
Suppose you are sent a link to a website - e.g. https://example.com/page/1234 But, before you can access it, you need to log in. So the website redirects you to: https://example.com/login?on_success=/page/1234 If you get the password right, you go to the original page you requested. Nice! But what happens if someone manipulates that query string? Suppose an adversary sends you a link like…
Continue reading →
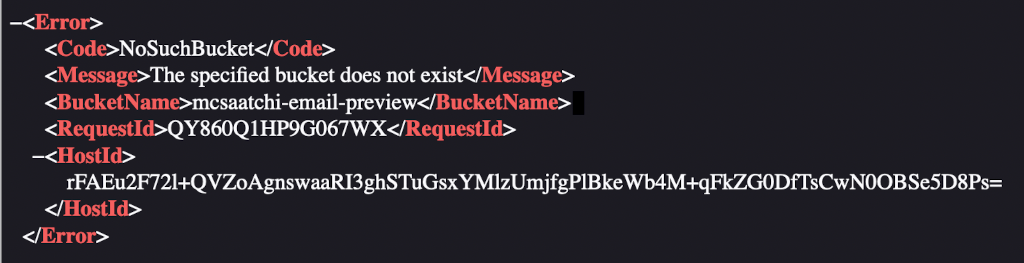
A few weeks ago, I received a billing email from my phone provider O2. While glancing at it, I noticed all the images were broken. Viewing the source of the email showed that they were all coming from http:// mcsaatchi-email-preview.s3.amazonaws.com/o2/... What happens if we visit that domain? Ah, the dreaded "The specified bucket does not exist" error. At some point the images were…
Continue reading →

Codeberg is a hip new code hosting site - similar to GitHub and GitLab. And, much like Gits Hub & Lab, users can serve static content through Codeberg pages. Somehow I screwed up my configuration, and when I visited edent.codeberg.page/abc123 I got this error: Now, whenever I see something from the request echoed into the page's source, my hacker-sense starts tingling. What happens if I…
Continue reading →



