Designing a Home Network for Hostile Devices
I've written before about just how many Internet connected gadgets I have.
I've also blogged about my dodgy WiFi lightswitches which send data back to China.
Every IoT device you put in your home brings a certain level of risk to the other devices in your network.
For example, my Smart TV and my Lifx don't require a password to access. Any device on my network can control them. That's extremely convenient - but it's a security nightmare.
Consider, for a moment, my WiFi Smoke Alarm. It periodically connects to the Internet to check for software updates. What if a hacker uploads fake firmware which scans for local devices and abuses them? Or opens up a tunnel into my network for criminals to access?
We're all one software update away from being infiltrated.

How should a suitably paranoid person design their home network?
All Together Now!
The naïve design is just to shove everything on one network.
Without a doubt this is the easiest to configure - just tell each device the WiFi password - but it's the most dangerous. Any device can talk to any other device. If your SmartTV receives a commercial for a DELICIOUS MILLER LITE™ BEER OF CHAMPIONS® it might connect to your smart fridge (no password - because who needs security on a domestic appliance) and order you an unwanted beer.
Or the Taiwanese company which made your lightbulb might get sold to a company who have no ethical qualms about exploring your NAS to see what sort of "exotic" material you have on there. Then encrypting and ransoming it back to you.
Blind Segregation
The router supplied by my ISP allows me to set up two isolated networks. I currently have a guest network which is open to anyone who visits (although that, in itself, may not be a wise idea).
So I could put my untrusted devices on a separate network to the devices I have a reasonably high degree of trust.
This makes accessing those devices less convenient - and it still means my Smart Toaster can turn off my Security Cameras.
Complete Separation
Suppose I set up a separate subnet for each device? 192.168.0.* for trusted devices, 192.168.1.* for all the security cameras. 192.168.2.* for all the Samsung kitchen appliances. And so on and so forth.
A chore to set up, but this has a superficial charm. Until I come to do anything. I want my phone's app to be able to control my games console. I want my TV to be able to read media off my local server.
Of course, that assumes that a regular ISP supplied router can do that. Hint - it probably can't.
Complex Firewalls
Ok, so now we move way beyond what a domestic router can normally do and into professional grade stuff. Forgive me if my use of terminology isn't 100%.
Each device added to the network needs to be part of an access control list. The firewall determines if any two devices are allowed to communicate with each other. For example:
- My tablet and laptop should be able to connect to everything.
- My Kindle should only have access to the Internet.
- My fridge and freezer can talk to each other - but nothing else.
- My solar panels can talk to my solar battery - but only on port 80.
What an absolute nightmare to set up. I'm not even sure what sort of router I'd need to buy in order to make something like that possible. How easy would it be to misconfigure? One errant mouse click and my Sonos speaker can unlock my front door when it plays a specifically crafted MP3...
How to build this?
I pride myself on being relatively tech savy. I've got around 40 Internet connected devices around the house - only some of which are under my direct control.
I've asked this question on the Security StackExchange - but I'd be grateful for any wisdom from you, dear reader. Are there any products that you can suggest?
Or, do I just give in gracefully? Stick strong passwords on everything which can be protected, and hope that none of me devices become part of the Internet of Traitors?
 Internet Connected Lightswitches - Redux!
Internet Connected Lightswitches - Redux!
 Gadget Review: DophiGo DV-200 WiFi Doorbell
Gadget Review: DophiGo DV-200 WiFi Doorbell
 Adventures in home automation - Home Assistant on a Raspberry Pi 2
Adventures in home automation - Home Assistant on a Raspberry Pi 2
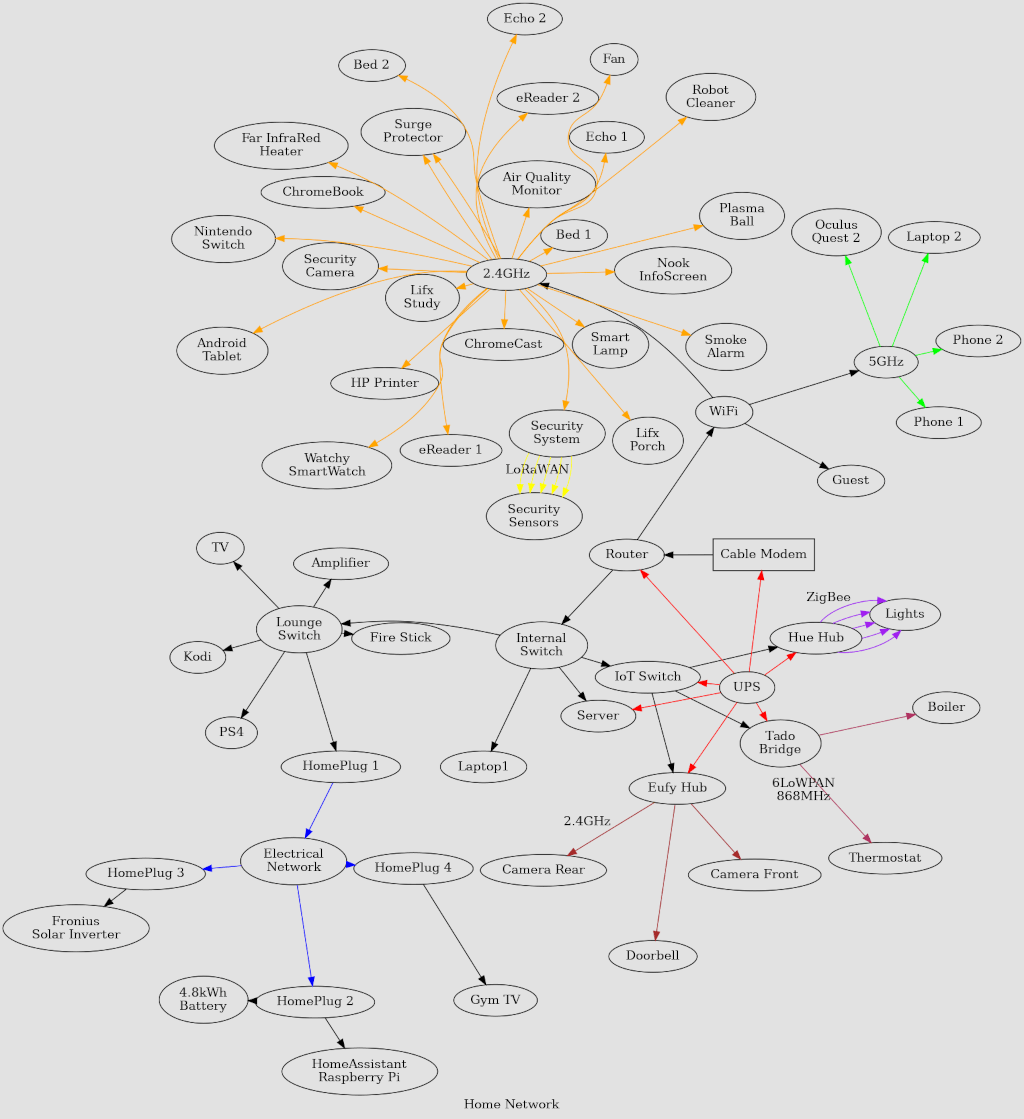 My Underkill Home Network
My Underkill Home Network
Matt says:
Or my preference, OpenBSD box with IP aliasing and pf
http://www.openbsd.org/faq/faq6.html#Setup.aliases
Jeremy Sullivan says:
Amily Carruth says:
Better throw out most of those devices :D. But in any event subnet them like you proposed with VLANs. For that, also get an Ubiquity UniFi AccessPoint. It allows you to assign different WLAN credentials to different VLANs and then the edge router can setup firewall rules about how those VLANS can interact. I have a trusted network of NAS + AppleTV + MacBook. Everything else goes into an untrusted LAN. But generally I don't have any IoT devices, and I doubt I ever will let them into my house.
https://www.ubnt.com/unifi/unifi-ap-ac-lite/
https://www.ubnt.com/edgemax/edgerouter-lite/
Terence Eden says:
lluad says:
Terence Eden says:
Tom says:
At the very low end, the venerable WR841N (2.4 GHz only 802.11n up to 300 Mbps) which can be had for under 20€.
Then the WDR3600 (or: 4300, 4900) (dual-band 802.11n up to 600 or 900 Mbps, much beefier CPUs) which are end-of-line but might be found used for about 40€.
And from their current line-up the Archer C5v1 / C7v2 (note the hardware revisions, which *must* match; note also that C5v1 and C7v2 are hardware-identical) (dual-band 802.11ac up to 1750 Mbps) which retail for 60€ to 100€.
There are others, but I can’t speak for them. The TP-Links are pretty well-known for their value for money, for example, the German community wifi "Freifunk" has several tens of thousands (!), primarily WR841Ns, all running OpenWrt.
John Tolly says:
pcunite says:
jstorm says:
First, establish security domains, which are essentially policy scopes with which the network should align. Doing this depends on what you value, and security domains for your environment might be Appliances (devices that cooperate and are centrally managed), Infrastructure (power, water, heat, and so on; again, things that can cooperate but take priority over other household devices), DMZ (isolated Internet access with device cooperation prohibited), Internal (a trusted domain containing your personal computers) and Internet. It may also be reasonable to have an isolated Vendor domain, for embedded devices that connect to the cloud (security cameras, smart TVs, etc.) but still need to cooperate locally.
Defining security domains in this way, the goal is not to eliminate attack vectors (magical thinking) but to constrain them so they can be well understood, preferably without introducing any more complexity than is necessary.
Second, establish a central point of control: a firewall. Every layer-3 interface of the firewall should reflect a security domain, which may consist of multiple subnets (VLANs) attached to a router. Doing this ensures you need only configure rules for interaction between security domains, letting switches (or additional routers) do the rest. That every firewall rule must be meticulously crafted is an ugly part of making this work, but if you want to know exactly what's allowed to get to where, there will be no mystery.
For a domain that doesn't need to interact with the others (a test network, say) it doesn't need to be represented on the firewall as it can remain isolated. This is likely a good idea for your Infrastructure devices, which can remain on a separate VLAN with static IPs, and can be managed by connecting your laptop to a port on that VLAN. For why this is a good idea, read up on some of the SCADA hacks that have been in the news. This level of isolation didn't stop Stuxnet, but that was another level of attack entirely.
Once you have security domains and a way to control them, the rest is endpoint management. Monitor your network traffic with an IDS, keep abreast of software updates in your computers and appliances, be weary of untrusted USB drives and e-mail attachments, etc. You can do these things today, without a complex network.
To the question of hardware, I would use a Cisco ASA 5506-X for the firewall. I'm biased because I work with ASAs often, but the 5506-X is (somewhat) affordable and has every feature you'll ever need (and then some). For home routers, anything that supports static routes (or a dynamic protocol if you really start to grow 🙂 ) and pushes the right bandwidth will do. For switches, anything that supports VLANs and the right bandwidth are fine.
I hope this helps. Regardless, good luck in finding a good arrangement for your extraordinarily large home network! 😀
Gary Gapinski says:
Network segmentation will require a decent (i.e., non-consumer) edge router and managed switches (with which to establish VLANs). The router can be accomplished using hardware or software running in a dedicated or virtual machine. Prices start at free, $100 (e.g. for Ubiquiti and Mikrotik gear), and go up from there. Managed switches start around $50. Building something yourself (e.g., pfSense in a VM) will save money at the cost of time (and adds the benefit of understanding how such things work).
You may want to take a look at Security Onion ( https://security-onion-solutions.github.io/security-onion/) to get a sense of the types of applications used for IDS, IPS, logging, analysis, alerting, and so forth. The apps in that bundle are good examples and save quite a bit of work of manual assembly. There are others, however, also freely available, and your cost is just the time spent acquiring competence with them.
You'll need a dedicated or virtual system with which to run the observation and analysis stuff. This will likely cost north of $600.
Expect to spend 200+ hours initially and at least several hours per week thereafter. Probably more. Some of that time should be spent learning to use Wireshark.
Not as flexible as a general set of multiple subnets, but easy to set up...?
http://events.linuxfoundation.org/sites/events/files/slides/Intelligent%20IoT%20Gateway%20on%20OpenWrt.pdf
Nnyan says:
So far that I at the core of the network is a Dell 6224 L3 switch as my core switch which handles VLAN routing. An HP 1810-48 port L2 switch for home runs back to the server closet. I found a number of devices don't work at all or very well if you have multiple hops. Also anything that handles large files/media I found I get better performance doing a direct run to the patch panel. Here are typically the steps I take on a new (non enterprise) network:
1. Identify and remediate what targets you have on your network. I am a big fan of nmap/zenmap, Nessus Home, NTOPNG and wireshark and yes there is a learning curve to some of these but well worth it I think. I also use NetCrunch Tools, Graphical Network Monitor, NetBeez.
2. Secure the endpoints. I typically have Bitdefender as the EP AV (although the Sophos Home suite is free and VERY nice) and Glasswire as a local firewall.
3. Secure. Deploy your firewall, IDS, IP blocker, Ad-blocker, etc... *
4. Setup reporting/alerts.
5. Test your setup.
I'm currently running pfSense with Suricata (IDS) and pfblockerng /with DNSBL as my firewall/router/gateway. This was pretty easy to setup even to a non linux wiz like myself. I am looking to move away from pfSense b/c it's reporting/alerts leave a great deal to be desired. For example I would never have known that one of my Synology NAS boxes had opened up port 5000 and I was getting dozens of remote connection attempts every day.
I currently have a Cujo security appliance. This was a bit more of a PITA to setup due to my network topology and I DO NOT recommend running it in DHCP mode (which hinders some features but can mess with a few things on your network). I'm currently using it as a last line of defense and reporting tool. It notifies me whenever it detects anything shady (which is how I got alerted to the port 5000 issue). BUT it is not feature complete yet and you get very little data/information currently so it's not a good primary solution.
Additionally my DNS is currently handled on a different VM that is just running Pi-Hole. It was a bit wonky until I restarted the VM but EVERYONE loves how it kills just about 100% (so far) of all craptastic ads on websites.
I really like the Sophos/Untangled UTMs for a number of reasons but I really want better AV at the core then available with pfSense. I also want to consolidate to one pane of glass and not have Bitdefender be the website net-nanny (one less place to manage from).
I'm also in the process of deploying/playing with a Mikrotik hEX to my parents house as they are retired and non-technical and just need a simple low powered solution (they have been hacked once already). I haven't played with these units yet but based on performance reports they spank the EdgeRouter Lite's that everyone seems to love (and has a nice gui) so I'm excited about that.
I also want to check out the netgate SG-1000 and maybe play around with a Beaglebone Black with simple iptables/nftables firewall.