Some ideas are timeless. Back in 2004, an anonymous genius set up "FobCam". Tired of having to carry around an RSA SecurID token everywhere, our hero simply left the fob at home with an early webcam pointing at it. And then left the page open for all to see.
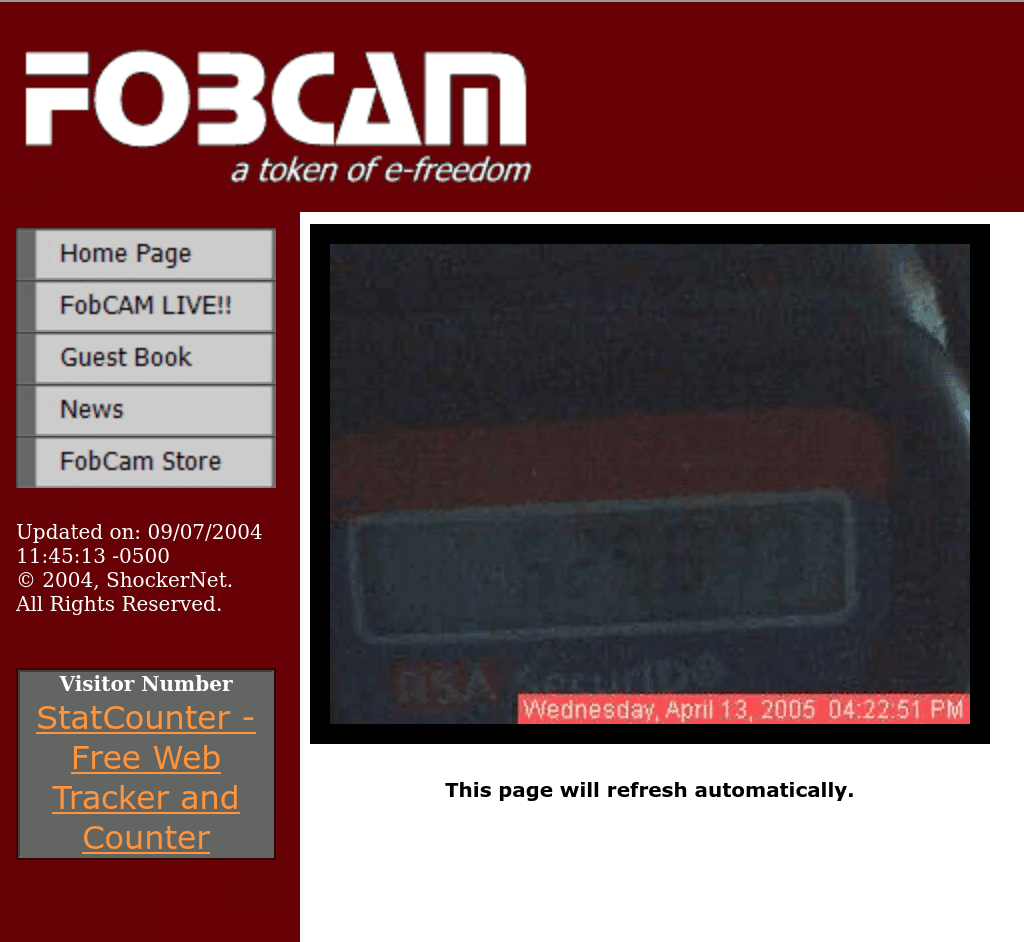
Security expert Bruce Schneier approved0 of this trade-off between security and usability - saying what we're all thinking:
Here’s a guy who has a webcam pointing at his SecurID token, so he doesn’t have to remember to carry it around. Here’s the strange thing: unless you know who the webpage belongs to, it’s still good security. Crypto-Gram - August 15, 2004
Nowadays, we have to carry dozens of these tokens with us. Although, unlike the poor schmucks of 2004, we have an app for that. But I don't always have access to my phone. Sometimes I'm in a secure location where I can't access my electronics. Sometimes my phone gets stolen, and I need to log into Facebook to whinge about it. Sometimes I just can't be bothered to remember which fingerprint unlocks my phone1.
Using the Web Crypto API, it is easy to Generate TOTP Codes in JavaScript directly in the browser. So here are all my important MFA tokens. If I ever need to log in somewhere, I can just visit this page and grab the code I need2.
All My Important Codes
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
What The Actual Fuck?
A 2007 paper called Lessons learned from the deployment of a smartphone-based access-control system looked at whether fobs met the needs of their users:
However, we observed that end users tend to be most concerned about how convenient [fobs] are to use. There are many examples of end users of widely used access-control technologies readily sacrificing security for convenience. For example, it is well known that users often write their passwords on post-it notes and stick them to their computer monitors. Other users are more inventive: a good example is the user who pointed a webcam at his fob and published the image online so he would not have to carry the fob around.
As for Schneier's suggestion that anonymity added protection, a contemporary report noted that the owner of the FobCam site was trivial to identify3.
Every security system involves trade-offs. I have a password manager, but with over a thousand passwords in it, the process of navigating and maintaining becomes a burden. The number of 2FA tokens I have is also rising. All of these security factors need backing up. Those back-ups need testing4. It is an endless cycle of drudgery.
What's a rational user supposed to do5? I suppose I could buy a couple of hardware keys, keep one in an off-site location, but somehow keep both in sync, and hope that a firmware-update doesn't brick them.
Should I just upload all of my passwords, tokens, secrets, recovery codes, passkeys, and biometrics6 into the cloud?
The cloud is just someone else's computer. This website is my computer. So I'm going to upload all my factors here. What's the worst that could happen7.
-
🫠 ↩︎
-
🖕 ↩︎
-
🙃 ↩︎
-
The neologism "doxing" hadn't yet been invented. ↩︎
-
As was written by the prophets: "Only wimps use tape backup: real men just upload their important stuff on ftp, and let the rest of the world mirror it" ↩︎
-
I in no way imply that I am rational. ↩︎
-
Just one more factor, that'll fix security, just gotta add one more factor bro. ↩︎
-
This is left as an exercise for the reader. ↩︎
3 thoughts on “FobCam '25 - All my MFA tokens on one page”
@Edent Fascinating experiment!
One random thought in response: Yubico took a lot of heat for making their key firmware read-only, but "nothing can modify the firmware" has its own security properties for some threat models.
| Reply to original comment on infosec.exchange
Dr. Winston O'Boogie
I don't get this. Does this mean that if I can get your email and password I can use this page to steal your accounts?
@edent
Well that wouldn't be very polite of you, would it?
More comments on Mastodon.