I don't particularly like picking on the security of Government websites. I do it a lot - but I always feel guilty about besmirching the good name of the many talented people who work in the Civil Service.
Today's flaw, however, is a particularly basic mistake which simply shouldn't be allowed to happen by any competent site owner.
What Is An Open Redirect?
A redirector is a small web service which takes the user to a new web page. It's a simple enough concept - if you visit:
http://www.planningportal.gov.uk/PpWeb/jsp/redirect.jsp?url=http://bbc.co.uk
you'll be taken to the BBC's homepage. It's an older technique which allows a website to track which external links you clicked on.
Unfortunately, this can be abused. Spammers can use links like:
http://GoodSite.com/?url=BadSite.com to trick people into visiting illegitimate web pages.
When those links are used in an email, it can help bypass spam filters. The presence of a .gov.uk domain adds the appearance of legitimacy to any phishing attempt.
Abuse of Open Redirects is perfect for phishing, spamming, trolling, and all manner of digital nastiness.
What Does It Look Like?
Here's the NSFW portion of the blog. Google crawls the web - and your emails - looking for links. When it finds them, it adds them to its search index. We can ask Google to give us all the results for the word X on website Y by performing a search for "X site:Y".
This lets us see all the times a UK Government site has been used to spew spam.
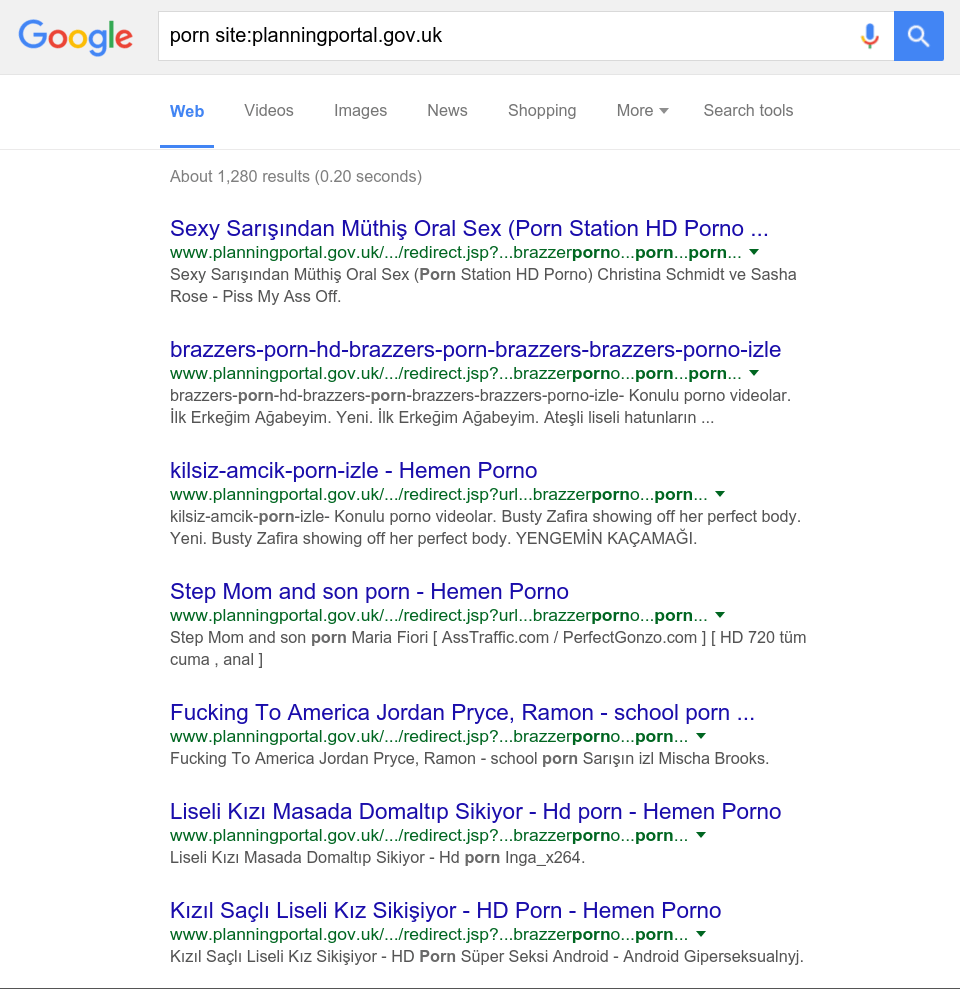
As a guess, the spammers have abused the open redirect and pasted those links on forums, in comments, and social media. Google dutifully follows and indexes them.
PlanningPortal.gov.uk is the only UK Government site which I could find which has this vulnerability. The US Government has vastly more sites with this particular problem - many of which seem to link to deeply disturbing content.
How to stop such wickedness?
There's an easy way, a hard way, and a pragmatic way to prevent this sort of vulnerability.
The easy way is - don't use a redirect service. If you want to link to an external website, just use a normal link. There really is limited use for them these days. Tracking can be accomplished by JavaScript analytics libraries without hijacking your user's browser.
The hard way is - create a whitelist of sites which can be linked through your redirect service. This is difficult because someone has to constantly maintain exactly which links are allowed through. You also have to manage which links are broken or are no longer acceptable.
If you absolutely need an open redirect and don't have the staffing levels to manage it, the pragmatic solution is this:

Final Thoughts
This isn't a new or innovative attack - Google have been warning about this vulnerability for the last 7 years!
Websites need constant care and maintenance against an evolving threat landscape. If a site contains such basic errors, I think it's reasonable to suspect that it is probably dangerously broken in other ways.
The UK Government should be holding GOV.UK website managers to a higher standard than this.