Codeberg is a hip new code hosting site - similar to GitHub and GitLab. And, much like Gits Hub & Lab, users can serve static content through Codeberg pages.
Somehow I screwed up my configuration, and when I visited edent.codeberg.page/abc123 I got this error:

Now, whenever I see something from the request echoed into the page's source, my hacker-sense starts tingling. What happens if I shove an innocent HTML element into the URl?
edent.codeberg.page/abc<em>123
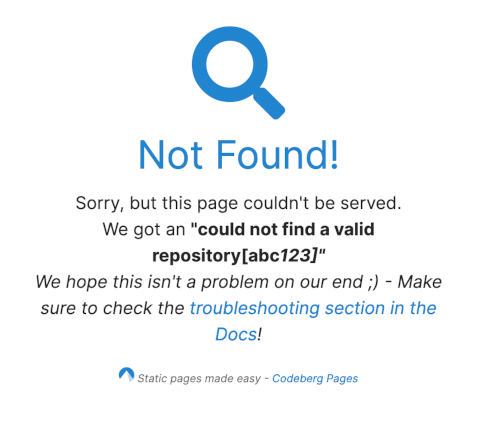
Aha! It lets through some HTML. I wonder which other elements it lets through? Let's try...
edent.codeberg.page/abc<img src="https://placecats.com/640/640">123

Ah nuts! Let's look in to the source code to see what went wrong:
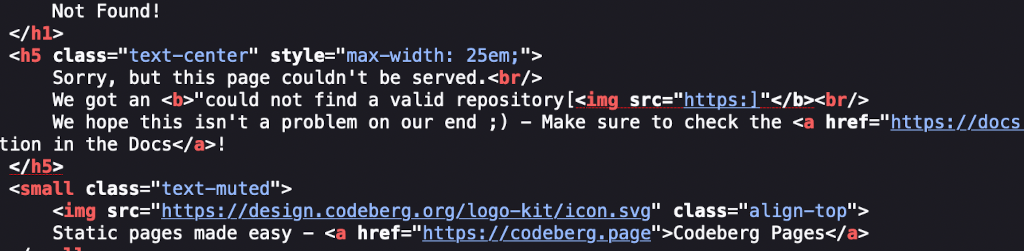
It seems that the back end code has some protection. It strips all / characters. That makes it impossible to inject a working <script> element because there will never be a </script> to close it.
We can't even use my favourite little trick of Base64 encoding the contents of an <iframe>:
HTML
<iframe src="data:text/html;base64,PHNjcmlwdD5hbGVydCgiWFNTISIpOzwvc2NyaXB0Pg==">
Manually removing the / led to this:

No forward slashes makes things like <svg> injection difficult - if not impossible. Hmmm... what can we do...? I know!
test.codeberg.page/abc<img src=1 onerror=alert("xss") ;

Boom!
Let this be a lesson to you - always sanitised user-supplied content, no matter how innocuous it seems.
Timeline
- 2022-12-02 Discovered. Emailed support, got a secure address to email, sent disclosure.
- 2022-12-05 Tested and discovered that it had been fixed.
- 2023-01-02 Blog post automatically published.