A few weeks ago, I received a billing email from my phone provider O20. While glancing at it, I noticed all the images were broken.
Viewing the source of the email showed that they were all coming from http:// mcsaatchi-email-preview.s3.amazonaws.com/o2/...
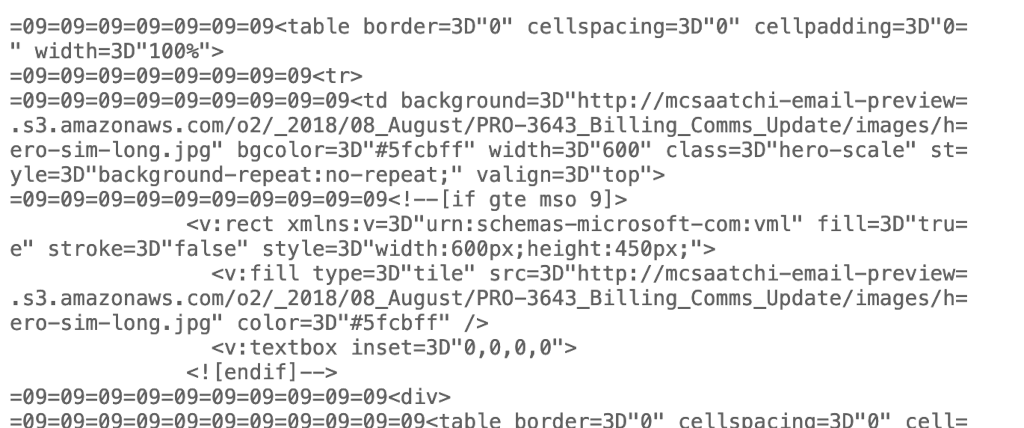
What happens if we visit that domain?
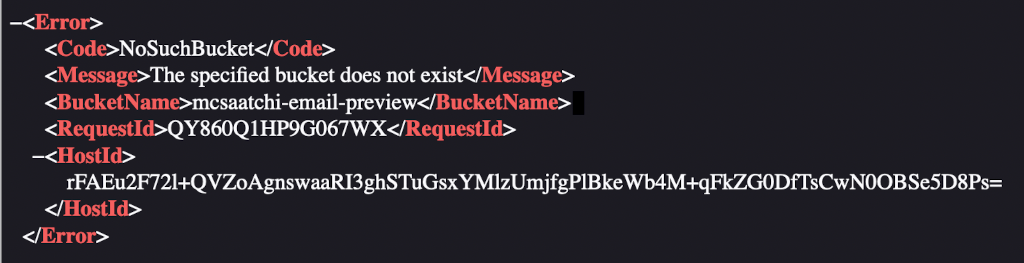
Ah, the dreaded "The specified bucket does not exist" error. At some point the images were served from that domain but someone deleted the bucket.
This is a problem. Amazon doesn't reserve bucket names after they're abandoned. Which means digital miscreants can claim them.
Imagine if, say, Vodafone1 registered that bucket name. All of a sudden they could inject their logos or adverts into their rival's billing emails.
An attacker could go further. They could replace the images with ones saying "Please note our bank details have changed, send BitCoin to...."
It gets worse. The emails contain a link to an external font.

An attacker could craft a font with specific ligatures which would replace the text of the email!
I quickly defensively registered the bucket on AWS and sent an email telling O2's security team about the problem. I suggested they update their future emails. Of course, that doesn't help all the emails which have been already been sent and are lingering in their customers' inboxes. So I offered to transfer the bucket name back.
I received an automated response saying they'd look in to it.
Lessons you should learn
You should be very wary about hosting your critical infrastructure on a sub-domain outside of your control. And you should never point directly to an S3 bucket if you can help it.
Ideally, O2 would have spun up a domain like images.billing-emails.o2.com, pointed it to S3, and used that in their emails. That way, if they decided not to continue using Amazon's services, all their existing billing emails would be unaffected.
If an attacker gets control of a domain used to show images in emails, the can directly target your customers.
Timeline
- 2023-01-26 Issue detected. Defensively registered. Email sent.
- 2023-02-21 Reminder email sent informing them that I'd be publishing this post.
- 2023-02-22 O2 said they were investigating and asked me to delete the bucket, which I did. They swiftly reclaimed the bucket and repopulated its content.
- 2023-02-27 Blog post automatically published.
No bug bounty, but O2 did raise my bill by 17.3%…
One thought on “Responsible Disclosure: Abandoned Buckets and Billing Emails”
@Edent dang, not even a bug report helped escape the dreaded RPI increase :p
would be interesting if Amazon “soft-deleted” buckets for ~a month, maybe strongly suggesting you recreate the bucket if it still sees requests?
admittedly, (as you mention) this sort of thing catches out domains as well- I remember Microsoft forgetting to renew passport.net and hotmail.co.uk a few decades ago https://web.archive.org/web/20000303032920/http://www.doublewide.net/ https://www.theregister.com/2003/11/06/microsoft_forgets_to_renew_hotmail/Michael Chaney's Personal Web Page at Doublewide
| Reply to original comment on woof.tech
More comments on Mastodon.