
A few weeks ago, someone wanted to send me some crypto. After spending months studying for a Blockchain exam, I usually avoid such things. But, hey, $20 is $20. So I signed up for a wallet, installed an extension, verified my credentials, saved a seed phrase, and - without too much technical fuss - had some crypto transferred to my account. So far, so good. Compared to a traditional financial…
Continue reading →
A glistening pool of blood gently wept from the body. Crimson gore sparkled under rapid flash photography as it loosely clung to the wounds. So many wounds. Too many for this to have been an accident. "Bite marks," said the forensics officer. "A lot of bite marks." The detective peered at the ragged corpse. It was barely recognisable as human; just a series of holes where flesh ought to be. …
Continue reading →

I love putting stickers on my laptops. But when it's time to move to a different laptop, what happens to all those cool stickers? After spending too many nights with a scraper and isopropanol, I decided to get a pre-cut dbrand skin. It'll protect the laptop and it will peel off in one piece, allowing me to preserve all my old stickers. I got the cheapest possible one - it's going to be covered…
Continue reading →
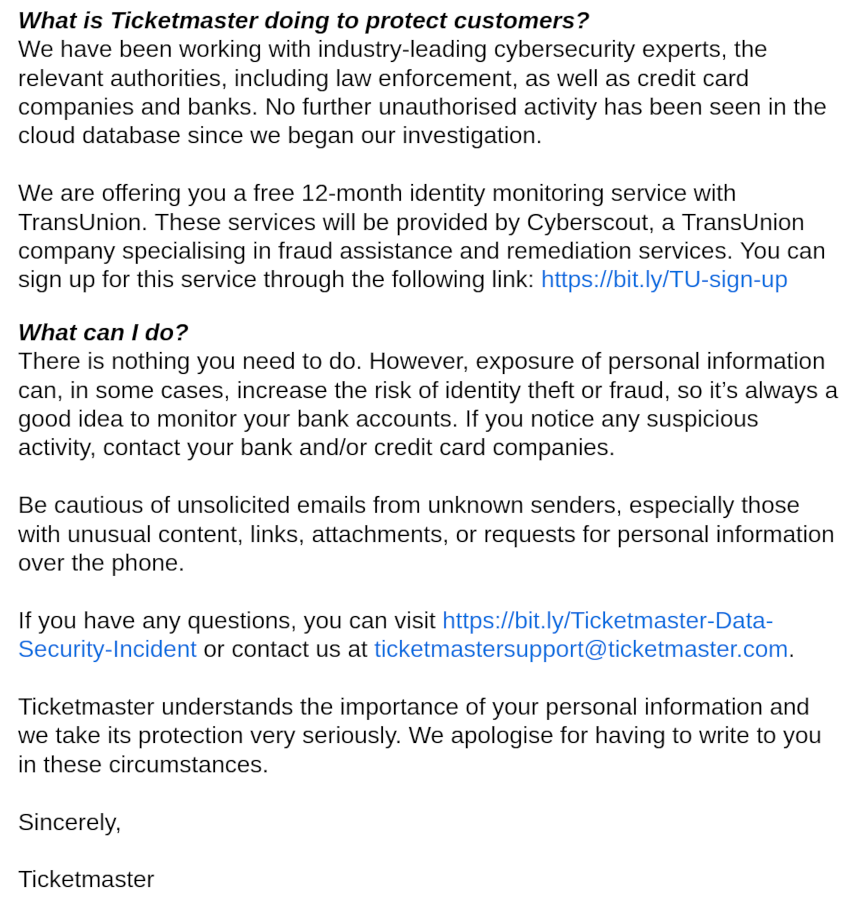
TicketMaster has joined the long list of companies to lose their customers' information. As is common, they sent out an email to warn poor sods like me who might have had our details snaffled. Their email is particularly poor and contains a delightful example of how not to communicate issues like this. See if you can spot it: In the same breath as warning their customers to look out for…
Continue reading →

Another one in the Panopticon series. Bouncy sci-fi which scattershoots its plots all over the place. VR, Mission to Mars, evil AI, underwater cities, eyeless technomages - this has it all. It probably has a little too much crammed in. But, hey, it's a great ride. A cliffhanger every other chapter, vaguely plausible science, and mortal danger at every turn. It looked like I was about to be part …
Continue reading →
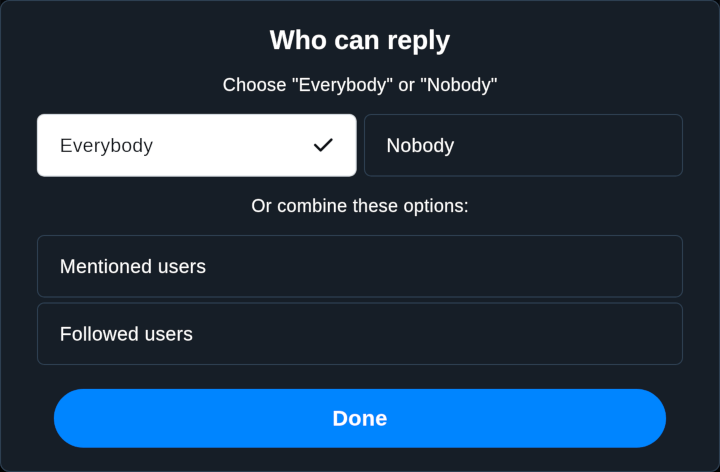
Vague thoughts as they enter my brainbox. The BlueSky social network has introduced "Reply Gating" - it looks like this: You can write your hot take on Taylor Swift and not be inundated by weirdos replying to you. Nifty! This is nothing new. Twitter has it. Facebook has the concept of "audiences" to restrict who your post is visible to. And, of course, blogging has this! There is a comment …
Continue reading →

I thought I didn't know Tchaikovsky's Swan Lake. But, like all truly great cultural phenomena, it had disseminated itself through the cultureweb so thoroughly that I felt completely familiar with it. Performed in the round, from our nosebleed seats we had a stunning view of the action. The full floor of the Royal Albert Hall is used - there's so much going on that it become hard to take it all…
Continue reading →

Guess who's back, back again! If you're new to the blog series, this is where I attempt to identify all the mobile phones used by The Doctor and their companions. The 2024 series is incredible. Lots of plot, not too much exposition, and a whole bunch of mystery. I love it when Doctor Who goes off in a new direction. Let's take a look at the handsets used in these stories. The Church on Ruby…
Continue reading →

Last week, I was part of the BarCamp London Hackathon. It had all the usual ups and downs of a Hackathon - laptops crashing, APIs failing, and HDMI ports breaking. We had a massive projector for participants to show off their work. The HDMI connection was… shit. Sorry, there's no better way to put it. It worked for about 30 seconds and then displayed a green screen. We replaced the HDMI cable. W…
Continue reading →

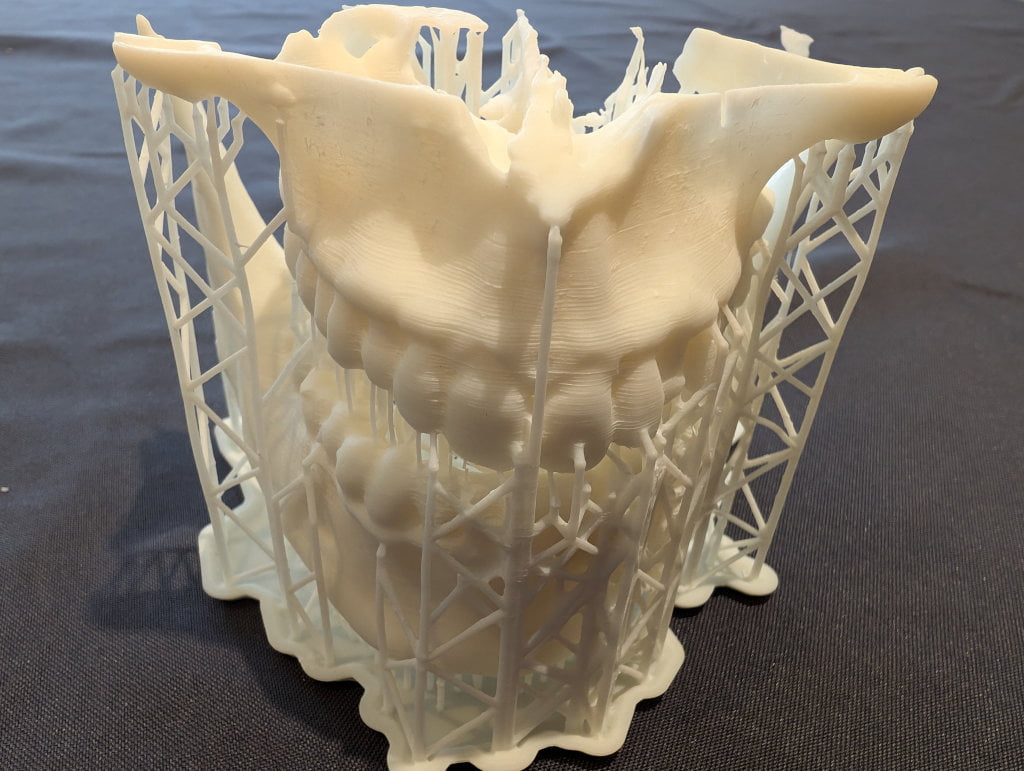
As previously mentioned, I recently had a some dental issues and learned how to view a CT Scan in 3D using Linux. At a hackathon last week, my friend Sidd brought along a 3D printer. How hard is it to convert a CT scan to a file suitable for printing? Slightly trickier than I expected! Most of the guides I found were outdated, or the software didn't work on Linux, or the instructions assumed a…
Continue reading →

Over the last few weeks, I've had several people ask me about the recent hack on the NHS. A ransomware attack has meant that several hospitals have cancelled operations and there is now an urgent demand for blood donors. What does it say about the state of NHS IT that this attack has happened? Nothing. Because the NHS was not hacked. Instead, a company they use to perform blood tests was…
Continue reading →

The Tildagon has 2MB of RAM. That's not enough to do... well, most things you'd want to do with a computer! There's not much processing power, so running complex image decoding algorithms might be a bit beyond it. Is there a simple image format which can be parsed and displayed? Yes! The ancient Portable PixMap (PPM) format. The standard is beautiful in its simplicity. Here's the header: …
Continue reading →











