What a crazy weekend! I made the last minute decision to attend Rewired State's "National Hack The Government 2014" hackathon.
Rather than hack on any of the provided datasets, I wanted to work on an interesting way to present all the security flaws I had found in Government websites.
I teamed up with Mark, Marcello, and Orlando - together we created "Corkr - Plugging the Government's Digital Holes"

We were looking for different and interesting ways to visualise the data. Interactive infographics, space-trees, leader boards, top-trumps - all classic staples of hackdays.
In the end, we thought what would be the most visually impressive would be to present the sites on a map. That way we could show the scale of the problems - and let local authorities know where they needed to target.

It's hard to quantify just how bad the bugs are - is a single SQL Injection worse than two XSS flaws, for example - so we settled on just doing a raw count. Marcello and Orlando were able to convert the wpscan results files into JSON - which made doing the calculations a lot easier.
Mark, our graphics / UI guy came up with a really strong design to help showcase just how bad some of the problems are. We decided against revealing the nature of the vulnerabilities and instead went for a traffic light system.
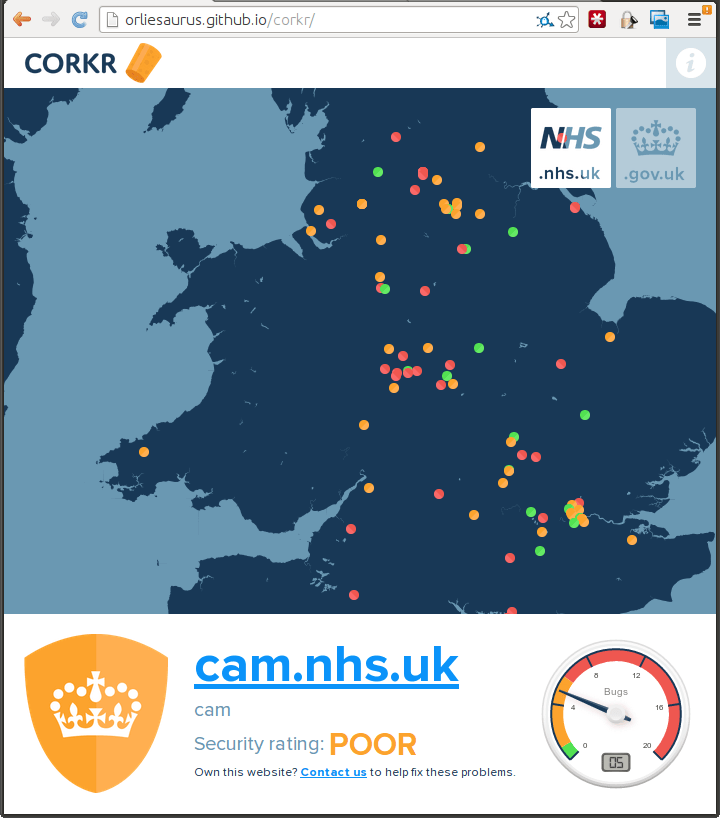
Using OpenStreetMap and LeafletJS meant it was incredibly easy to create lush looking maps which were zoomable. Adding markers to specific locations was also really easy.
Where In The Country Is A Website?
Some websites have a defined geographic location - a tiny Parish Council's website can reasonably be centred on a map.
The WHOIS data for *.gov.uk sites is not standardised. Very few of the sites spat out a Post Code when queried. Going to each website and looking for a "contact us" link was just too much work for a hackday - so we cheated!
Google has a pretty good API for getting the geographic location from a search query. So I manually converted all the domain names into something Google could use. For example "10downingstreet.gov.uk" became "10 downing street" (used as an example - it's not a vulnerable site).
Here's the PHP code:
PHP
$location = $argv[1]; $json = file_get_contents('https://maps.googleapis.com/maps/api/geocode/json?address='.$location.',%20uk&sensor=false'); $obj = json_decode($json, true); echo $obj["results"][0]["geometry"]["location"]["lat"] . ", " . $obj["results"][0]["geometry"]["location"]["lng"];
Now, obviously that requires a lot of copying and pasting. Luckily, Linux makes it very easy to automatically copy the output of a script onto the clipboard:
php -e locate.php West%20Byfleet | xclip -sel clip
And then we created a master JSON file which tallied up the number of flaws, where the sites were, and what they were named.
And then we did the same for the NHS sites!
In the end, due to time constraints, we only managed to get around 200 .gov.uk sites and 150 .nhs.uk sites.
And so, on very little sleep, we demo'd it...
The Competition
As ever with Rewired State, the standard of hacks was incredibly high. They ranged from the silly (dating MPs) to the serious (statistical comparisons of local areas). We presented towards the end, and were painfully aware of just how tough this was going to be. When you're up against a physicist using LIDAR calculated height data to infer shadow mapping and Pseudo-facial recognition using photoresistors, you know you're competing against the very best in the UK.
I am delighted to say that we were one of the four winners!










Some Thoughts On The Day
It was an absolutely amazing weekend. The food was good - and healthy - there was a wide range of people and some top notch government people there to talk with.
It might have been nice to have a bit more of a formal "what are people working on" session at the start. With 80ish hackers it may have taken some time, but it would have helped people introduce themselves and recruit for teams. All in all, a minor concern.
Prizes. I've written before about the corrupting influence of big money prizes. Luckily, the prizes on offer at #NHTG14 weren't jewel encrusted! About £30 - £40 worth of tech - plus some O’Reilly books. Just the right sort of level - not so extravagant that people would be gutted to lose, but expensive enough to make you go "Ooooh! What a lovely treat!".
Of course, the real value is in the taking part. And that's not just hokum; it really is.




For me, I think the real prize is making the government take notice and fix their broken sites. I think that is slowly happening - but a bit more on that later.
Congratulations to all the teams who took part - and many thanks to the judges for their impeccable taste.
What links here from around this blog?