New! Samsung Security Flaw - Disable Lockscreen - Total Control
I have discovered another security flaw in Samsung Android phones. It is possible to completely disable the lock screen and get access to any app - even when the phone is "securely" locked with a pattern, PIN, password, or face detection. Unlike another recently released flaw, this doesn't rely quite so heavily on ultra-precise timing.
Of course, if you are unable to download a screen unlocker, this security vulnerability still allows you to dial any phone number and run any app!
HOWTO
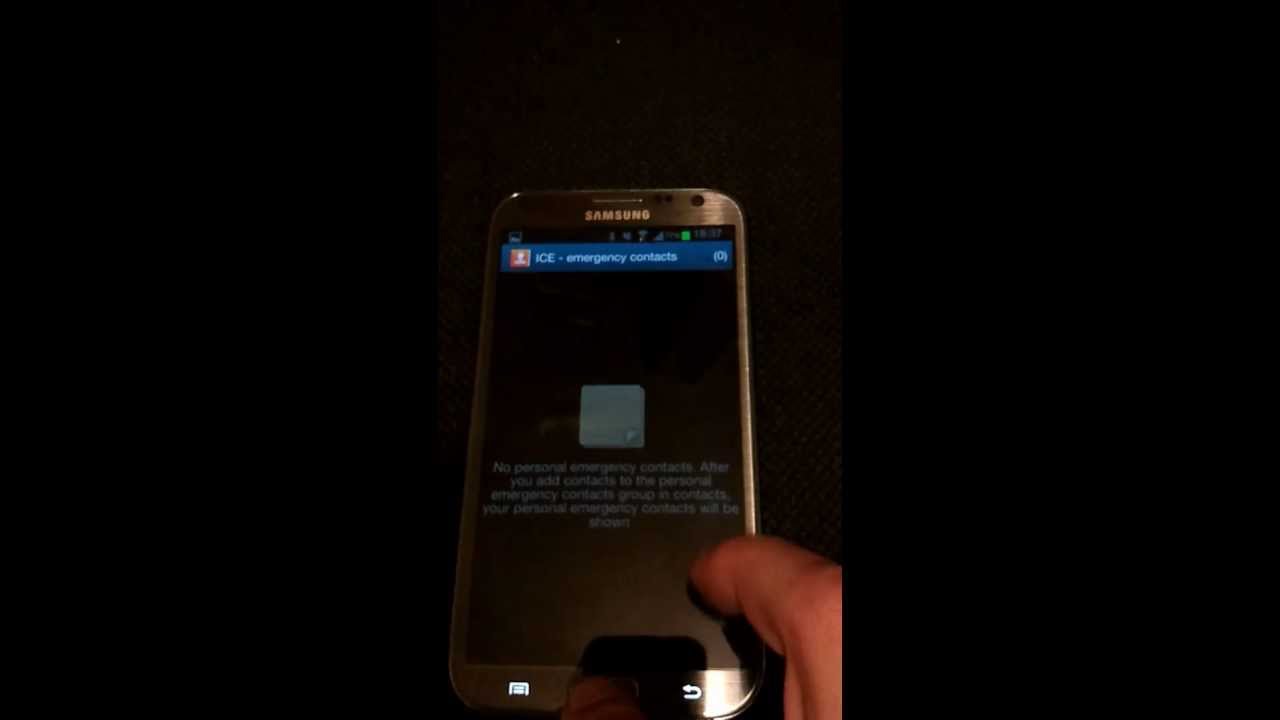
- From the lock screen, hit the emergency call button.
- Dial a non-existent emergency services number - e.g. 0.
- Press the green dial icon.
- Dismiss the error message.
- Press the phone's back button.
- The app's screen will be briefly displayed.
- This is just about long enough to interact with the app.
- Using this, you can run and interact with any app / widget / settings menu.
- You can also use this to launch the dialler.
- From there, you can dial any phone number (one digit at a time) and place a phone call.
- With Google Play, you can search for apps using the voice interface.
- You can download apps from the app store which will disable the screen lock.
Impact
This does not occur on stock Android from Google. This flaw only seems to be present on Samsung's version of Android. I have only tested it on a Galaxy Note II running 4.1.2 - I believe it should work on Samsung Galaxy SIII. It may work on other devices from Samsung.
My test phone was running 4.1.2 with the Touchwiz launcher from Samsung.
Defending Against This Attack
Until Samsung release a patch, the only way this can be defended against is by completely removing the Samsung firmware and replacing it with a 3rd party ROM.
This ROM for the Galaxy S III claims to have fixed the problem.
I'm sure there will be ROMs for other Galaxy devices in due course.
UPDATE 2013-03-20T16:54:12+00:00
YouTube user "bicecream88" has alerted me to a way to partially defend against this attack.
By disabling your screen animations, it is possible to reduce the amount of time the screen is displayed.
Settings -> Developer Options -> Window animation scale -> off
Repeat for Transition animation scale and Animator duration scale.
The vulnerability is still present - but you need to be a lot quicker in order to exploit it.
Responsible Disclosure
I reported this flaw to Samsung in late February. They are working on a patch which they assure me will be released shortly.
I have delayed public disclosure of this vulnerability. I also asked if they wanted me to delay publication until a patch was ready - however they declined this offer.
If you discover a security issue with Samsung's mobile products, I strongly encourage you to email m.security AT samsung.com
They will provide their PGP public key if you wish to ensure your communications with them are secure.
Thanks
My thanks to Thang Chien of Vietnam, who first demonstrated a variant of this flaw in January.
Thanks also to David Rogers, Marc Rogers, Alec Muffett, and Glyn Wintle for their wisdom and advice around the subject of responsible disclosure. Any faults with this disclosure are mine and mine alone.


 Two-Factor Authentication and the Police State
Two-Factor Authentication and the Police State
 Samsung's Bug Bounty
Samsung's Bug Bounty
 2013 - What a year!
2013 - What a year!
I can do this on my S3 running Android 4.1.2 as well. Bad samsung.
Doesn't work on my S3 (4.1.2), it just goes straight back to the lock screen. I can still get to the home screen via the ICE though.
Sort of works on my Note 1 N7000 int on stock JB.
Cant really do much with it, the screen changes too quick.
I. Did it on my s3 after hit ice contacts a few times holding down the home button it bypassed the lock screen all together and my phone unlocked and would not go back to lock screen
Bkav has just released a fix for this flaw: http://www.bkav.com/top-news/-/view_content/content/45560/bkav-releases-a-fix-for-new-lock-screen-flaw-on-samsung-phones