
The good news follow-up rarely gets as much attention as the original bad-news story. Earlier this month I accidentally kicked off a minor kerfuffle over whether BMW was respecting the GPL. Their i3 car contains a huge amount of Open Source Software and there was some confusion as to BMW's compliance with the licence terms. I took a look through the car's user interface and, hidden away, was…
Continue reading →

I've written before about just how many Internet connected gadgets I have. I've also blogged about my dodgy WiFi lightswitches which send data back to China. Every IoT device you put in your home brings a certain level of risk to the other devices in your network. For example, my Smart TV and my Lifx don't require a password to access. Any device on my network can control them. That's…
Continue reading →

Imagine, just for a moment, you could tell someone's most intimate secrets just by looking at them. Many year ago, when I was very young and you were even younger, I saw an advert in the back pages of some cheap comic. The implication was clear - SEE GIRLS NAKED! The reality was somewhat more prosaic. But technology marches on. Today, you can buy a smartphone with a thermographic camera. …
Continue reading →

Even in the depths of British winter my solar panels'll still happily convert what little sunlight we get into delicious, free-range, organic electrons. Nice! Most of our domestic energy use is in the evening. So, when I'm out at work I can schedule the tumble dryer, robot vacuum cleaner, and WiFi rice-cooker to consume energy when the sun is shining. The rest is sold back into the grid for…
Continue reading →

I've got three Raspberry Pis around my house. Well... at least... I think I do. I can certainly ping three of them. I know the physical location of two of them... It's a testament to the success of the Raspberry Pi. Anyone with £30 to spare can pick one up and start hacking. Want to build an IoT fishtank? Start with a Pi. Need to monitor air pollution? Start with a Pi. Have a vague idea...? You …
Continue reading →

Just because I ask a question - doesn't mean I'm asking you a question! There's a certain class of Internet user who troubles me. He - and it is usually a he - will strive to answer any technical question he sees asked, no matter his lack of expertise. Here are the symptoms: Sometimes he responds with the first Google link for the question - as though I haven't thought of doing a basic…
Continue reading →

I accidentally caused a little brouhaha last week - for which I would like to apologise. In my blog post about BMW's unencrypted software updates, I said: Judging from the files, it would appear that the infotainment system is made by Magneti Marelli with components by Wind River, AutoSAR, and Nvidia Tegra. Looking at the copious mentions of systemd and freedesktop it's a Linux system! …
Continue reading →

Update! I now have an XSS which is only 18 characters! Here's a fun little game for all the family! What is the minimum number of characters required to perform a successful XSS attack? Let's take an entirely theoretical example - suppose we have a site which echos back user input without sanitising it. So a search for " <em>" turns the whole page italic. ahem A hacker might think, "Hurrah! …
Continue reading →

When is a string not a string? When it's a series of control characters! Not a particularly funny riddle, but one I've been wrestling with recently. Imagine we want to write a program which displays a Twitter user's name. Not their @ handle, but their "real" name. For example, instead of @POTUS, display "President Obama". Easy, right? Not quite. What happens when a user is named "️"? N…
Continue reading →
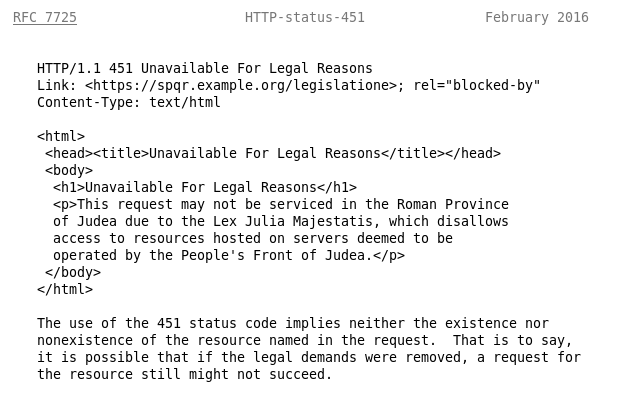
Friends, allow me to wallow in a little boasting! Four years ago, I made a modest proposal for a new HTTP Code to indicate censorship. A few days ago, RFC 7725: An HTTP Status Code to Report Legal Obstacles became an approved standard by the Internet Engineering Task Force. This allows a website, proxy, or ISP to explain to the user that the resource the user requested is unavailable for…
Continue reading →

I've just got a WiFi light switch. As I've explained previously, swapping out all my existing light bulbs with Smart Bulbs would be hugely expensive and has the disadvantage of not working when the switches are off at the wall. A WiFi light switch (theoretically) allows me to control the lights from my phone - and anyone else to use the physical buttons on the wall. That helps avoid this…
Continue reading →










