If you have a TingTag, your location is being broadcast without encryption!
Earlier this year I purchased and reviewed the TinTag. I've spent the last month trying to get hold of the company to report a serious privacy problem with their Android app. I've not received an adequate response, so I'm publishing this post to let affected users know about the issue.
The TinTag is a BLE tracker. It's designed to attach to your keys or bag. An app on your phone can send a message to the tag, which causes it to light up and make a noise. Handy if you've lost your keys and you're within Bluetooth range.
But what if you drop your keys while out jogging - how will you find them again? These tags are too small and under-powered to run a GPS chip. Instead, the app does the heavy lifting. Every time the app detects the beacon, it records the phone's location and uses that as the "last known location".
And if you've lost your phone as well? No worries! The TinTag app uploads your precise location to its web server.
Completely unencrypted!
*sigh*
Let's fire up our trusty MITM app and see what the Android TinTag app is broadcasting to the world.
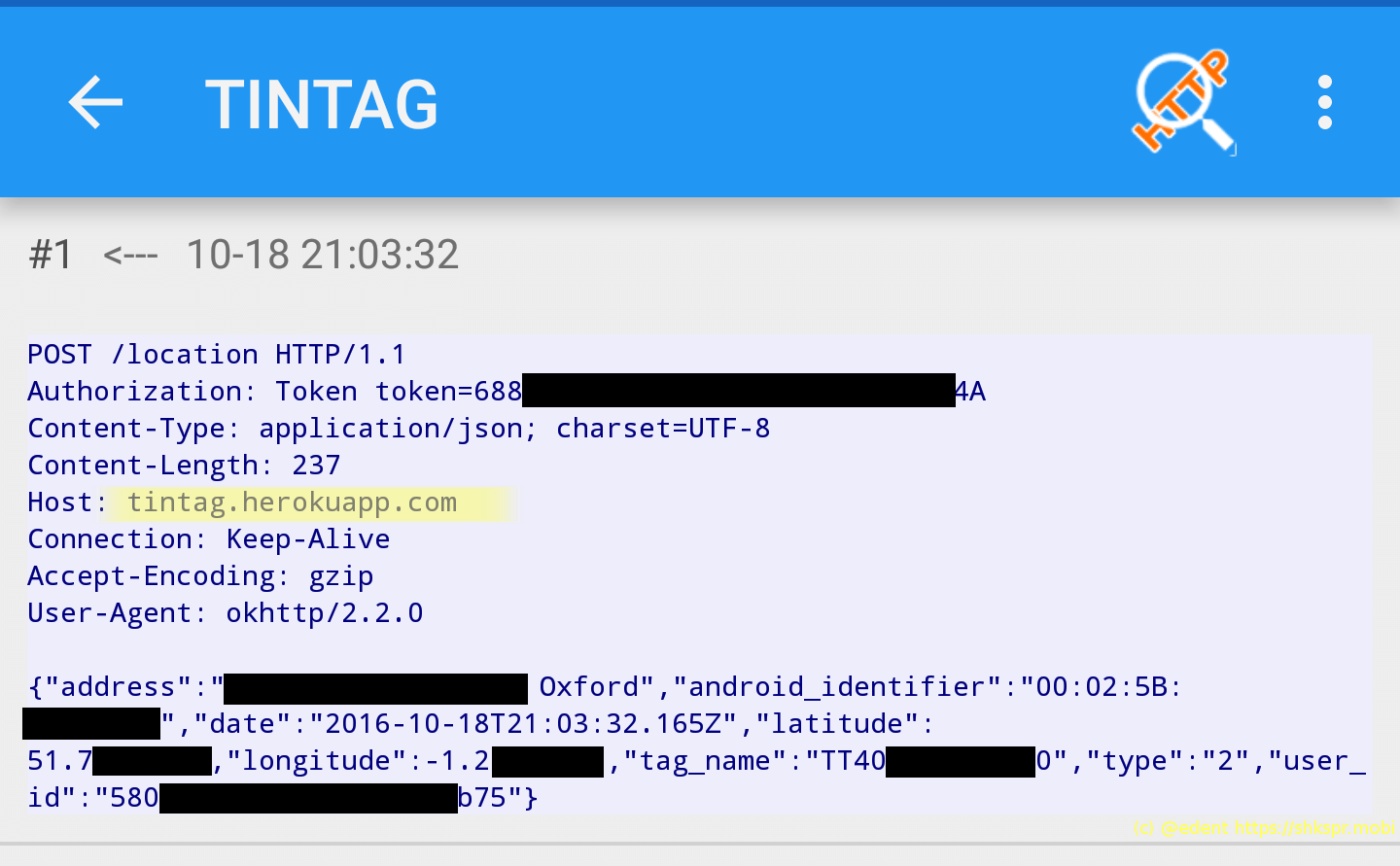
First off, all data is sent in the clear to Heroku.
TinTag are sending...
- The street address of the user.
- The MAC address of the TinTag.
- The precise latitude and longitude of the user.
- The tag's ID.
- A unique user ID.
Of these, the most obvious concern is the exact location of the user. They aren't encrypted in transit - what's the betting that they're encrypted on the server?
Given that TinTag haven't updated their Android app since the beginning of the year, do you think they've updated their server's software recently?
If TinTag's servers are attacked - someone could get your entire location history.
In part, I must say that I blame Heroku for some of these problems. They could make their domains SSL enabled by default - but they don't. Unfortunately, even if Heroku switched on SSL for all their users - that wouldn't help TinTag. Digging into the app's code, this is what we find...

My Java is a little rusty - but I'm reasonably sure that code is a "radically insecure" way to accept all HTTPS connections even if they are not valid!
The sad thing is, the TinTag is a great piece of hardware. It has a nifty wireless recharger, has brigher lights and a louder speaker than any other BLE token I've found. The software is so desperately insecure with your privacy that owners should stop using it immediately.
Timeline
- 17 October - repeated attempts to contact the company via their website.
- 26 October - contacted the CEO via LinkedIn.
- 01 November - response from CEO promising to look in to it.
- No further contact from TingTag despite trying to contact them.
- 17 November - publication.
3 thoughts on “Full Disclosure - This Bluetooth tag is leaking your personal data”
Well, they can't update the application on the Play Store Not with this code. Since May, any broad TrustManager implementation like this one is forbidden: https://support.google.com/faqs/answer/6346016
So, they may have updated their server!
I recognise the pain that is SSL in Android (Java) environments. I've just recently had to go through the excruciating experience that is dealing with certificates, incomplete chains, closed peer connections, disabled TLS and then some, to get this to work properly on Androids dating back to 3.0. And I have to admit, I'd rather not have to deal with it again if I absolutely don't have to.
That said, I too accepted all certificates similar to the way shown in the code in this post because of simpler debugging and testing, so I recognise what they've done. But pushing that to production/live.... Nope. Nope, nope, nope.
Trackbacks and Pingbacks
[…] Full disclosure – this Bluetooth tag is leaking your personal data • Terence Eden […]