, and implications
() Informa UK Limited. doi:10.1111/j.1469-5812.2009.00600.x
Dors, Tania Mara & Van Amstel, Frederick M. C. & Binder, Fabio & Reinehr, Sheila & Malucelli, Andreia Reflective Practice in Software Development Studios: Findings from an Ethnographic Study
() IEEE. doi:10.1109/cseet49119.2020.9206217
Eaton, Colette “I don’t get it”, – the challenge of teaching reflective practice to health and care practitioners
() Informa UK Limited. doi:10.1080/14623943.2016.1145582
Ehrenberg, Andrew J. & King, John Leslie Blockchain in Context
() Springer Science and Business Media LLC. doi:10.1007/s10796-019-09946-6
Fernsten, Linda & Fernsten, Jeffrey Portfolio assessment and reflection: enhancing learning through effective practice
() Informa UK Limited. doi:10.1080/14623940500106542
GE, Chunmian & SHI, Haoyue & JIANG, Junhui & XU, Xiaoying Investigating the Demand for Blockchain Talents in the Recruitment Market: Evidence from Topic Modeling Analysis on Job Postings
() Elsevier BV. doi:10.1016/j.im.2021.103513
Gensler, G. (2018) Blockchain and Money | Sloan School of Management | MIT OpenCourseWare. (Course Number 15.S12). Available at: https://ocw.mit.edu/courses/15-s12-blockchain-and-money-fall-2018/ (Accessed: 4 May 2022).
Ghaleb, Asem & Pattabiraman, Karthik How effective are smart contract analysis tools? evaluating smart contract static analysis tools using bug injection
() ACM. doi:10.1145/3395363.3397385
Granan, Lars-Petter When researchers stumble, clinicians fall and patients suffer
() University of Buckingham Press. doi:10.5750/ejpch.v4i3.1192
Hargreaves, Janet So how do you feel about that? Assessing reflective practice
() Elsevier BV. doi:10.1016/j.nedt.2003.11.008
Helyer, Ruth Learning through reflection: the critical role of reflection in work-based learning (WBL)
() Emerald. doi:10.1108/jwam-10-2015-003
Hobbs, Valerie Faking it or hating it: can reflective practice be forced?
() Informa UK Limited. doi:10.1080/14623940701425063
Holmes, C. (2022) ‘How Blockchain Technology could support Democracy and E-Voting’, The Journal of The British Blockchain Association, p. 33960. Available at: https://jbba.scholasticahq.com/article/33960 (Accessed: 1 May 2022).
IPCC (2022) ‘Climate Change 2022: Impacts, Adaptation and Vulnerability’. Available at: https://www.ipcc.ch/report/ar6/wg2/.
Jasper, M. (2013) Beginning reflective practice. Nelson Thornes.
Jha, S. and Vazirani, N. (2021) ‘Determinants of Team Performance: Mediating Role of Team Reflective Learning & Team Trust’, Indian Journal of Industrial Relations, 56(3), pp. 521–536. Available at: https://search.ebscohost.com/login.aspx?direct=true&AuthType=cookie,ip,shib,uid&db=buh&AN=151343405&site=ehost-live&scope=site (Accessed: 12 June 2022).
Kompf, M. and Bond, W. R. (1995) Through the Looking Glass: Some Criticisms of Reflection. Available at: https://eric.ed.gov/?id=ED383661 (Accessed: 6 May 2022).
Laurie, Ben Certificate Transparency
() Association for Computing Machinery (ACM). doi:10.1145/2668152.2668154
Lilienfeld, Scott O. & Basterfield, Candice Reflective practice in clinical psychology: Reflections from basic psychological science.
() American Psychological Association (APA). doi:10.1111/cpsp.12352
Mann, Karen & Gordon, Jill & MacLeod, Anna Reflection and reflective practice in health professions education: a systematic review
() Springer Science and Business Media LLC. doi:10.1007/s10459-007-9090-2
Martins dos Santos, B. and Anastácio, K. (2022) ccTLDs: a recollection of the usage of country code domain names and their importance for identity and culture. SSRN Scholarly Paper 4023826. Rochester, NY: Social Science Research Network. Available at: https://papers.ssrn.com/abstract=4023826 (Accessed: 4 May 2022).
McGarr, Oliver & Ó Gallchóir, Ciarán The futile quest for honesty in reflective writing: recognising self-criticism as a form of self-enhancement
() Informa UK Limited. doi:10.1080/13562517.2020.1712354
Mertens, Donna M. Mixed Methods and Wicked Problems
() SAGE Publications. doi:10.1177/1558689814562944
National Audit Office (2017) Digital Transformation in Government. National Audit Office. Available at: https://www.nao.org.uk/report/digital-transformation-in-government/.
Norrie, Caroline & Hammond, John & D’Avray, Lynda & Collington, Valentina & Fook, Jan Doing it differently? A review of literature on teaching reflective practice across health and social care professions
() Informa UK Limited. doi:10.1080/14623943.2012.670628
Nousbeck, Janna & Burger, Bettina & Fuchs-Telem, Dana & Pavlovsky, Mor & Fenig, Shlomit & Sarig, Ofer & Itin, Peter & Sprecher, Eli A Mutation in a Skin-Specific Isoform of SMARCAD1 Causes Autosomal-Dominant Adermatoglyphia
() Elsevier BV. doi:10.1016/j.ajhg.2011.07.004
Blockchains Unchained
() Organisation for Economic Co-Operation and Development (OECD). doi:10.1787/3c32c429-en
Ofcom (2022) ‘Adults’ Media Use and Attitudes report 2022’, p. 30. Available at: https://www.ofcom.org.uk/research-and-data/media-literacy-research/adults/adults-media-use-and-attitudes.
Oluwatoyin, F. E. (2015) ‘Reflective Practice: Implication for Nurses’, Journal of nursing and health science, p. 7.
Onat, Nuri & Jabbar, Rateb & Kucukvar, Murat & Fetais, Noora Bitcoin and Global Climate Change: Emissions Beyond Borders
() Research Square Platform LLC. doi:10.21203/rs.3.rs-564281/v1
Ooi, Su Min & Fisher, Paul & Coker, Siân A systematic review of reflective practice questionnaires and scales for healthcare professionals: a narrative synthesis
() Informa UK Limited. doi:10.1080/14623943.2020.1801406
Páez, Rafael & Pérez, Manuel & Ramírez, Gustavo & Montes, Juan & Bouvarel, Lucas An Architecture for Biometric Electronic Identification Document System Based on Blockchain †
() MDPI AG. doi:10.3390/fi12010010
Pahlajani, Sunny & Kshirsagar, Avinash & Pachghare, Vinod Survey on Private Blockchain Consensus Algorithms
() IEEE. doi:10.1109/iciict1.2019.8741353
Phan, L., Li, S. and Mentzer, K. (2019) ‘Blockchain Technology and The Current Discussion on Fraud’, Computer Information Systems Journal Articles. Available at: https://digitalcommons.bryant.edu/cisjou/28.
qa.com | EC Council Certified Blockchain Professional (CBP) e-Learning (ECCCBP) (2022). Available at: https://www.qa.com/course-catalogue/products/ec-council-certified-blockchain-professional-cbp-e-learning-ecccbp/ (Accessed: 24 April 2022).
Rajendran, S. (2017) ‘Identification for Development 2017 Annual Report’. World Bank. Available at: https://thedocs.worldbank.org/en/doc/561391513609113984-0190022017/2017-ID4D-Annual-Report (Accessed: 1 May 2022).
Richardson, J. (2014) ‘Double Loop Learning: A Powerful Force for Organizational Excellence’, p. 10.
Rogers, Russell R.() Springer Science and Business Media LLC. doi:10.1023/a:1010986404527
Ross, Dian & Cretu, Edmond & Lemieux, Victoria NFTs: Tulip Mania or Digital Renaissance?
() IEEE. doi:10.1109/bigdata52589.2021.9671707
Rühl, Giesela Smart (Legal) Contracts, or: Which (Contract) Law for Smart Contracts?
() Springer International Publishing. doi:10.1007/978-3-030-52722-8_11
Ruoti, Scott & Andersen, Jeff & Zappala, Daniel & Seamons, Kent Why Johnny Still, Still Can't Encrypt: Evaluating the Usability of a Modern PGP Client
() arXiv. DOI: https://doi.org/10.48550/arxiv.1510.08555
Scharfman, Jason Cryptocurrency Compliance and Operations Case Studies
() Springer International Publishing. doi:10.1007/978-3-030-88000-2_8
Schinckus, Christophe Proof-of-work based blockchain technology and Anthropocene: An undermined situation?
() Elsevier BV. doi:10.1016/j.rser.2021.111682
Schön, D. A. (1987) ‘Educating the Reflective Practitioner: Toward a New Design for Teaching and Learning in the Professions’, undefined. Available at: https://www.semanticscholar.org/paper/Educating-the-Reflective-Practitioner%3A-Toward-a-New-Sch%C3%B6n/82276ad8751828a699e739f22b7a614a6863e776 (Accessed: 24 April 2022).
Schuster, Edmund Cloud Crypto Land
() Wiley. doi:10.1111/1468-2230.12603
Smith, Sara & Martin, Jan Practitioner capability
() Emerald. doi:10.1108/heswbl-04-2014-0009
Soeters, Joseph Why It Is Important to Be Cautious in the Analysis of Military Organizations: A Reply to Hasselbladh and Ydén
() SAGE Publications. doi:10.1177/0095327x20970248
Sparkes, Matthew UK jumps on crypto bandwagon
() Elsevier BV. doi:10.1016/s0262-4079(22)00649-2
Spruce, H. (2020) ‘Free Personal Development Plan (PDP) Example Template PDF’, The Hub | High Speed Training, 6 January. Available at: https://www.highspeedtraining.co.uk/hub/personal-development-plan-template/ (Accessed: 9 February 2022).
Szabo, Nick Formalizing and Securing Relationships on Public Networks
() University of Illinois Libraries. doi:10.5210/fm.v2i9.548
Tatar, Unal & Gokce, Yasir & Nussbaum, Brian Law versus technology: Blockchain, GDPR, and tough tradeoffs
() Elsevier BV. doi:10.1016/j.clsr.2020.105454
Tombs, L. (2019) Could blockchain be the future of the property market? - HM Land Registry, HM Land Registry. Available at: https://hmlandregistry.blog.gov.uk/2019/05/24/could-blockchain-be-the-future-of-the-property-market/ (Accessed: 2 May 2022).
Trozze, Arianna & Kamps, Josh & Akartuna, Eray Arda & Hetzel, Florian J. & Kleinberg, Bennett & Davies, Toby & Johnson, Shane D. Cryptocurrencies and future financial crime
() Springer Science and Business Media LLC. doi:10.1186/s40163-021-00163-8
W3C (2021) Decentralized Identifiers (DIDs) v1.0. Available at: https://www.w3.org/TR/did-core/ (Accessed: 2 May 2022).
Walker, Rachel & Cooke, Marie & Henderson, Amanda & Creedy, Debra K. Using a critical reflection process to create an effective learning community in the workplace
() Elsevier BV. doi:10.1016/j.nedt.2012.03.001
Webster, P Understanding the limitations of the ccTLD as a proxy for the national web: lessons from cross-border religion in the northern Irish web sphere
() Humanities Commons. DOI: https://doi.org/10.17613/yms5-9v95
Wheeler, H. (2022) Transforming for a digital future: 2022 to 2025 roadmap for digital and data, GOV.UK. Available at: https://www.gov.uk/government/publications/roadmap-for-digital-and-data-2022-to-2025/transforming-for-a-digital-future-2022-to-2025-roadmap-for-digital-and-data (Accessed: 11 June 2022).
Whitten, A. and Tygar, J. D. (1999) ‘Why Johnny Can’t Encrypt: A Usability Evaluation of {PGP} 5.0’, in. 8th USENIX Security Symposium (USENIX Security 99). Available at: https://www.usenix.org/conference/8th-usenix-security-symposium/why-johnny-cant-encrypt-usability-evaluation-pgp-50 (Accessed: 2 May 2022).
Wong, Ken Yan & Whitcombe, Steven W & Boniface, Gail Teaching and learning the esoteric: an insight into how reflection may be internalised with reference to the occupational therapy profession
() Informa UK Limited. doi:10.1080/14623943.2016.1175341
Yaga, Dylan & Mell, Peter & Roby, Nik & Scarfone, Karen Blockchain technology overview
() National Institute of Standards and Technology. doi:10.6028/nist.ir.8202
Copyright and Copyleft
This document is 🄯 Terence Eden CC-BY-NC https://creativecommons.org/licenses/by-nc/4.0/
It may not be used or retained in electronic systems for the detection of plagiarism. No part of it may be used for commercial purposes without prior permission.
Any source code is under the MIT Licence
This document contains public sector information licensed under the Open Government Licence v3.0. https://www.nationalarchives.gov.uk/doc/open-government-licence/version/3/
| Reply to original comment on twitter.com
More comments on Mastodon.